正在加载图片...
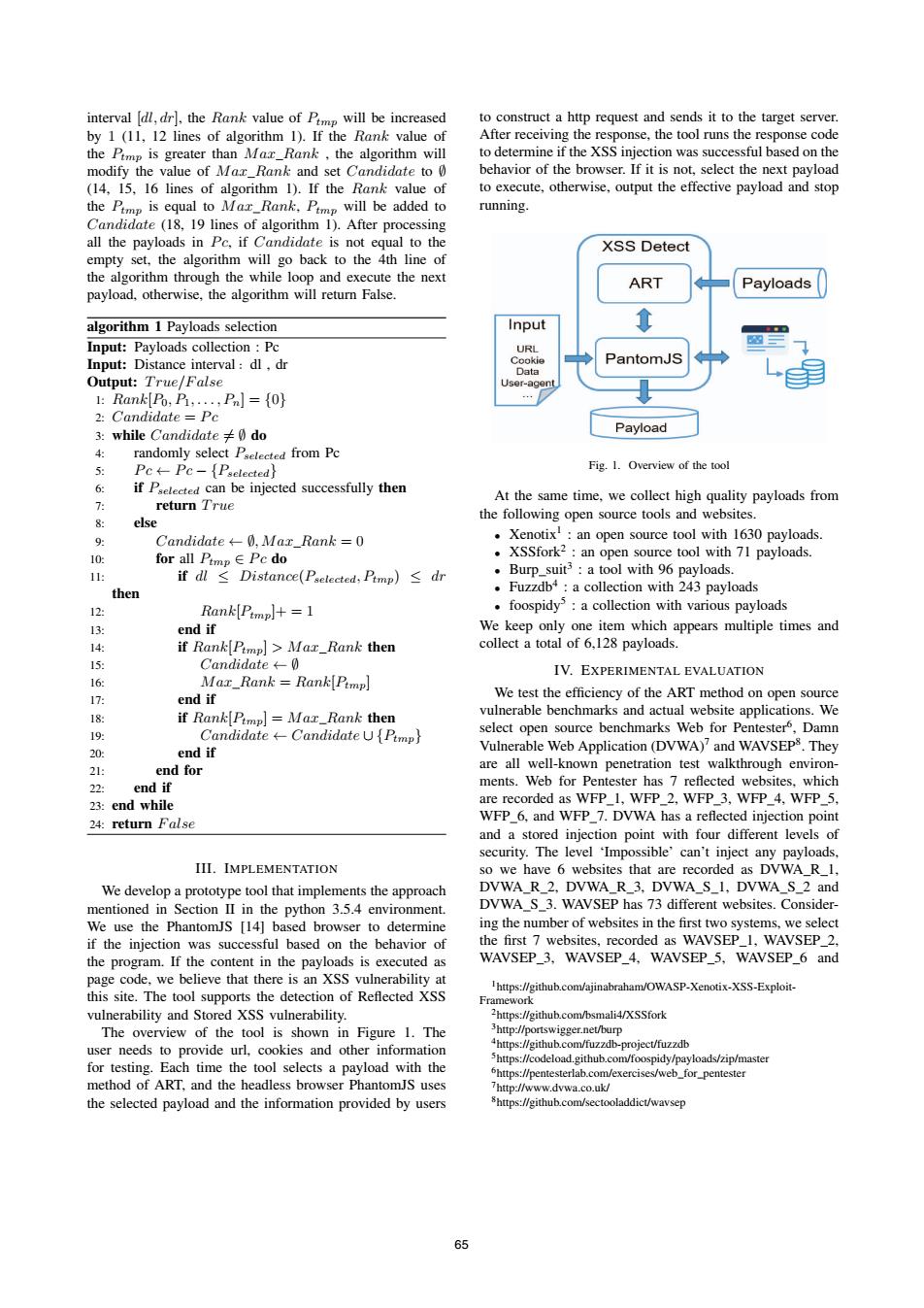
interval [dl,dr].the Rank value of Pmp will be increased to construct a http request and sends it to the target server by 1 (11,12 lines of algorithm 1).If the Rank value of After receiving the response,the tool runs the response code the Pimp is greater than Mar_Rank,the algorithm will to determine if the XSS injection was successful based on the modify the value of Max Rank and set Candidate to 0 behavior of the browser.If it is not,select the next payload (14,15,16 lines of algorithm 1).If the Rank value of to execute,otherwise,output the effective payload and stop the Pimp is equal to Mar_Rank.Pimp will be added to running. Candidate (18,19 lines of algorithm 1).After processing all the payloads in Pc.if Candidate is not equal to the XSS Detect empty set,the algorithm will go back to the 4th line of the algorithm through the while loop and execute the next ART payload,otherwise,the algorithm will return False. Payloads algorithm 1 Payloads selection Input Input:Payloads collection:Pc URL Input:Distance interval:dl,dr Cookie PantomJS Data Output:True/False User-agent 上Rank[Po,B,.,Pn={o} 2:Candidate Pc 3:while Candidate0 do Payload randomly select Pselected from Pc Pc←Pc-{Pselected} Fig.1.Overview of the tool 6 if Pselected can be injected successfully then At the same time,we collect high quality payloads from return True the following open source tools and websites. else 9 Candidate+0.Max Rank =0 Xenotix!:an open source tool with 1630 payloads. 10: for all Pimp∈Pcdo XSSfork2:an open source tool with 71 payloads. 11: ifdl≤Distance(Pselected,Ptmp)≤dh Burp_suit3:a tool with 96 payloads then Fuzzdb4:a collection with 243 payloads 12: Rank[Pimp]+=1 foospidys:a collection with various payloads 13: end if We keep only one item which appears multiple times and 14 if Rank(Pimp]>Mar_Rank then collect a total of 6,128 payloads. 15: Candidate←-0 IV.EXPERIMENTAL EVALUATION 16: Mar_Rank Rank[Pimp] 17: end if We test the efficiency of the ART method on open source 伊 if Rank(Pimp]Mar_Rank then vulnerable benchmarks and actual website applications.We 19: CandidateCandidate U{Pimp} select open source benchmarks Web for Pentester5,Damn 20: end if Vulnerable Web Application(DVWA)?and WAVSEPS.They 21: end for are all well-known penetration test walkthrough environ- 22 end if ments.Web for Pentester has 7 refected websites,which 23:end while are recorded as WFP_1,WFP_2,WFP 3,WFP 4,WFP 5. 