正在加载图片...
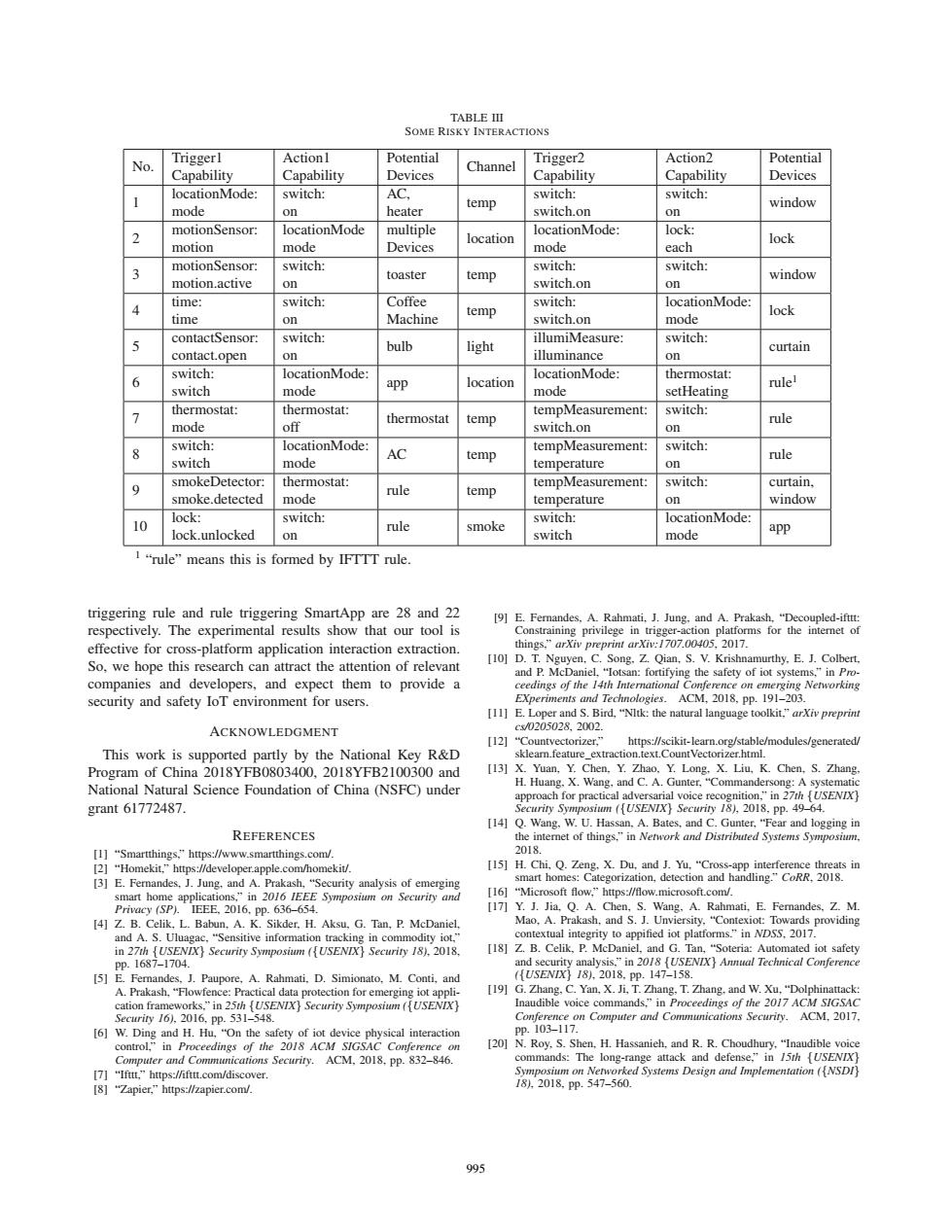
TABLE III SOME RISKY INTERACTIONS Actionl Potential Action2 Potential No Triggerl Trigger2 Channel Capability Capability Devices Capability Capability Devices locationMode: switch: AC. switch: switch: temp window mode on heater switch.on on motionSensor: locationMode multiple locationMode: lock: 2 location lock motion mode Devices mode each motionSensor: switch: switch: switch: 3 toaster window motion.active temp on switch.on on time: switch: Coffee switch: locationMode: temp lock time on Machine switch.on mode contactSensor: switch: illumiMeasure: switch: 5 bulb light contact.open on illuminance curtain on switch: locationMode: locationMode: thermostat: 6 location rulel switch mode app mode setHeating thermostat: thermostat: tempMeasurement: switch: 7 rule mode off thermostat temp switch.on on switch: locationMode: tempMeasurement: switch: 8 AC temp rule switch mode temperature on smokeDetector: thermostat: switch: 9 tempMeasurement: curtain, rule smoke.detected mode temp temperature on window lock: switch: switch: locationMode: 10 rule smoke lock.unlocked app on switch mode I“rule”means this is formed by IFTTT rule. triggering rule and rule triggering SmartApp are 28 and 22 [9]E.Fernandes.A.Rahmati.J.Jung.and A.Prakash."Decoupled-ifttt: respectively.The experimental results show that our tool is Constraining privilege in trigger-action platforms for the internet of effective for cross-platform application interaction extraction. things."arXiv preprint arXiv:1707.00405,2017. So,we hope this research can attract the attention of relevant [10]D.T.Nguyen,C.Song.Z.Qian,S.V.Krishnamurthy.E.J.Colbert. and P.McDaniel."Iotsan:fortifying the safety of iot systems,"in Pro- companies and developers,and expect them to provide a ceedings of the 14th International Conference on emerging Networking security and safety IoT environment for users. EXperiments and Technologies.ACM,2018,pp.191-203. [11]E.Loper and S.Bird,"NItk:the natural language toolkit,"arXiv preprint ACKNOWLEDGMENT cx/0205028.2002. [12]"Countvectorizer," https://scikit-learn.org/stable/modules/generated/ This work is supported partly by the National Key R&D sklear.feature extraction.text.CountVectorizer.html. Program of China 2018YFB0803400,2018YFB2100300 and [13]X.Yuan,Y.Chen.Y.Zhao.Y.Long.X.Liu,K.Chen,S.Zhang, National Natural Science Foundation of China(NSFC)under H.Huang.X.Wang,and C.A.Gunter,"Commandersong:A systematic approach for practical adversarial voice recognition,"in 27th {USENIX] grant61772487. Securiry Symposium (USENIX)Security 18).2018.pp.49-64. [14]Q.Wang,W.U.Hassan,A.Bates,and C.Gunter,"Fear and logging in REFERENCES the internet of things,"in Network and Distributed Systems Symposium. [l】“Smartthings,”https:/www.smartthings.com/. 