正在加载图片...
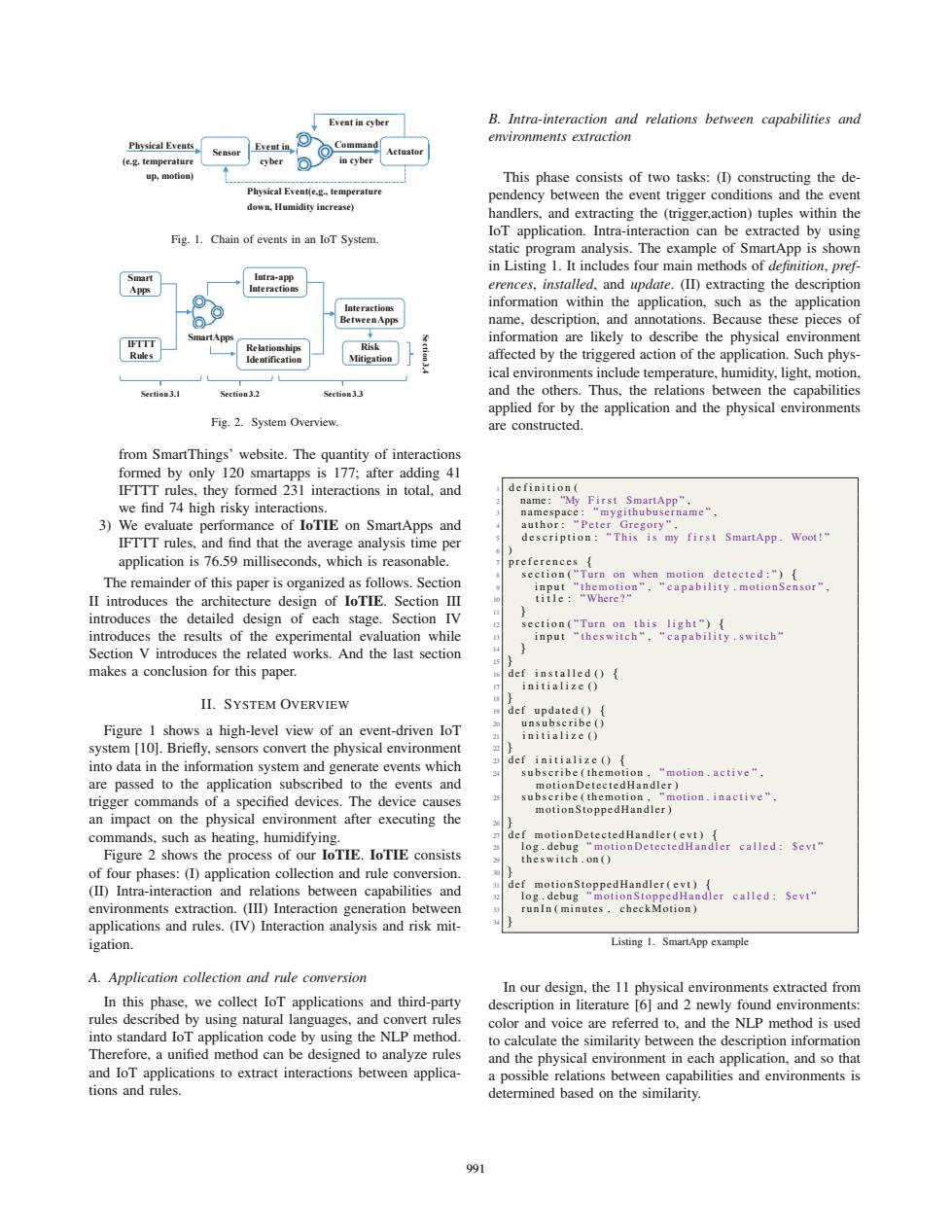
Event in cyber B.Intra-interaction and relations between capabilities and environments extraction Physical Events 、Command Sensor Event in (e.g.temperature cyber in cyher up,motion) This phase consists of two tasks:(I)constructing the de- Physical Event(e.g,temperature pendency between the event trigger conditions and the event down,Humidity increase) handlers,and extracting the (trigger,action)tuples within the Fig.1.Chain of events in an loT System. IoT application.Intra-interaction can be extracted by using static program analysis.The example of SmartApp is shown in Listing 1.It includes four main methods of definition,pref Intra-app Interactions erences,installed,and update.(II)extracting the description Interactions information within the application,such as the application BetweenApps name,description,and annotations.Because these pieces of IXMN information are likely to describe the physical environment Risk Rules Identification Mitigation affected by the triggered action of the application.Such phys- ical environments include temperature,humidity,light,motion, Section3.2 and the others.Thus,the relations between the capabilities applied for by the application and the physical environments Fig.2.System Overview. are constructed. from SmartThings'website.The quantity of interactions formed by only 120 smartapps is 177;after adding 41 IFTTT rules,they formed 231 interactions in total,and definition( we find 74 high risky interactions. name:"My First SmartApp" namespace "mygithubusername", 3)We evaluate performance of IoTIE on SmartApps and author:"Peter Gregory". IFTTT rules,and find that the average analysis time per description:"This is my first SmartApp.Woot!" application is 76.59 milliseconds,which is reasonable. preferences section("Turn on when motion detected:") The remainder of this paper is organized as follows.Section input "themotion"."capability.motionSensor". II introduces the architecture design of IoTIE.Section III title:"Where?" introduces the detailed design of each stage.Section IV section("Turn on this light"){ introduces the results of the experimental evaluation while input "theswitch"."capability.switch" Section V introduces the related works.And the last section makes a conclusion for this paper. def installed ( initialize() II.SYSTEM OVERVIEW def updated()f unsubscribe() Figure I shows a high-level view of an event-driven IoT initialize() system [10].Briefly,sensors convert the physical environment into data in the information system and generate events which def initialize ( subscribe(themotion. “motion.active“ are passed to the application subscribed to the events and motionDetectedHandler) trigger commands of a specified devices.The device causes subscribe(themotion,"motion.inactive". an impact on the physical environment after executing the motionStoppedHandler) commands,such as heating,humidifying. motionDetectedHandler(evt) Figure 2 shows the process of our IoTIE.IoTIE consists log.debug "motionDetectedHandler called:Sevt" theswitch.on() of four phases:(I)application collection and rule conversion. (II)Intra-interaction and relations between capabilities and def motionStoppedHandler(evt){ log.debug "motionStoppedHandier called:Sevt" environments extraction.(III)Interaction generation between runIn(minutes.checkMotion) applications and rules.(IV)Interaction analysis and risk mit- igation. Listing 1.SmartApp cxample A.Application collection and rule conversion In our design,the 11 physical environments extracted from In this phase,we collect IoT applications and third-party description in literature [6]and 2 newly found environments: rules described by using natural languages,and convert rules color and voice are referred to,and the NLP method is used into standard IoT application code by using the NLP method. to calculate the similarity between the description information Therefore,a unified method can be designed to analyze rules and the physical environment in each application,and so that and loT applications to extract interactions between applica- a possible relations between capabilities and environments is tions and rules. determined based on the similarity. 9916HQVRU $FWXDWRU (YHQWLQ F\EHU &RPPDQG LQF\EHU (YHQWLQF\EHU 3K\VLFDO(YHQW
HJWHPSHUDWXUH GRZQ+XPLGLW\LQFUHDVH
3K\VLFDO(YHQWV
HJWHPSHUDWXUH XSPRWLRQ