24:return False WFP_6,and WFP_7.DVWA has a reflected injection point and a stored injection point with four different levels of security.The level 'Impossible'can't inject any payloads. III.IMPLEMENTATION so we have 6 websites that are recorded as DVWA_R1, We develop a prototype tool that implements the approach DVWA_R_2,DVWA_R_3,DVWA_S_I,DVWA_S_2 and mentioned in Section II in the python 3.5.4 environment. DVWA S 3.WAVSEP has 73 different websites.Consider- We use the PhantomJS [14]based browser to determine ing the number of websites in the first two systems,we select if the injection was successful based on the behavior of the first 7 websites,recorded as WAVSEP_1,WAVSEP 2 the program.If the content in the payloads is executed as WAVSEP_3,WAVSEP_4,WAVSEP_5, WAVSEP 6 and page code,we believe that there is an XSS vulnerability at Ihttps://github.com/ajinabraham/OWASP-Xenotix-XSS-Exploit- this site.The tool supports the detection of Reflected XSS Framework vulnerability and Stored XSS vulnerability. 2https://github.com/bsmali4/XSSfork The overview of the tool is shown in Figure 1.The 3http://portswigger.net/burp user needs to provide url,cookies and other information 4https://github.com/fuzzdb-project/fuzzdb for testing.Each time the tool selects a payload with the 5https://codeload.github.com/foospidy/payloads/zip/master 6https://pentesterlab.com/exercises/web_for_pentester method of ART,and the headless browser PhantomJS uses 7http://www.dvwa.co.uk/ the selected payload and the information provided by users 8https://github.com/sectooladdict/wavsep 65interval [dl, dr], the Rank value of Ptmp will be increased by 1 (11, 12 lines of algorithm 1). If the Rank value of the Ptmp is greater than M ax Rank , the algorithm will modify the value of M ax Rank and set Candidate to ∅ (14, 15, 16 lines of algorithm 1). If the Rank value of the Ptmp is equal to M ax Rank, Ptmp will be added to Candidate (18, 19 lines of algorithm 1). After processing all the payloads in P c, if Candidate is not equal to the empty set, the algorithm will go back to the 4th line of the algorithm through the while loop and execute the next payload, otherwise, the algorithm will return False. algorithm 1 Payloads selection Input: Payloads collection : Pc Input: Distance interval:dl , dr Output: T rue/F alse 1: Rank[P0, P1,...,Pn] = {0} 2: Candidate = P c 3: while Candidate = ∅ do 4: randomly select Pselected from Pc 5: P c ← P c − {Pselected} 6: if Pselected can be injected successfully then 7: return T rue 8: else 9: Candidate ← ∅, M ax Rank = 0 10: for all Ptmp ∈ P c do 11: if dl ≤ Distance(Pselected, Ptmp) ≤ dr then 12: Rank[Ptmp]+ = 1 13: end if 14: if Rank[Ptmp] > M ax Rank then 15: Candidate ← ∅ 16: M ax Rank = Rank[Ptmp] 17: end if 18: if Rank[Ptmp] = M ax Rank then 19: Candidate ← Candidate ∪ {Ptmp} 20: end if 21: end for 22: end if 23: end while 24: return F alse III. IMPLEMENTATION We develop a prototype tool that implements