正在加载图片...
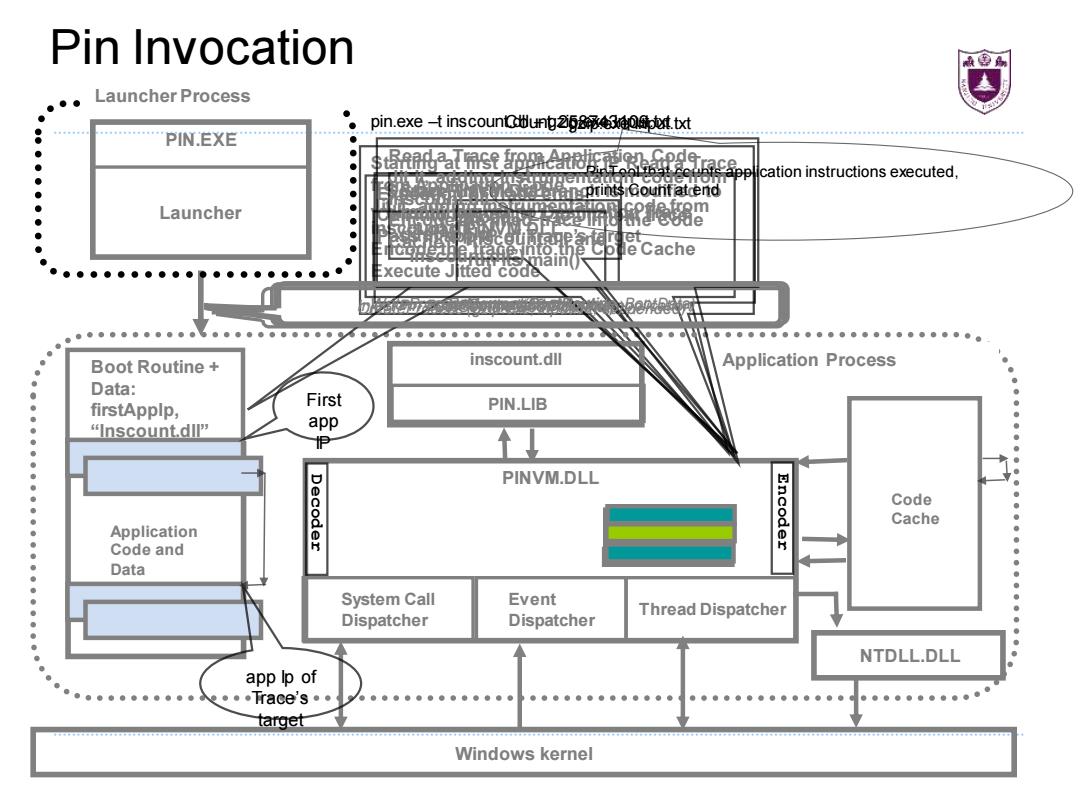
Pin Invocation Launcher Process ● ● pin.exe -t inscountung26830pt.txt 8 PIN.EXE ● ● ● cation instructions executed, ● ● 上ncprints Gountatcend ● Launcher the eude ● et ● ● icode the into.the Coue Cache ●●●●●●●● kecute Jltfed code Boot Routine inscount.dll Application Process Data: ● First firstApplp, PIN.LIB “nscount.dlI app ● PINVM.DLL Decoder Encoder Code Cache ● Application ● Code and Data ● ● ● System Call Event Thread Dispatcher Dispatcher Dispatcher NTDLL.DLL app lp of 。●.Trace's。● target Windows kernelStarting at first application IP Read a Trace from Application Code Jit it, adding instrumentation code from inscount.dll Encode the trace into the Code Cache Execute Jitted code Execution of Trace ends Call into PINVM.DLL to Jit next trace Pass in app IP of Trace’s target Source Trace exit branch is modified to directly branch to Destination Trace Pin Invocation gzip.exe input.txt Application Code and Data Application Process System Call Dispatcher Event Dispatcher Thread Dispatcher PINVM.DLL inscount.dll PIN.LIB Code Cache NTDLL.DLL Windows kernel CreateProcess (gzip.exe, input.txt, suspended) Launcher PIN.EXE Launcher Process Boot Routine + Data: firstAppIp, “Inscount.dll” Load PINVM.DLL Inject Pin BootRoutine and Data into application Load inscount.dll and run its main() Start PINVM.DLL running (firstAppIp, “inscount.dll”) pin.exe –t inscount.dll Count 258743109 – gzip.exe input.txt PinTool that counts application instructions executed, prints Count at end Resume at BootRoutine First app IP app Ip of Trace’s target Read a Trace from Application Code Jit it, adding instrumentation code from inscount.dll Encode the jitted trace into the Code Cache WriteProcessMemory(BootRoutine, BootData) SetContext(BootRoutineIp) GetContext(&firstAppIp) Decoder Encoder