正在加载图片...
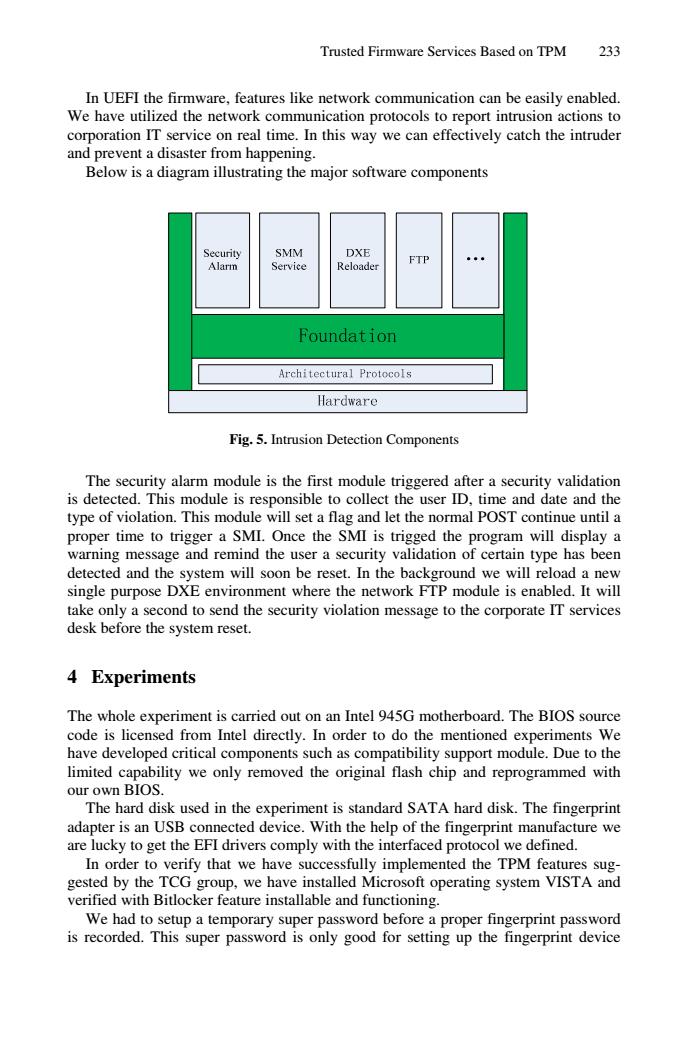
Trusted Firmware Services Based on TPM 233 In UEFI the firmware,features like network communication can be easily enabled. We have utilized the network communication protocols to report intrusion actions to corporation IT service on real time.In this way we can effectively catch the intruder and prevent a disaster from happening. Below is a diagram illustrating the major software components Security SMM DXE FTP Alarm Service Reloader Foundation Architectural Protocols Hardware Fig.5.Intrusion Detection Components The security alarm module is the first module triggered after a security validation is detected.This module is responsible to collect the user ID,time and date and the type of violation.This module will set a flag and let the normal POST continue until a proper time to trigger a SMI.Once the SMI is trigged the program will display a warning message and remind the user a security validation of certain type has been detected and the system will soon be reset.In the background we will reload a new single purpose DXE environment where the network FTP module is enabled.It will take only a second to send the security violation message to the corporate IT services desk before the system reset. 4 Experiments The whole experiment is carried out on an Intel 945G motherboard.The BIOS source code is licensed from Intel directly.In order to do the mentioned experiments We have developed critical components such as compatibility support module.Due to the limited capability we only removed the original flash chip and reprogrammed with our own BIOS. The hard disk used in the experiment is standard SATA hard disk.The fingerprint adapter is an USB connected device.With the help of the fingerprint manufacture we are lucky to get the EFI drivers comply with the interfaced protocol we defined. In order to verify that we have successfully implemented the TPM features sug- gested by the TCG group,we have installed Microsoft operating system VISTA and verified with Bitlocker feature installable and functioning. We had to setup a temporary super password before a proper fingerprint password is recorded.This super password is only good for setting up the fingerprint deviceTrusted Firmware Services Based on TPM 233 In UEFI the firmware, features like network communication can be easily enabled. We have utilized the network communication protocols to report intrusion actions to corporation IT service on real time. In this way we can effectively catch the intruder and prevent a disaster from happening. Below is a diagram illustrating the major software components Fig. 5. Intrusion Detection Components The security alarm module is the first module triggered after a security validation is detected. This module is responsible to collect the user ID, time and date and the type of violation. This module will set a flag and let the normal POST continue until a proper time to trigger a SMI. Once the SMI is trigged the program will display a warning message and remind the user a security validation of certain type has been detected and the system will soon be reset. In the background we will reload a new single purpose DXE environment where the network FTP module is enabled. It will take only a second to send the security violation message to the corporate IT services desk before the system reset. 4 Experiments The whole experiment is carried out on an Intel 945G motherboard. The BIOS source code is licensed from Intel directly. In order to do the mentioned experiments We have developed critical components such as compatibility support module. Due to the limited capability we only removed the original flash chip and reprogrammed with our own BIOS. The hard disk used in the experiment is standard SATA hard disk. The fingerprint adapter is an USB connected device. With the help of the fingerprint manufacture we are lucky to get the EFI drivers comply with the interfaced protocol we defined. In order to verify that we have successfully implemented the TPM features suggested by the TCG group, we have installed Microsoft operating system VISTA and verified with Bitlocker feature installable and functioning. We had to setup a temporary super password before a proper fingerprint password is recorded. This super password is only good for setting up the fingerprint device