2018. [2]"Homekit,"https://developer.apple.com/homekit/. [15]H.Chi,Q.Zeng,X.Du,and J.Yu,"Cross-app interference threats in [3]E.Fernandes.J.Jung.and A.Prakash,"Security analysis of emerging smart homes:Categorization,detection and handling."CoRR,2018. smant home applications,"in 2016 IEEE Symposium on Security and [16]"Microsoft flow,"https://flow.microsoft.com/. Privacy (SP).IEEE,2016.pp.636-654. [17]Y.J.Jia,Q.A.Chen,S.Wang.A.Rahmati,E.Fernandes,Z.M [4]Z.B.Celik.L.Babun,A.K.Sikder.H.Aksu,G.Tan,P.McDaniel, Mao,A.Prakash,and S.J.Unviersity,"Contexiot:Towards providing and A.S.Uluagac,"Sensitive information tracking in commodity iot," contextual integrity to appified iot platforms."in NDSS.2017. in 27th {USENIX Security Symposium ({USENIX}Securiry 18).2018. [18]Z.B.Celik,P.McDaniel,and G.Tan,"Soteria:Automated iot safety pp.1687-1704. and security analysis,"in 2018 {USENIX}Annual Technical Conference 5]E.Fernandes,J.Paupore,A.Rahmati.D.Simionato.M.Conti,and ({USENIX)181,2018.pp.147-158. A.Prakash,"Flowfence:Practical data protection for emerging iot appli- [19]G.Zhang.C.Yan,X.Ji,T.Zhang,T.Zhang,and W.Xu,"Dolphinattack: cation frameworks,"in 25th {USENIX Securiry Symposium (USENIX Inaudible voice commands,"in Proceedings of the 2017 ACM SIGSAC Security16),2016,pp.531-548. Conference on Computer and Communications Security.ACM,2017. [6]W.Ding and H.Hu,"On the safety of iot device physical interaction pp.103-117. control,"in Proceedings of the 2018 ACM SIGSAC Conference on [20]N.Roy,S.Shen,H.Hassanieh,and R.R.Choudhury,"Inaudible voice Computer and Communications Securiry.ACM,2018.pp.832-846. commands:The long-range attack and defense,"in 15th [USENIX} []“Ift,”https:://fu.com/discover. Symposium on Networked Systems Design and Implementation ({NSDI [8]"Zapier,"https://zapier.com/. 181,2018.pp.547-560. 995TABLE III SOME RISKY INTERACTIONS No. Trigger1 Capability Action1 Capability Potential Devices Channel Trigger2 Capability Action2 Capability Potential Devices 1 locationMode: mode switch: on AC, heater temp switch: switch.on switch: on window 2 motionSensor: motion locationMode mode multiple Devices location locationMode: mode lock: each lock 3 motionSensor: motion.active switch: on toaster temp switch: switch.on switch: on window 4 time: time switch: on Coffee Machine temp switch: switch.on locationMode: mode lock 5 contactSensor: contact.open switch: on bulb light illumiMeasure: illuminance switch: on curtain 6 switch: switch locationMode: mode app location locationMode: mode thermostat: setHeating rule1 7 thermostat: mode thermostat: off thermostat temp tempMeasurement: switch.on switch: on rule 8 switch: switch locationMode: mode AC temp tempMeasurement: temperature switch: on rule 9 smokeDetector: smoke.detected thermostat: mode rule temp tempMeasurement: temperature switch: on curtain, window 10 lock: lock.unlocked switch: on rule smoke switch: switch locationMode: mode app 1 “rule” means this is formed by IFTTT rule. triggering rule and rule triggering SmartApp are 28 and 22 respectively. The experimental results show that our tool is effective for cross-platform application interaction extraction. So, we hope this research can attract the attention of relevant companies and developers, and expect them to provide a security and safety IoT environment for users. ACKNOWLEDGMENT This work is supported partly by the National Key R&D Program of China 2018YFB0803400, 2018YFB2100300 and National Natural Science