正在加载图片...
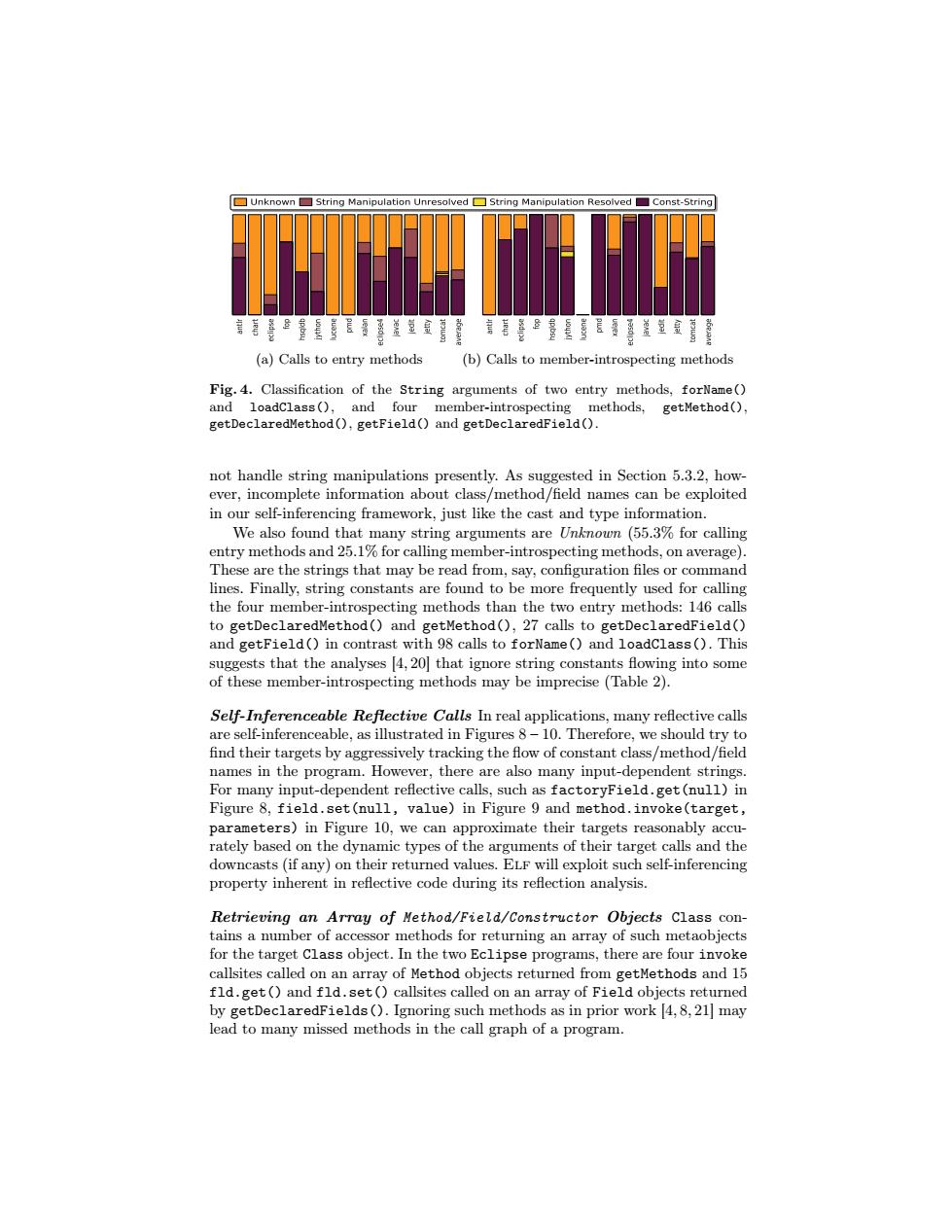
□Unknown☐String Manipulation Unresolved☐String Manipulatio Resolved Const-String 言复是8量复复屋爱是盖道宜警 (a)Calls to entry methods (b)Calls to member-introspecting methods Fig.4.Classification of the String arguments of two entry methods,forName() and loadclass(),and four member-introspecting methods,getMethod() getDeclaredMethod(),getField()and getDeclaredField(). not handle string manipulations presently.As suggested in Section 5.3.2,how- ever,incomplete information about class/method/field names can be exploited in our self-inferencing framework,just like the cast and type information. We also found that many string arguments are Unknown (55.3%for calling entry methods and 25.1%for calling member-introspecting methods,on average). These are the strings that may be read from,say,configuration files or command lines.Finally,string constants are found to be more frequently used for calling the four member-introspecting methods than the two entry methods:146 calls to getDeclaredMethod()and getMethod(),27 calls to getDeclaredField() and getField()in contrast with 98 calls to forName()and loadclass().This suggests that the analyses [4,20 that ignore string constants flowing into some of these member-introspecting methods may be imprecise(Table 2). Self-Inferenceable Reflective Calls In real applications,many reflective calls are self-inferenceable,as illustrated in Figures 8-10.Therefore,we should try to find their targets by aggressively tracking the flow of constant class/method/field names in the program.However,there are also many input-dependent strings. For many input-dependent reflective calls,such as factoryField.get(null)in Figure 8,field.set(null,value)in Figure 9 and method.invoke(target, parameters)in Figure 10,we can approximate their targets reasonably accu- rately based on the dynamic types of the arguments of their target calls and the downcasts(if any)on their returned values.ELF will exploit such self-inferencing property inherent in reflective code during its reflection analysis. Retrieving an Array of Method/Field/Constructor Objects Class con- tains a number of accessor methods for returning an array of such metaobjects for the target Class object.In the two Eclipse programs,there are four invoke callsites called on an array of Method objects returned from getMethods and 15 fld.get()and fld.set()callsites called on an array of Field objects returned by getDeclaredFields().Ignoring such methods as in prior work [4,8,21]may lead to many missed methods in the call graph of a program.antlr chart eclipse fop hsqldb jython lucene pmd xalan eclipse4 javac jedit jetty tomcat