正在加载图片...
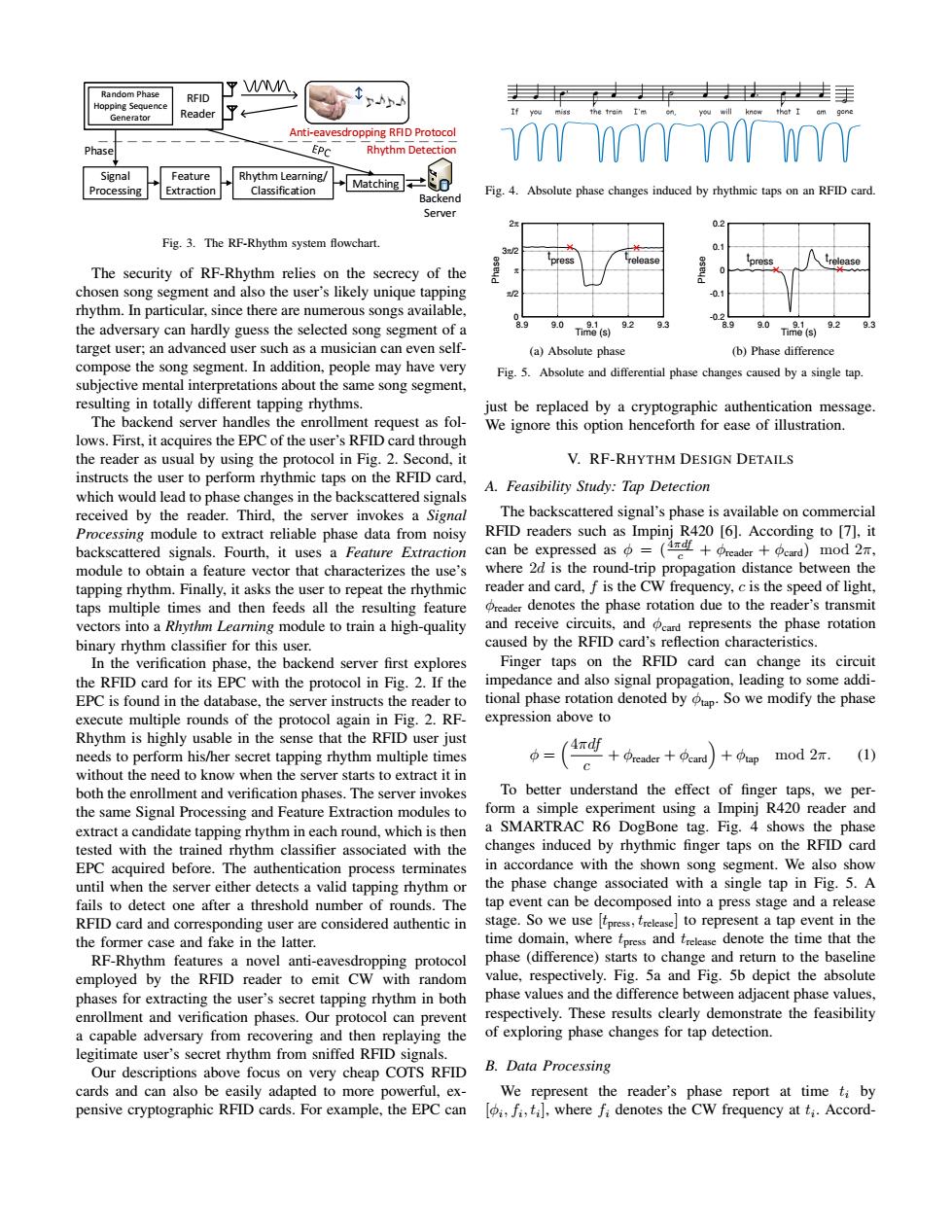
Random phase 了WM RFID opping Sequence Generator Reader Anti-eavesdropping RFID Protocol Phase EPC Rhythm Detection Signal Feature Rhythm Learning/ Processing Matching Extraction Classification Fig.4.Absolute phase changes induced by rhythmic taps on an RFID card. Backend Server 2 02 Fig.3.The RF-Rhythm system flowchart. 0.1 ease The security of RF-Rhythm relies on the secrecy of the chosen song segment and also the user's likely unique tapping -0.1 rhythm.In particular,since there are numerous songs available, 0 the adversary can hardly guess the selected song segment of a 9.0 Time (s) 92 9.3 8.9 9.0 9.2 9.3 target user;an advanced user such as a musician can even self- (a)Absolute phase (b)Phase difference compose the song segment.In addition,people may have very Fig.5.Absolute and differential phase changes caused by a single tap. subjective mental interpretations about the same song segment, resulting in totally different tapping rhythms. just be replaced by a cryptographic authentication message. The backend server handles the enrollment request as fol- We ignore this option henceforth for ease of illustration. lows.First,it acquires the EPC of the user's RFID card through the reader as usual by using the protocol in Fig.2.Second,it V.RF-RHYTHM DESIGN DETAILS instructs the user to perform rhythmic taps on the RFID card, A.Feasibility Study:Tap Detection which would lead to phase changes in the backscattered signals received by the reader.Third,the server invokes a Signal The backscattered signal's phase is available on commercial Processing module to extract reliable phase data from noisy RFID readers such as Impinj R420 [6].According to [7],it backscattered signals.Fourth,it uses a Feature Extraction can be expressed as(+rader+cd)mod 2 module to obtain a feature vector that characterizes the use's where 2d is the round-trip propagation distance between the tapping rhythm.Finally,it asks the user to repeat the rhythmic reader and card,f is the CW frequency,cis the speed of light, taps multiple times and then feeds all the resulting feature dreader denotes the phase rotation due to the reader's transmit vectors into a Rhythm Learning module to train a high-quality and receive circuits,and card represents the phase rotation binary rhythm classifier for this user. caused by the RFID card's reflection characteristics. In the verification phase,the backend server first explores Finger taps on the RFID card can change its circuit the RFID card for its EPC with the protocol in Fig.2.If the impedance and also signal propagation,leading to some addi- EPC is found in the database,the server instructs the reader to tional phase rotation denoted by tap So we modify the phase execute multiple rounds of the protocol again in Fig.2.RF- expression above to Rhythm is highly usable in the sense that the RFID user just needs to perform his/her secret tapping rhythm multiple times (ddd+upmod 2. (1) 、c without the need to know when the server starts to extract it in both the enrollment and verification phases.The server invokes To better understand the effect of finger taps,we per- the same Signal Processing and Feature Extraction modules to form a simple experiment using a Impinj R420 reader and extract a candidate tapping rhythm in each round,which is then a SMARTRAC R6 DogBone tag.Fig.4 shows the phase tested with the trained rhythm classifier