正在加载图片...
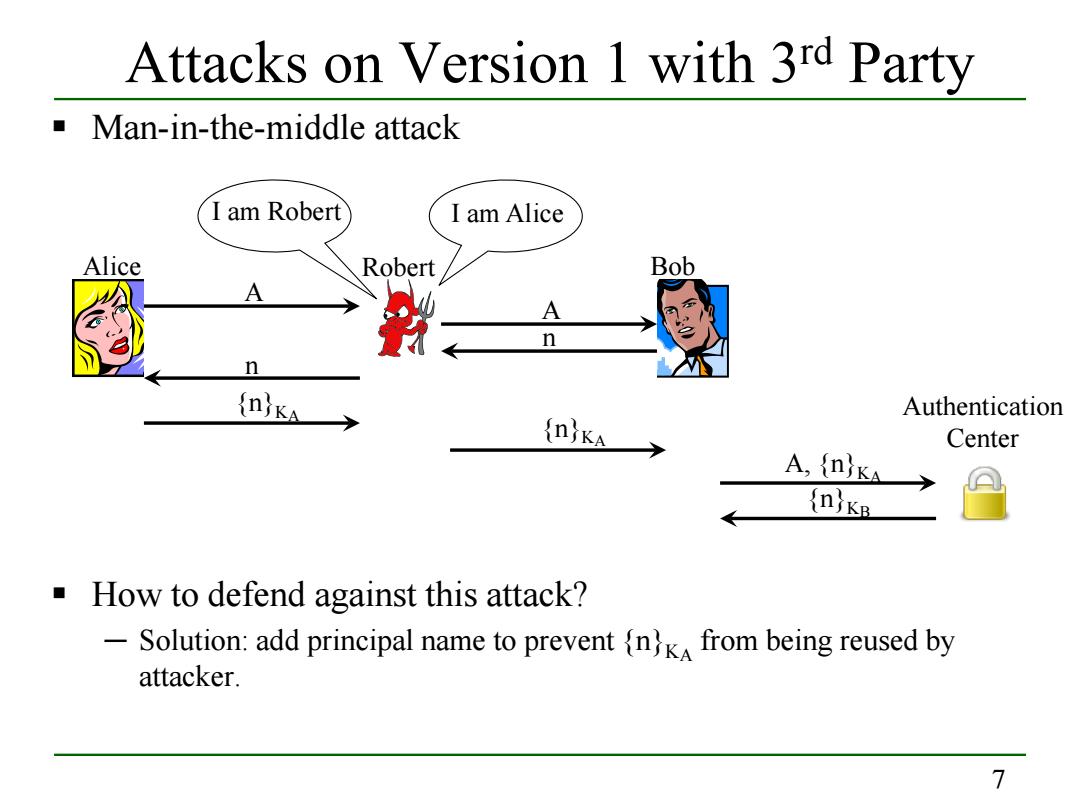
Attacks on Version 1 with 3rd Party Man-in-the-middle attack I am Robert I am Alice Alice Robert Bob A n Authentication Center A,(nika (nKB How to defend against this attack? -Solution:add principal name to prevent (n}k from being reused by attacker. 77 Man-in-the-middle attack How to defend against this attack? ─ Solution: add principal name to prevent {n}KA from being reused by attacker. Alice Bob A n {n}KA A, {n}KA {n}KB Authentication Center Robert A n {n}KA Attacks on Version 1 with 3rd Party I am Robert I am Alice