Fig. 1. Chain of events in an IoT System. ,)777 5XOHV 6PDUW$SSV ,QWUDDSS ,QWHUDFWLRQV 5HODWLRQVKLSV ,GHQWLILFDWLRQ 6PDUW $SSV ,QWHUDFWLRQV %HWZHHQ$SSV 6HFWLRQ 6HFWLRQ 6HFWLRQ 5LVN 0LWLJDWLRQ 6HFWLRQ Fig. 2. System Overview. from SmartThings’ website. The quantity of interactions formed by only 120 smartapps is 177; after adding 41 IFTTT rules, they formed 231 interactions in total, and we find 74 high risky interactions. 3) We evaluate performance of IoTIE on SmartApps and IFTTT rules, and find that the average analysis time per application is 76.59 milliseconds, which is reasonable. The remainder of this paper is organized as follows. Section II introduces the architecture design of IoTIE. Section III introduces the detailed design of each stage. Section IV introduces the results of the experimental evaluation while Section V introduces the related works. And the last section makes a conclusion for this paper. II. SYSTEM OVERVIEW Figure 1 shows a high-level view of an event-driven IoT system [10]. Briefly, sensors convert the physical environment into data in the information system and generate events which are passed to the application subscribed to the events and trigger commands of a specified devices. The device causes an impact on the physical environment after executing the commands, such as heating, humidifying. Figure 2 shows the process of our IoTIE. IoTIE consists of four phases: (I) application collection and rule conversion. (II) Intra-interaction and relations between capabilities and environments extraction. (III) Interaction generation between applications and rules. (IV) Interaction analysis and risk mitigation. A. Application collection and rule conversion In this phase, we collect IoT applications and third-party rules described by using natural languages, and convert rules into standard IoT application code by using the NLP method. Therefore, a unified method can be designed to analyze rules and IoT applications to extract interactions between applications and rules. B. Intra-interaction and relations between capabilities and environments extraction This phase consists of two tasks: (I) constructing the dependency between the event trigger conditions and the event handlers, and extracting the (trigger,action) tuples within the IoT application. Intra-interaction can be extracted by using static program analysis. The example of SmartApp is shown in Listing 1. It includes four main methods of definition, preferences, installed, and update. (II) extracting the description information within the application, such as the application name, description, and annotations. Because these pieces of information are likely to describe the physical environment affected by the triggered action of the application. Such physical environments include temperature, humidity, light, motion, and the others. Thus, the relations between the capabilities applied for by the application and the physical environments are constructed. 1 definition ( 2 name : ”My F i r s t SmartApp ” , 3 namespace : ”mygithubusername” , 4 author : ” Peter Gregory” , 5 description : ” T hi s i s my f i r s t SmartApp . Woot ! ” 6 ) 7 preferences { 8 section ( ” Turn on when motion d et e ct e d : ” ) { 9 input ”themotion” , ” capability . motionSensor” , 10 title : ”Where?” 11 } 12 section ( ”Turn on t hi s li g ht ” ) { 13 input ”theswitch” , ” capability . switch” 14 } 15 } 16 def installed () { 17 initialize () 18 } 19 def updated () { 20 unsubscribe () 21 initialize () 22 } 23 def initialize () { 24 subscribe (themotion , ”motion . active ” , motionDetectedHandler ) 25 subscribe (themotion , ”motion . inactive ” , motionStoppedHandler ) 26 } 27 def motionDetectedHandler ( evt ) { 28 log . debug ”motionDetectedHandler called : $evt” 29 theswitch . on ( ) 30 } 31 def motionStoppedHandler ( evt ) { 32 log . debug ”motionStoppedHandler called : $evt” 33 runIn ( minutes , checkMotion ) 34 } Listing 1. SmartApp example In our design, the 11 physical environments extracted from description in literature [6] and 2 newly found environments: color and voice are referred to, and the NLP method is used to calculate the similarity between the description information and the physical environment in each application, and so that a possible relations between capabilities and environments is determined based on the similarity. 991��������������������