正在加载图片...
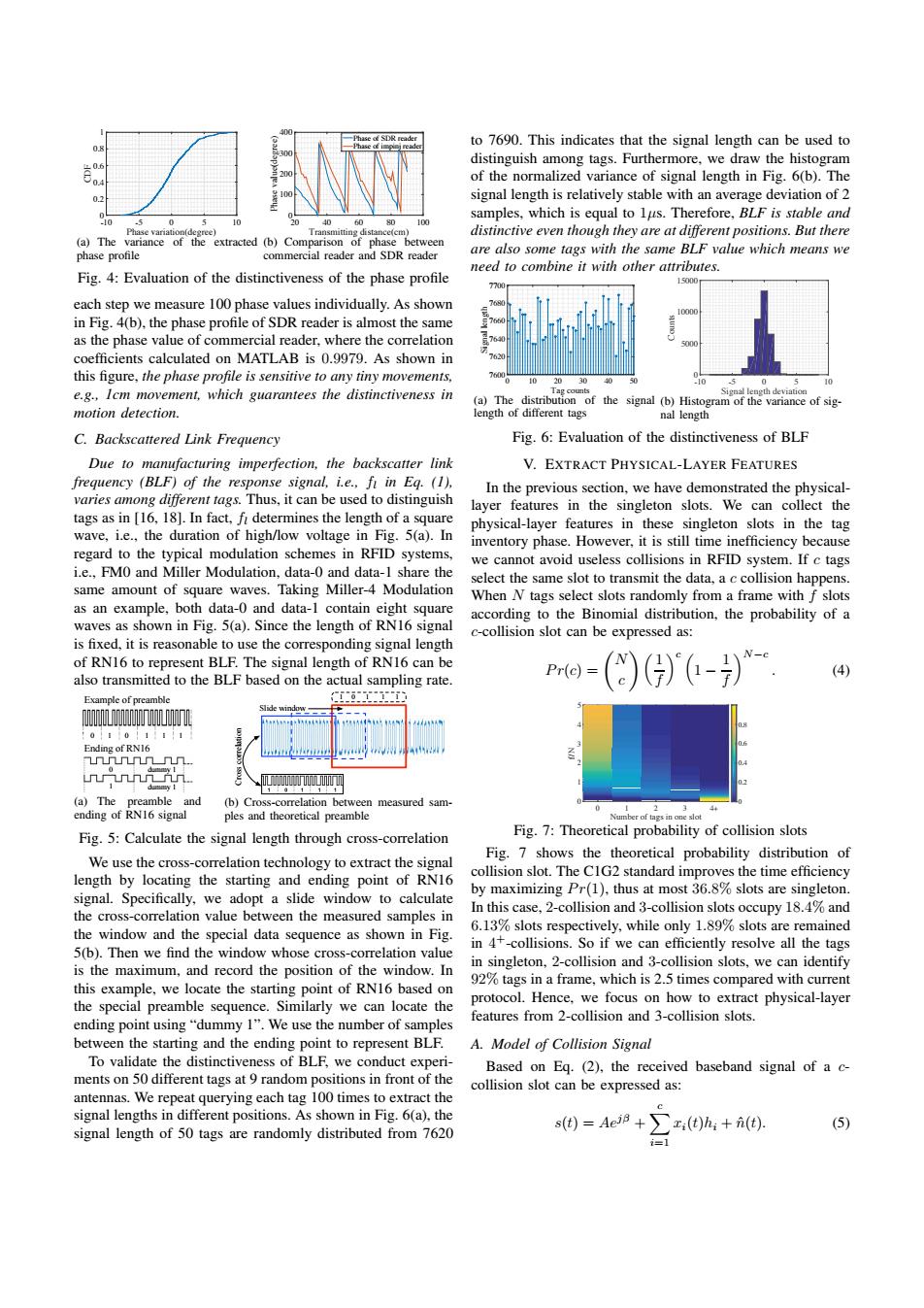
to 7690.This indicates that the signal length can be used to distinguish among tags.Furthermore,we draw the histogram of the normalized variance of signal length in Fig.6(b).The 0.2 signal length is relatively stable with an average deviation of 2 samples,which is equal to lus.Therefore,BLF is stable and 10 (a)The distinctive even though they are at different positions.But there the extracted (b)Comp arison of hase between phase profile commercial reader and SDR reader are also some tags with the same BLF value which means we need to combine it with other attributes. Fig.4:Evaluation of the distinctiveness of the phase profile 770 1500 each step we measure 100 phase values individually.As shown in Fig.4(b),the phase profile of SDR reader is almost the same as the phase value of commercial reader,where the correlation coefficients calculated on MATLAB is 0.9979.As shown in this figure,the phase profile is sensitive to any tiny movements, 20 e.g.,Icm movement,which guarantees the distinctiveness in (a) The distribution of the signal (b)Histogram of of sig- motion detection. length of different tags nal length C.Backscattered Link Frequency Fig.6:Evaluation of the distinctiveness of BLF Due to manufacturing imperfection,the backscatter link V.EXTRACT PHYSICAL-LAYER FEATURES frequency (BLF)of the response signal,i.e.,f in Eg.(1). In the previous section,we have demonstrated the physical- varies among different tags.Thus,it can be used to distinguish layer features in the singleton slots.We can collect the tags as in [16,18].In fact,f determines the length of a square physical-layer features in these singleton slots in the tag wave,i.e.,the duration of high/low voltage in Fig.5(a).In inventory phase.However,it is still time inefficiency because regard to the typical modulation schemes in RFID systems, we cannot avoid useless collisions in RFID system.If c tags i.e.,FMO and Miller Modulation.data-0 and data-1 share the same amount of square waves.Taking Miller-4 Modulation select the same slot to transmit the data,a c collision happens. When N tags select slots randomly from a frame with f slots as an example,both data-0 and data-1 contain eight square according to the Binomial distribution,the probability of a waves as shown in Fig.5(a).Since the length of RN16 signal c-collision slot can be expressed as: is fixed,it is reasonable to use the corresponding signal length of RN16 to represent BLF.The signal length of RN16 can be (4) also transmitted to the BLF based on the actual sampling rate. Pr(c)= Example of preamble 6T11 01101111 Ending of RN16 风 (a)The preamble and (b)Cross-correlation between measured sam- 0 44 ending of RN16 signal ples and theoretical preamble Number of tags in one slot Fig.5:Calculate the signal length through cross-correlation Fig.7:Theoretical probability of collision slots We use the cross-correlation technology to extract the signal Fig.7 shows the theoretical probability distribution of length by locating the starting and ending point of RN16 collision slot.The C1G2 standard improves the time efficiency by maximizing Pr(1),thus at most 36.8%slots are singleton signal.Specifically,we adopt a