average antlr chart eclipse fop hsqldb jython lucene pmd xalan eclipse4 javac jedit jetty tomcat average Unknown String Manipulation Unresolved String Manipulation Resolved Const-String (a) Calls to entry methods (b) Calls to member-introspecting methods Fig. 4. Classification of the String arguments of two entry methods, forName() and loadClass(), and four member-introspecting methods, getMethod(), getDeclaredMethod(), getField() and getDeclaredField(). not handle string manipulations presently. As suggested in Section 5.3.2, however, incomplete information about class/method/field names can be exploited in our self-inferencing framework, just like the cast and type information. We also found that many string arguments are Unknown (55.3% for calling entry methods and 25.1% for calling member-introspecting methods, on average). These are the strings that may be read from, say, configuration files or command lines. Finally, string constants are found to be more frequently used for calling the four member-introspecting methods than the two entry methods: 146 calls to getDeclaredMethod() and getMethod(), 27 calls to getDeclaredField() and getField() in contrast with 98 calls to forName() and loadClass(). This suggests that the analyses [4, 20] that ignore string constants flowing into some of these member-introspecting methods may be imprecise (Table 2). Self-Inferenceable Reflective Calls In real applications, many reflective calls are self-inferenceable, as illustrated in Figures 8 – 10. Therefore, we should try to find their targets by aggressively tracking the flow of constant class/method/field names in the program. However, there are also many input-dependent strings. For many input-dependent reflective calls, such as factoryField.get(null) in Figure 8, field.set(null, value) in Figure 9 and method.invoke(target, parameters) in Figure 10, we can approximate their targets reasonably accurately based on the dynamic types of the arguments of their target calls and the downcasts (if any) on their returned values. Elf will exploit such self-inferencing property inherent in reflective code during its reflection analysis. Retrieving an Array of Method/Field/Constructor Objects Class contains a number of accessor methods for returning an array of such metaobjects for the target Class object. In the two Eclipse programs, there are four invoke callsites called on an array of Method objects returned from getMethods and 15 fld.get() and fld.set() callsites called on an array of Field objects returned by getDeclaredFields(). Ignoring such methods as in prior work [4, 8, 21] may lead to many missed methods in the call graph of a program