正在加载图片...
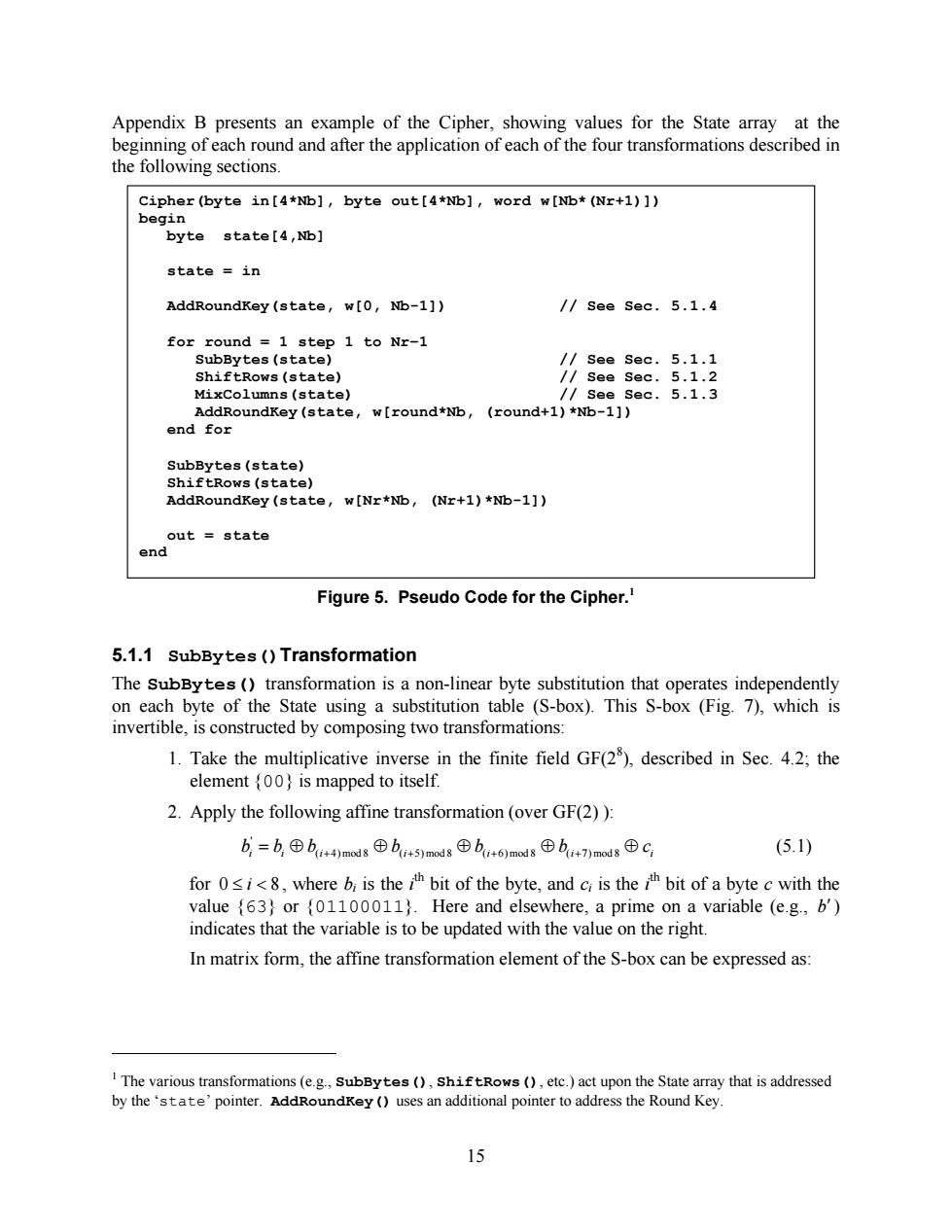
Appendix B presents an example of the Cipher,showing values for the State array at the beginning of each round and after the application of each of the four transformations described in the following sections. Cipher (byte in[4*Nb],byte out[4*Nb],word w[Nb*(Nr+1)]) begin byte:state[4,Nb】 state in AddRoundKey (state,w[0,Nb-1]) /See Sec.5.1.4 for round 1 step 1 to Nr-1 SubBytes (state) /See Sec.5.1.1 ShiftRows(state) /See Sec.5.1.2 MixColumns (state) /see sec.5.1.3 AddRoundKey(state,w[round*Nb, (round+1)*Nb-1]) end for SubBytes(state) ShiftRows (state) AddRoundKey(state,w[Nr*Nb,(Nr+1)*Nb-1]) out state end Figure 5.Pseudo Code for the Cipher. 5.1.1 SubBytes ()Transformation The SubBytes (transformation is a non-linear byte substitution that operates independently on each byte of the State using a substitution table (S-box).This S-box (Fig.7),which is invertible,is constructed by composing two transformations: 1.Take the multiplicative inverse in the finite field GF(2),described in Sec.4.2;the element (00)is mapped to itself. 2.Apply the following affine transformation (over GF(2)): b,=b,⊕bi+4)md8⊕b+5)modsb+6)madg⊕b+7)mod8⊕C (5.1) for 0i,where b is theh bit of the byte,and cr is the h bit of a byte c with the value {63)or {01100011).Here and elsewhere,a prime on a variable (e.g.,b') indicates that the variable is to be updated with the value on the right. In matrix form,the affine transformation element of the S-box can be expressed as: I The various transformations(e.g.,SubBytes(),shiftRows(),etc.)act upon the State array that is addressed by the 'state'pointer.AddRoundKey (uses an additional pointer to address the Round Key. 1515 Appendix B presents an example of the Cipher, showing values for the State array at the beginning of each round and after the application of each of the four transformations described in the following sections. Figure 5. Pseudo Code for the Cipher.1 5.1.1 SubBytes()Transformation The SubBytes() transformation is a non-linear byte substitution that operates independently on each byte of the State using a substitution table (S-box). This S-box (Fig. 7), which is invertible, is constructed by composing two transformations: 1. Take the multiplicative inverse in the finite field GF(28 ), described in Sec. 4.2; the element {00} is mapped to itself. 2. Apply the following affine transformation (over GF(2) ): i i i i i i i b = b Å b Å b Å b Å b Å c ( +4) mod 8 ( +5) mod 8 ( +6) mod 8 ( +7) mod 8 ' (5.1) for 0 £ i < 8 , where bi is the i th bit of the byte, and ci is the i th bit of a byte c with the value {63} or {01100011}. Here and elsewhere, a prime on a variable (e.g., b¢) indicates that the variable is to be updated with the value on the right. In matrix form, the affine transformation element of the S-box can be expressed as: 1 The various transformations (e.g., SubBytes(), ShiftRows(), etc.) act upon the State array that is addressed by the ‘state’ pointer. AddRoundKey() uses an additional pointer to address the Round Key. Cipher(byte in[4*Nb], byte out[4*Nb], word w[Nb*(Nr+1)]) begin byte state[4,Nb] state = in AddRoundKey(state, w[0, Nb-1]) // See Sec. 5.1.4 for round = 1 step 1 to Nr–1 SubBytes(state) // See Sec. 5.1.1 ShiftRows(state) // See Sec. 5.1.2 MixColumns(state) // See Sec. 5.1.3 AddRoundKey(state, w[round*Nb, (round+1)*Nb-1]) end for SubBytes(state) ShiftRows(state) AddRoundKey(state, w[Nr*Nb, (Nr+1)*Nb-1]) out = state end