slide window to calculate In this case,2-collision and 3-collision slots occupy 18.4%and the cross-correlation value between the measured samples in the window and the special data sequence as shown in Fig. 6.13%slots respectively,while only 1.89%slots are remained 5(b).Then we find the window whose cross-correlation value in 4+-collisions.So if we can efficiently resolve all the tags in singleton,2-collision and 3-collision slots,we can identify is the maximum,and record the position of the window.In this example,we locate the starting point of RN16 based on 92%tags in a frame,which is 2.5 times compared with current the special preamble sequence.Similarly we can locate the protocol.Hence,we focus on how to extract physical-layer ending point using"dummy 1".We use the number of samples features from 2-collision and 3-collision slots between the starting and the ending point to represent BLF. A.Model of Collision Signal To validate the distinctiveness of BLF,we conduct experi- Based on Eq.(2),the received baseband signal of a c- ments on 50 different tags at 9 random positions in front of the collision slot can be expressed as: antennas.We repeat querying each tag 100 times to extract the signal lengths in different positions.As shown in Fig.6(a),the s(t)=Aei+;(t)hi+(t) (5) signal length of 50 tags are randomly distributed from 7620 =1Phase variation(degree) -10 -5 0 5 10 CDF 0 0.2 0.4 0.6 0.8 1 (a) The variance of the extracted phase profile Transmitting distance(cm) 20 40 60 80 100 Phase value(degree) 0 100 200 300 400 Phase of SDR reader Phase of impinj reader (b) Comparison of phase between commercial reader and SDR reader Fig. 4: Evaluation of the distinctiveness of the phase profile each step we measure 100 phase values individually. As shown in Fig. 4(b), the phase profile of SDR reader is almost the same as the phase value of commercial reader, where the correlation coefficients calculated on MATLAB is 0.9979. As shown in this figure, the phase profile is sensitive to any tiny movements, e.g., 1cm movement, which guarantees the distinctiveness in motion detection. C. Backscattered Link Frequency Due to manufacturing imperfection, the backscatter link frequency (BLF) of the response signal, i.e., fl in Eq. (1), varies among different tags. Thus, it can be used to distinguish tags as in [16, 18]. In fact, fl determines the length of a square wave, i.e., the duration of high/low voltage in Fig. 5(a). In regard to the typical modulation schemes in RFID systems, i.e., FM0 and Miller Modulation, data-0 and data-1 share the same amount of square waves. Taking Miller-4 Modulation as an example, both data-0 and data-1 contain eight square waves as shown in Fig. 5(a). Since the length of RN16 signal is fixed, it is reasonable to use the corresponding signal length of RN16 to represent BLF. The signal length of RN16 can be also transmitted to the BLF based on the actual sampling rate. 1 0 dummy 1 dummy 1 0 1 0 1 1 1 Example of preamble Ending of RN16 (a) The preamble and ending of RN16 signal 1 0 1 1 1 Slide window Cross correlation (b) Cross-correlation between measured samples and theoretical preamble Fig. 5: Calculate the signal length through cross-correlation We