正在加载图片...
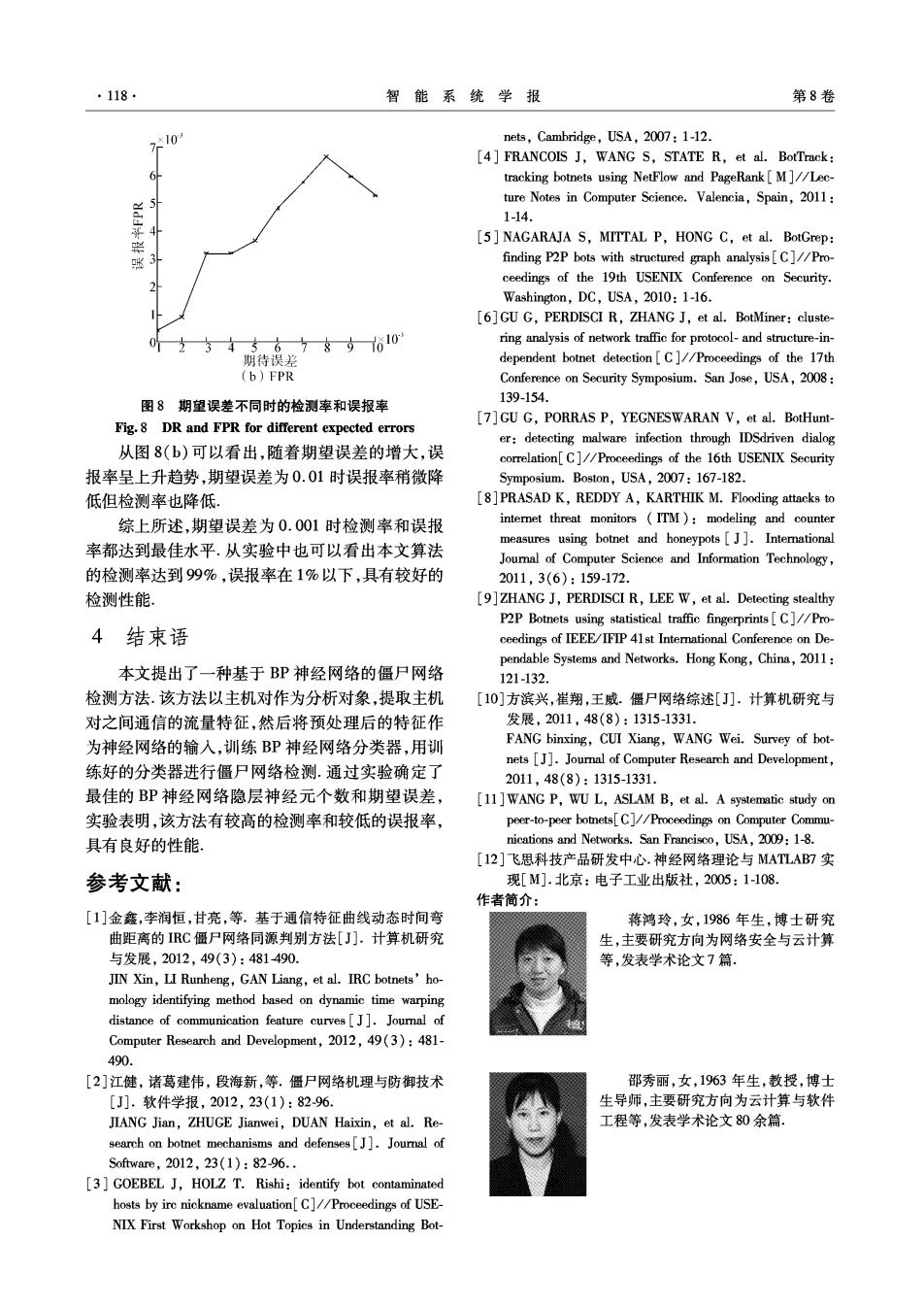
118 智能系统学报 第8卷 ,×10 nets,Cambridge,USA,2007:1-12. [4]FRANCOIS J,WANG S,STATE R,et al.BotTrack: tracking botnets using NetFlow and PageRank[M]//Lec- ture Notes in Computer Science.Valencia,Spain,2011: 1-14. [5]NAGARAJA S,MITTAL P,HONG C,et al.BotGrep: 好 finding P2P bots with structured graph analysis[C]//Pro- ceedings of the 19th USENIX Conference on Security. Washington,DC,USA,2010:1-16. [6]GU G,PERDISCI R,ZHANG J,et al.BotMiner:cluste- 234367896101 ring analysis of network traffic for protocol-and structure-in- 期待误差 dependent botnet detection[C]//Proceedings of the 17th (b)FPR Conference on Security Symposium.San Jose,USA,2008: 139-154. 图8期望误差不同时的检测率和误报率 Fig.8 DR and FPR for different expected errors [7]GU G,PORRAS P,YEGNESWARAN V,et al.BotHunt- er:detecting malware infection through IDSdriven dialog 从图8(b)可以看出,随着期望误差的增大,误 correlation[C]//Proceedings of the 16th USENIX Security 报率呈上升趋势,期望误差为0.01时误报率稍微降 Symposium.Boston,USA,2007:167-182. 低但检测率也降低。 [8]PRASAD K,REDDY A,KARTHIK M.Flooding attacks to 综上所述,期望误差为0.001时检测率和误报 internet threat monitors ITM )modeling and counter measures using botnet and honeypots[J].International 率都达到最佳水平.从实验中也可以看出本文算法 Journal of Computer Science and Information Technology, 的检测率达到99%,误报率在1%以下,具有较好的 2011,3(6):159-172. 