associated with the changes induced by rhythmic finger taps on the RFID card EPC acquired before.The authentication process terminates in accordance with the shown song segment.We also show until when the server either detects a valid tapping rhythm or the phase change associated with a single tap in Fig.5.A fails to detect one after a threshold number of rounds.The tap event can be decomposed into a press stage and a release RFID card and corresponding user are considered authentic in stage.So we use [tpress,trelease]to represent a tap event in the the former case and fake in the latter. time domain,where tpress and trelease denote the time that the RF-Rhythm features a novel anti-eavesdropping protocol phase (difference)starts to change and return to the baseline employed by the RFID reader to emit CW with random value,respectively.Fig.5a and Fig.5b depict the absolute phases for extracting the user's secret tapping rhythm in both phase values and the difference between adjacent phase values, enrollment and verification phases.Our protocol can prevent respectively.These results clearly demonstrate the feasibility a capable adversary from recovering and then replaying the of exploring phase changes for tap detection. legitimate user's secret rhythm from sniffed RFID signals. Our descriptions above focus on very cheap COTS RFID B.Data Processing cards and can also be easily adapted to more powerful,ex- We represent the reader's phase report at time ti by pensive cryptographic RFID cards.For example,the EPC can fi,ti],where fi denotes the CW frequency atti.Accord-Feature Extraction Rhythm Learning/ Classification Matching Rhythm Detection Anti-eavesdropping RFID Protocol Signal Processing Random Phase Hopping Sequence Generator RFID Reader Random Phase Hopping Sequence Generator RFID Reader Random Phase Hopping Sequence Generator RFID Reader Backend Server Phase Fig. 3. The RF-Rhythm system flowchart. The security of RF-Rhythm relies on the secrecy of the chosen song segment and also the user’s likely unique tapping rhythm. In particular, since there are numerous songs available, the adversary can hardly guess the selected song segment of a target user; an advanced user such as a musician can even selfcompose the song segment. In addition, people may have very subjective mental interpretations about the same song segment, resulting in totally different tapping rhythms. The backend server handles the enrollment request as follows. First, it acquires the EPC of the user’s RFID card through the reader as usual by using the protocol in Fig. 2. Second, it instructs the user to perform rhythmic taps on the RFID card, which would lead to phase changes in the backscattered signals received by the reader. Third, the server invokes a Signal Processing module to extract reliable phase data from noisy backscattered signals. Fourth, it uses a Feature Extraction module to obtain a feature vector that characterizes the use’s tapping rhythm. Finally, it asks the user to repeat the rhythmic taps multiple times and then feeds all the resulting feature vectors into a Rhythm Learning module to train a high-quality binary rhythm classifier for this user. In the verification phase, the backend server first explores the RFID card for its EPC with the protocol in Fig. 2. If the EPC is found in the database, the server instructs the reader to execute multiple rounds of the protocol again in Fig. 