use the cross-correlation technology to extract the signal length by locating the starting and ending point of RN16 signal. Specifically, we adopt a slide window to calculate the cross-correlation value between the measured samples in the window and the special data sequence as shown in Fig. 5(b). Then we find the window whose cross-correlation value is the maximum, and record the position of the window. In this example, we locate the starting point of RN16 based on the special preamble sequence. Similarly we can locate the ending point using “dummy 1”. We use the number of samples between the starting and the ending point to represent BLF. To validate the distinctiveness of BLF, we conduct experiments on 50 different tags at 9 random positions in front of the antennas. We repeat querying each tag 100 times to extract the signal lengths in different positions. As shown in Fig. 6(a), the signal length of 50 tags are randomly distributed from 7620 to 7690. This indicates that the signal length can be used to distinguish among tags. Furthermore, we draw the histogram of the normalized variance of signal length in Fig. 6(b). The signal length is relatively stable with an average deviation of 2 samples, which is equal to 1µs. Therefore, BLF is stable and distinctive even though they are at different positions. But there are also some tags with the same BLF value which means we need to combine it with other attributes. Tag counts 0 10 20 30 40 50 Signal length 7600 7620 7640 7660 7680 7700 (a) The distribution of the signal length of different tags Signal length deviation -10 -5 0 5 10 Counts 0 5000 10000 15000 (b) Histogram of the variance of signal length Fig. 6: Evaluation of the distinctiveness of BLF V. EXTRACT PHYSICAL-LAYER FEATURES In the previous section, we have demonstrated the physicallayer features in the singleton slots. We can collect the physical-layer features in these singleton slots in the tag inventory phase. However, it is still time inefficiency because we cannot avoid useless collisions in RFID system. If c tags select the same slot to transmit the data, a c collision happens. When N tags select slots randomly from a frame with f slots according to the Binomial distribution, the probability of a c-collision slot can be expressed as: P r(c) = Ç N c å Å 1 f ãc Å 1 − 1 f ãN−c . (4) Number of tags in one slot 0 1 2 3 4+ f/N 0 1 2 3 4 5 0 0.2 0.4 0.6 0.8 Fig. 7: Theoretical probability of collision slots Fig. 7 shows the theoretical probability distribution of collision slot. The C1G2 standard improves the time efficiency by maximizing P r(1), thus at most 36.8% slots are singleton. In this case, 2-collision and 3-collision slots occupy 18.4% and 6.13% slots respectively, while only 1.89% slots are remained in 4+-collisions. So if we can efficiently resolve all the tags in singleton, 2-collision and 3-collision slots, we can identify 92% tags in a frame, which is 2.5 times compared with current protocol. Hence, we focus on how to extract physical-layer features from 2-collision and 3-collision slots. A. Model of Collision Signal Based on Eq. (2), the received baseband signal of a ccollision slot can be expressed as: s(t) = Aejβ +!c i=1 xi(t)hi + ˆn(t). (5)