正在加载图片...
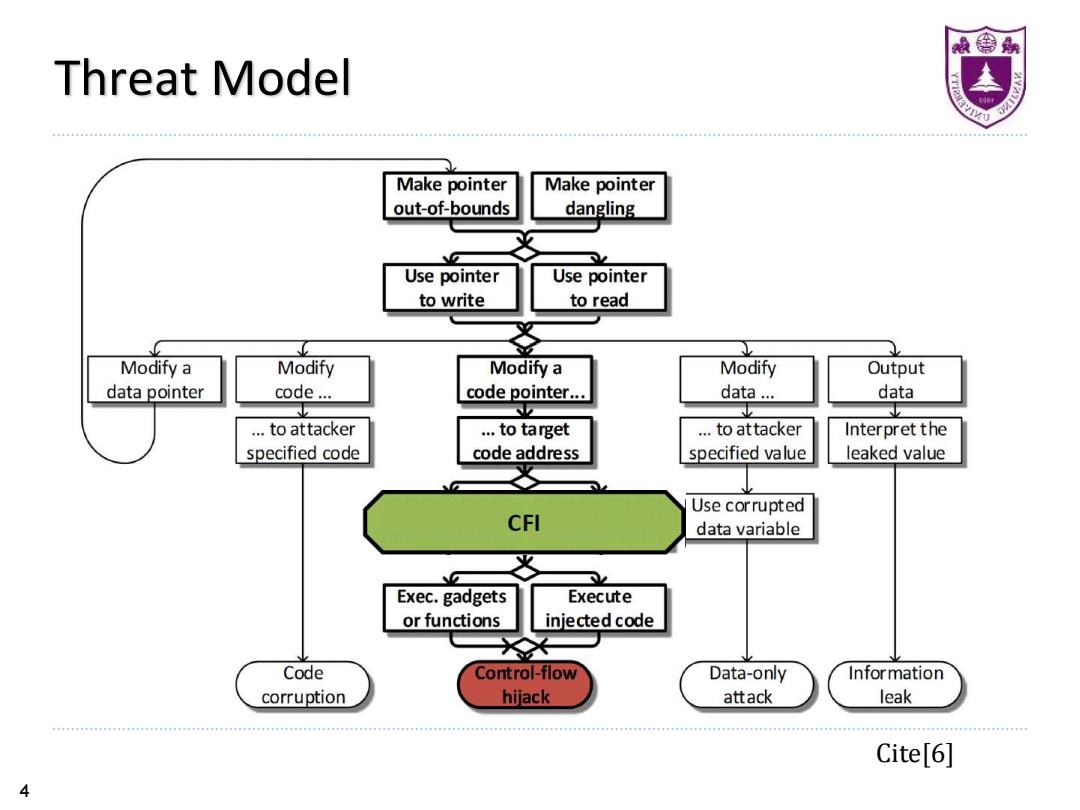
最鲁 Threat Model Make pointer Make pointer out-of-bounds dangling Use pointer Use pointer to write to read Modify a Modify Modify a Modify Output data pointer code... code pointer... data... data …to attacker ..to target ..to attacker Interpret the specified code code address specified value leaked value Use corrupted CFI data variable Exec.gadgets Execute or functions injected code Code Control-flow Data-only Information corruption hijack attack leak Cite[6] 44 Threat Model Cite[6]