检测性能 [9]ZHANG J,PERDISCI R,LEE W,et al.Detecting stealthy P2P Botnets using statistical traffic fingerprints[C]//Pro 4结束语 ceedings of IEEE/IFIP 41st Intemational Conference on De- pendable Systems and Networks.Hong Kong,China,2011: 本文提出了一种基于BP神经网络的僵尸网络 121132 检测方法.该方法以主机对作为分析对象,提取主机 [10]方滨兴,崔翔,王威.僵尸网络综述[J].计算机研究与 对之间通信的流量特征,然后将预处理后的特征作 发展,2011,48(8):1315-1331. 为神经网络的输入,训练BP神经网络分类器,用训 FANG binxing,CUI Xiang,WANG Wei.Survey of bot- nets [J].Journal of Computer Research and Development, 练好的分类器进行僵尸网络检测.通过实验确定了 2011,48(8):1315-1331. 最佳的BP神经网络隐层神经元个数和期望误差, [11]WANG P,WU L,ASLAM B,et al.A systematic study on 实验表明,该方法有较高的检测率和较低的误报率, peer-to-peer botnets[C]//Proceedings on Computer Commu- 具有良好的性能, nications and Networks.San Francisco,USA,2009:1-8. [12]飞思科技产品研发中心.神经网络理论与MATLAB7实 参考文献: 现[M].北京:电子工业出版社,2005:1108. 作者简介: [1]金鑫,李润恒,甘亮,等.基于通信特征曲线动态时间弯 蒋鸿玲,女,1986年生,博士研究 曲距离的IRC僵尸网同源判别方法[J].计算机研究 生,主要研究方向为网络安全与云计算 与发展,2012,49(3):481490. 等,发表学术论文7篇. JIN Xin,LI Runheng,GAN Liang,et al.IRC botnets'ho- mology identifying method based on dynamic time warping distance of communication feature curves[J].Journal of Computer Research and Development,2012,49(3):481- 490. [2]江健,诸葛建伟,段海新,等.僵尸网络机理与防御技术 邵秀丽,女,1963年生,教授,博士 [J].软件学报,2012,23(1):8296. 生导师,主要研究方向为云计算与软件 JIANG Jian,ZHUGE Jianwei,DUAN Haixin,et al.Re- 工程等,发表学术论文80余篇. search on botnet mechanisms and defenses[].Joumal of Software,2012,23(1):82-96.. [3]GOEBEL J,HOLZ T.Rishi:identify bot contaminated hosts by ire nickname evaluation[C]//Proceedings of USE NIX First Workshop on Hot Topics in Understanding Bot-