the approach mentioned in Section II in the python 3.5.4 environment. We use the PhantomJS [14] based browser to determine if the injection was successful based on the behavior of the program. If the content in the payloads is executed as page code, we believe that there is an XSS vulnerability at this site. The tool supports the detection of Reflected XSS vulnerability and Stored XSS vulnerability. The overview of the tool is shown in Figure 1. The user needs to provide url, cookies and other information for testing. Each time the tool selects a payload with the method of ART, and the headless browser PhantomJS uses the selected payload and the information provided by users to construct a http request and sends it to the target server. After receiving the response, the tool runs the response code to determine if the XSS injection was successful based on the behavior of the browser. If it is not, select the next payload to execute, otherwise, output the effective payload and stop running. Fig. 1. Overview of the tool At the same time, we collect high quality payloads from the following open source tools and websites. • Xenotix1 : an open source tool with 1630 payloads. • XSSfork2 : an open source tool with 71 payloads. • Burp suit3 : a tool with 96 payloads. • Fuzzdb4 : a collection with 243 payloads • foospidy5 : a collection with various payloads We keep only one item which appears multiple times and collect a total of 6,128 payloads. IV. EXPERIMENTAL EVALUATION We test the efficiency of the ART method on open source vulnerable benchmarks and actual website applications. We select open source benchmarks Web for Pentester6, Damn Vulnerable Web Application (DVWA)7 and WAVSEP8. They are all well-known penetration test walkthrough environments. Web for Pentester has 7 reflected websites, which are recorded as WFP 1, WFP 2, WFP 3, WFP 4, WFP 5, WFP 6, and WFP 7. DVWA has a reflected injection point and a stored injection point with four different levels of security. The level ‘Impossible’ can’t inject any payloads, so we have 6 websites that are recorded as DVWA R 1, DVWA R 2, DVWA R 3, DVWA S 1, DVWA S 2 and DVWA S 3. WAVSEP has 73 different websites. Considering the number of websites in the first two systems, we select the first 7 websites, recorded as WAVSEP 1, WAVSEP 2, WAVSEP 3, WAVSEP 4, WAVSEP 5, WAVSEP 6 and 1https://github.com/ajinabraham/OWASP-Xenotix-XSS-ExploitFramework 2https://github.com/bsmali4/XSSfork 3http://portswigger.net/burp 4https://github.com/fuzzdb-project/fuzzdb 5https://codeload.github.com/foospidy/payloads/zip/master 6https://pentesterlab.com/exercises/web for pentester 7http://www.dvwa.co.uk/ 8https://github.com/sectooladdict/wavsep 65