正在加载图片...
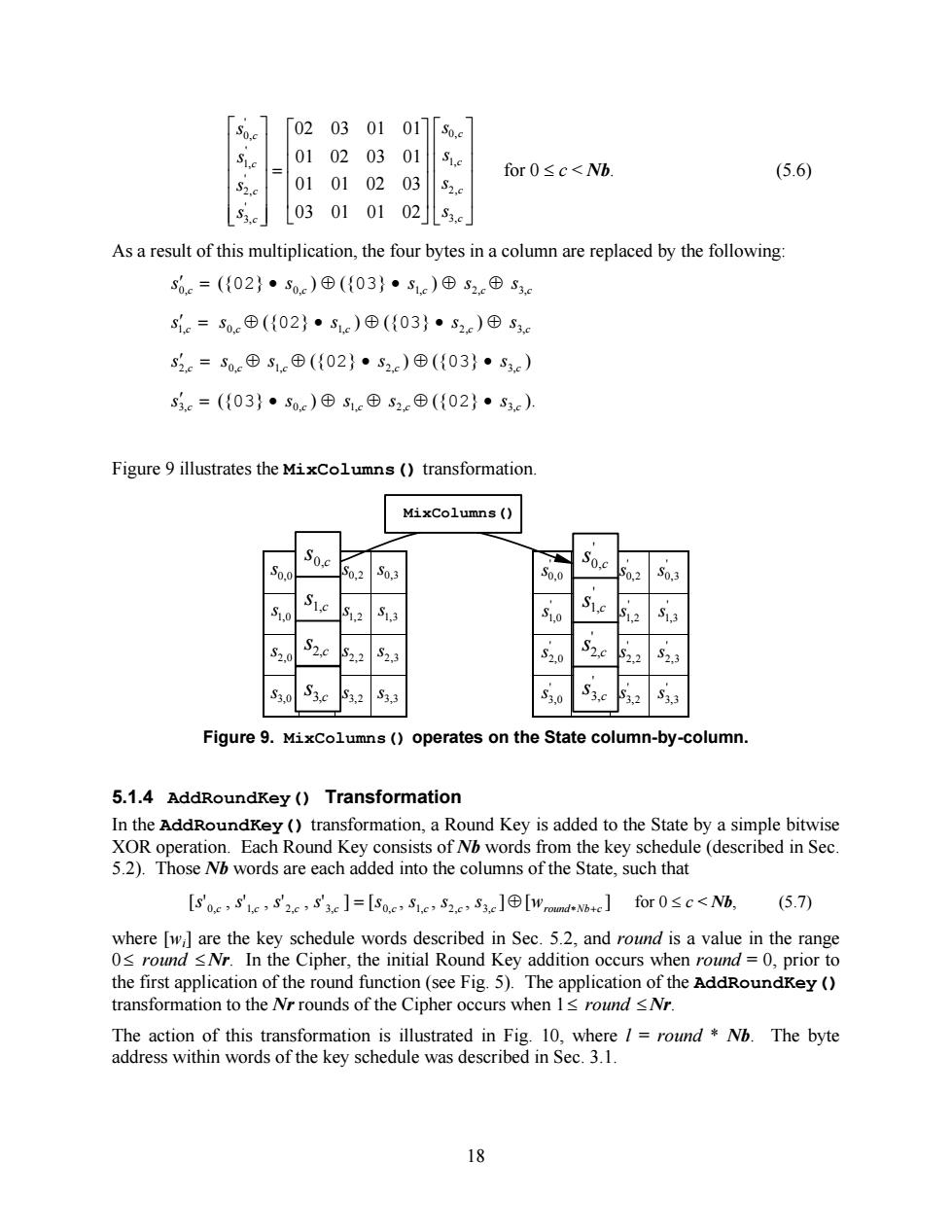
So.c 02 03 01 01][so.e 01 02 03 01 SL.e for0≤c<Nb (5.6) 01 01 02 03 s2. 03 01 01 02S3.c As a result of this multiplication,the four bytes in a column are replaced by the following: s0e=({02}·Soe)⊕({03}·Se)⊕S2e⊕5c Se=s⊕({02}·Se)⊕({03}·52c)⊕5c S2c=S.e⊕5⊕({02}·S2c)⊕({03}·Sc) sc=({03}·Soe)⊕S1e田S2⊕({02}·S3e) Figure 9 illustrates the MixColumns()transformation. MixColumns ( So.o Soc 5o2 S0,3 S0,0 So.c 0,2 S03 Sye S12 ,3 S2.0 S2f S2,2 S23 S20 S2,2 S23 S3.0 S3f S3,2 S33 S30 S33 Figure 9.Mixcolumns()operates on the State column-by-column. 5.1.4 AddRoundKey (Transformation In the AddRoundKey (transformation,a Round Key is added to the State by a simple bitwise XOR operation.Each Round Key consists of Nb words from the key schedule (described in Sec. 5.2).Those Nb words are each added into the columns of the State,such that [s'oc S'Le S2e,S'3e]=[So.c SLe S2 S3][Wrommd-Nbte]for 0sc<Nb, (5.7) where [wi]are the key schedule words described in Sec.5.2,and round is a value in the range 0<round <Nr.In the Cipher,the initial Round Key addition occurs when round =0,prior to the first application of the round function(see Fig.5).The application of the AddRoundKey ( transformation to the Nr rounds of the Cipher occurs when 1s round <Nr. The action of this transformation is illustrated in Fig.10,where /round Nb.The byte address within words of the key schedule was described in Sec.3.1. 