Foundation of China (NSFC) under grant 61772487. REFERENCES [1] “Smartthings,” https://www.smartthings.com/. [2] “Homekit,” https://developer.apple.com/homekit/. [3] E. Fernandes, J. Jung, and A. Prakash, “Security analysis of emerging smart home applications,” in 2016 IEEE Symposium on Security and Privacy (SP). IEEE, 2016, pp. 636–654. [4] Z. B. Celik, L. Babun, A. K. Sikder, H. Aksu, G. Tan, P. McDaniel, and A. S. Uluagac, “Sensitive information tracking in commodity iot,” in 27th {USENIX} Security Symposium ({USENIX} Security 18), 2018, pp. 1687–1704. [5] E. Fernandes, J. Paupore, A. Rahmati, D. Simionato, M. Conti, and A. Prakash, “Flowfence: Practical data protection for emerging iot application frameworks,” in 25th {USENIX} Security Symposium ({USENIX} Security 16), 2016, pp. 531–548. [6] W. Ding and H. Hu, “On the safety of iot device physical interaction control,” in Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. ACM, 2018, pp. 832–846. [7] “Ifttt,” https://ifttt.com/discover. [8] “Zapier,” https://zapier.com/. [9] E. Fernandes, A. Rahmati, J. Jung, and A. Prakash, “Decoupled-ifttt: Constraining privilege in trigger-action platforms for the internet of things,” arXiv preprint arXiv:1707.00405, 2017. [10] D. T. Nguyen, C. Song, Z. Qian, S. V. Krishnamurthy, E. J. Colbert, and P. McDaniel, “Iotsan: fortifying the safety of iot systems,” in Proceedings of the 14th International Conference on emerging Networking EXperiments and Technologies. ACM, 2018, pp. 191–203. [11] E. Loper and S. Bird, “Nltk: the natural language toolkit,” arXiv preprint cs/0205028, 2002. [12] “Countvectorizer,” https://scikit-learn.org/stable/modules/generated/ sklearn.feature extraction.text.CountVectorizer.html. [13] X. Yuan, Y. Chen, Y. Zhao, Y. Long, X. Liu, K. Chen, S. Zhang, H. Huang, X. Wang, and C. A. Gunter, “Commandersong: A systematic approach for practical adversarial voice recognition,” in 27th {USENIX} Security Symposium ({USENIX} Security 18), 2018, pp. 49–64. [14] Q. Wang, W. U. Hassan, A. Bates, and C. Gunter, “Fear and logging in the internet of things,” in Network and Distributed Systems Symposium, 2018. [15] H. Chi, Q. Zeng, X. Du, and J. Yu, “Cross-app interference threats in smart homes: Categorization, detection and handling.” CoRR, 2018. [16] “Microsoft flow,” https://flow.microsoft.com/. [17] Y. J. Jia, Q. A. Chen, S. Wang, A. Rahmati, E. Fernandes, Z. M. Mao, A. Prakash, and S. J. Unviersity, “Contexiot: Towards providing contextual integrity to appified iot platforms.” in NDSS, 2017. [18] Z. B. Celik, P. McDaniel, and G. Tan, “Soteria: Automated iot safety and security analysis,” in 2018 {USENIX} Annual Technical Conference ({USENIX} 18), 2018, pp. 147–158. [19] G. Zhang, C. Yan, X. Ji, T. Zhang, T. Zhang, and W. Xu, “Dolphinattack: Inaudible voice commands,” in Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. ACM, 2017, pp. 103–117. [20] N. Roy, S. Shen, H. Hassanieh, and R. R. Choudhury, “Inaudible voice commands: The long-range attack and defense,” in 15th {USENIX} Symposium on Networked Systems Design and Implementation ({NSDI} 18), 2018, pp. 547–560. 995