正在加载图片...
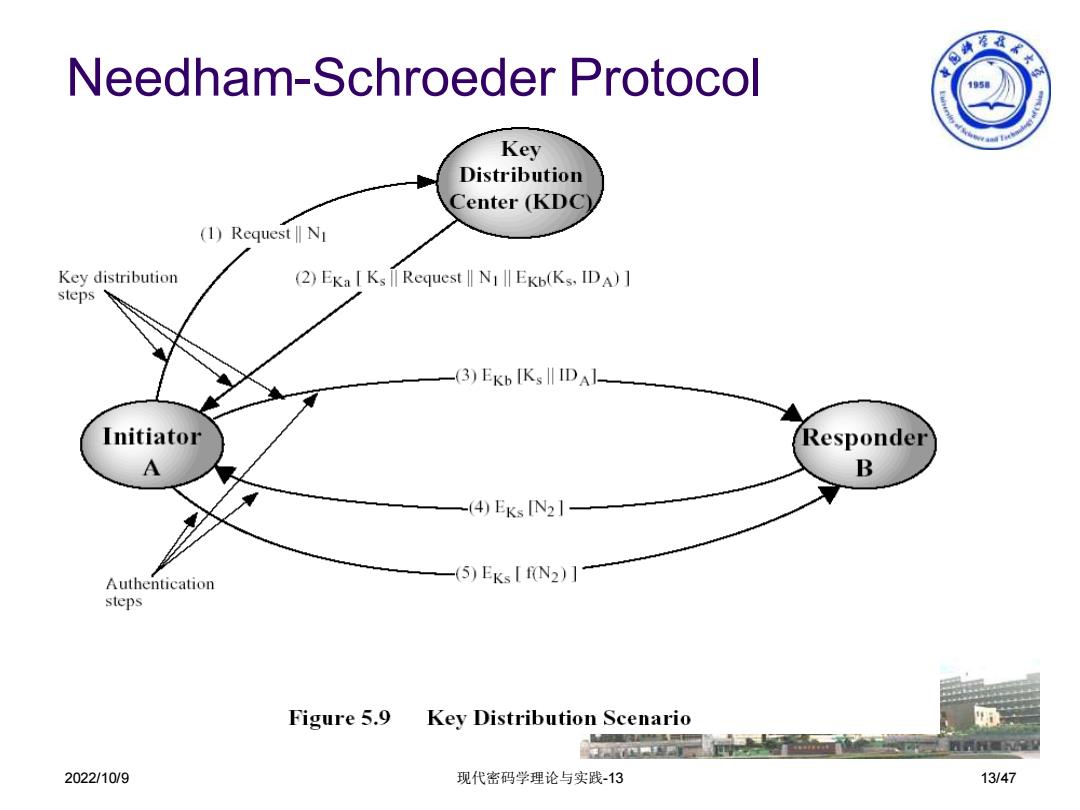
Needham-Schroeder Protocol 经长 105 Key Distribution Center (KDC) (1)Request NI Key distribution (2)Eka I Ks lI Request II NIll EKb(Ks.IDA)] steps -(3)EKb IKs DAl- Initiator Responder A B -(4)EKsN2] Authentication -(5)EKs[fN2)] steps Figure 5.9 Key Distribution Scenario 甲 2022/10/9 现代密码学理论与实践-13 13/472022/10/9 现代密码学理论与实践-13 13/47 Needham-Schroeder Protocol