1818 ú ú ú ú û ù ê ê ê ê ë é ú ú ú ú û ù ê ê ê ê ë é = ú ú ú ú ú û ù ê ê ê ê ê ë é c c c c c c c c s s s s s s s s 3, 2, 1, 0, ' 3, ' 2, ' 1, ' 0, 03 01 01 02 01 01 02 03 01 02 03 01 02 03 01 01 for 0 £ c < Nb. (5.6) As a result of this multiplication, the four bytes in a column are replaced by the following: s0 ¢ ,c = ({02} · c s0, ) Å ({03} · c s1, ) Å c s2, Å c s3, s1 ¢ ,c = c s0, Å ({02} · c s1, ) Å ({03} · c s2, ) Å c s3, s¢ 2,c = c s0, Å c s1, Å ({02} · c s2, ) Å ({03} · c s3, ) s3 ¢ ,c = ({03} · c s0, ) Å c s1, Å c s2, Å ({02} · c s3, ). Figure 9 illustrates the MixColumns() transformation. 0,0 s 0,1 s 0,2 s 0,3 s ' 0,0 s ' 0,1 s ' 0,2 s ' 0,3 s 1,0 s 1,1 s 1,2 s 1,3 s ' 1,0 s ' 1,1 s ' 1,2 s ' 1,3 s 2,0 s 2,1 s 2,2 s 2,3 s ' 2,0 s ' 2,1 s ' 2,2 s ' 2,3 s 3,0 s 3,1 s 3,2 s 3,3 s ' 3,0 s ' 3,1 s ' 3,2 s ' 3,3 s Figure 9. MixColumns() operates on the State column-by-column. 5.1.4 AddRoundKey() Transformation In the AddRoundKey() transformation, a Round Key is added to the State by a simple bitwise XOR operation. Each Round Key consists of Nb words from the key schedule (described in Sec. 5.2). Those Nb words are each added into the columns of the State, such that [ ' , ' , ' , ' ] [ , , , ] [ ] 0,c 1,c 2,c 3,c 0,c 1,c 2,c 3,c wround Nb c s s s s s s s s = Å * + for 0 £ c < Nb, (5.7) where [wi] are the key schedule words described in Sec. 5.2, and round is a value in the range 0£ round £ Nr. In the Cipher, the initial Round Key addition occurs when round = 0, prior to the first application of the round function (see Fig. 5). The application of the AddRoundKey() transformation to the Nr rounds of the Cipher occurs when 1£ round £ Nr. The action of this transformation is illustrated in Fig. 10, where l = round * Nb. The byte address within words of the key schedule was described in Sec. 3.1. MixColumns() c s0, c s1, c s2, c s3, ' 0,c s ' 1,c s ' 2,c s ' 3,c s