2. RFRhythm is highly usable in the sense that the RFID user just needs to perform his/her secret tapping rhythm multiple times without the need to know when the server starts to extract it in both the enrollment and verification phases. The server invokes the same Signal Processing and Feature Extraction modules to extract a candidate tapping rhythm in each round, which is then tested with the trained rhythm classifier associated with the EPC acquired before. The authentication process terminates until when the server either detects a valid tapping rhythm or fails to detect one after a threshold number of rounds. The RFID card and corresponding user are considered authentic in the former case and fake in the latter. RF-Rhythm features a novel anti-eavesdropping protocol employed by the RFID reader to emit CW with random phases for extracting the user’s secret tapping rhythm in both enrollment and verification phases. Our protocol can prevent a capable adversary from recovering and then replaying the legitimate user’s secret rhythm from sniffed RFID signals. Our descriptions above focus on very cheap COTS RFID cards and can also be easily adapted to more powerful, expensive cryptographic RFID cards. For example, the EPC can Fig. 4. Absolute phase changes induced by rhythmic taps on an RFID card. 0 π/2 π 3π/2 2π 8.9 9.0 9.1 9.2 9.3 tpress t release Phase Time (s) (a) Absolute phase -0.2 -0.1 0 0.1 0.2 8.9 9.0 9.1 9.2 9.3 tpress t release Phase Time (s) (b) Phase difference Fig. 5. Absolute and differential phase changes caused by a single tap. just be replaced by a cryptographic authentication message. We ignore this option henceforth for ease of illustration. V. RF-RHYTHM DESIGN DETAILS A. Feasibility Study: Tap Detection The backscattered signal’s phase is available on commercial RFID readers such as Impinj R420 [6]. According to [7], it can be expressed as φ = ( 4πdf c + φreader + φcard) mod 2π, where 2d is the round-trip propagation distance between the reader and card, f is the CW frequency, c is the speed of light, φreader denotes the phase rotation due to the reader’s transmit and receive circuits, and φcard represents the phase rotation caused by the RFID card’s reflection characteristics. Finger taps on the RFID card can change its circuit impedance and also signal propagation, leading to some additional phase rotation denoted by φtap. So we modify the phase expression above to φ = 4πdf c + φreader + φcard + φtap mod 2π. (1) To better understand the effect of finger taps, we perform a simple experiment using a Impinj R420 reader and a SMARTRAC R6 DogBone tag. Fig. 4 shows the phase changes induced by rhythmic finger taps on the RFID card in accordance with the shown song segment. We also show the phase change associated with a single tap in Fig. 5. A tap event can be decomposed into a press stage and a release stage. So we use [tpress, trelease] to represent a tap event in the time domain, where tpress and trelease denote the time that the phase (difference) starts to change and return to the baseline value, respectively. Fig. 5a and Fig. 5b depict the absolute phase values and the difference between adjacent phase values, respectively. These results clearly demonstrate the feasibility of exploring phase changes for tap detection. B. Data Processing We represent the reader’s phase report at time ti by [φi , fi , ti ], where fi denotes the CW frequency at ti . Accord-