正在加载图片...
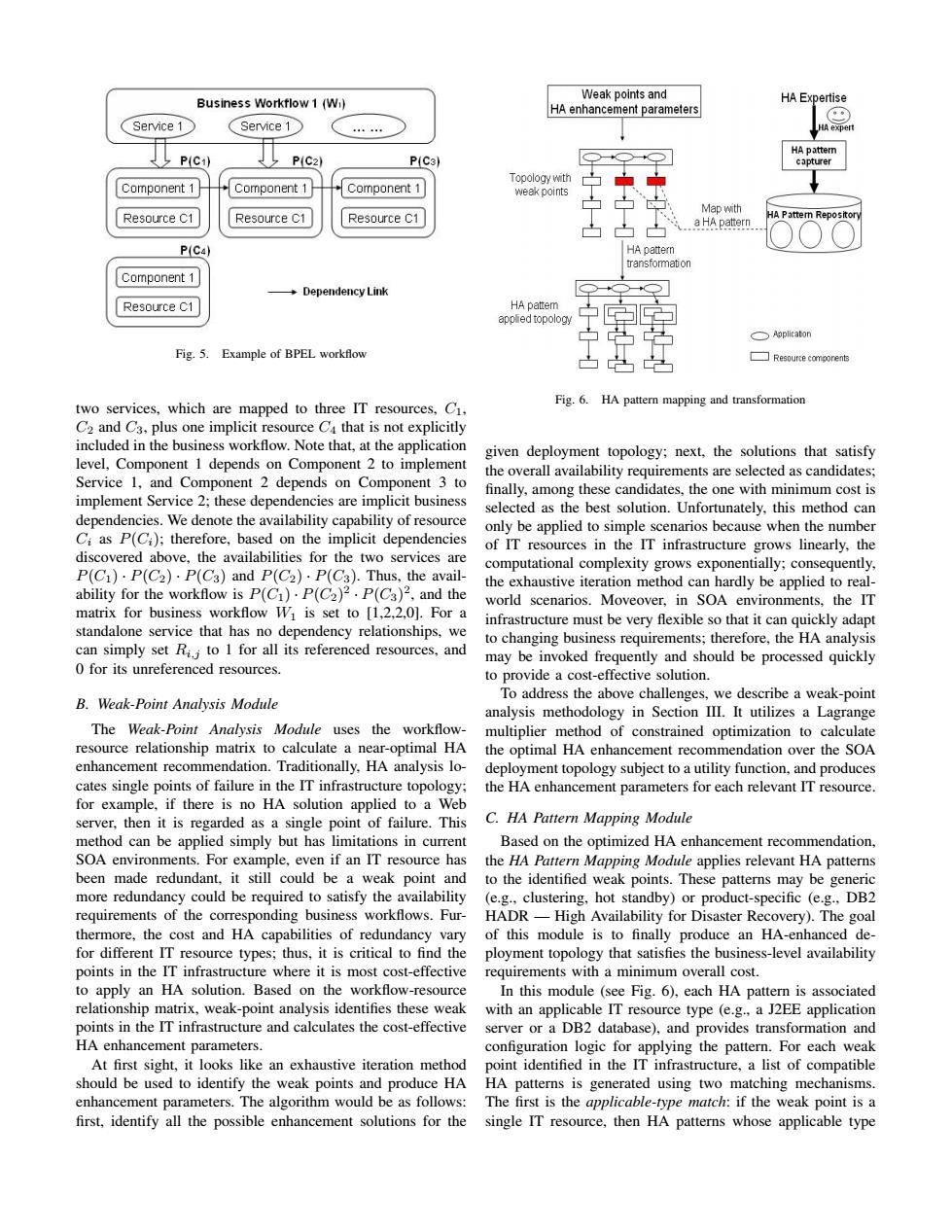
Weak points and Business Worktlow 1 (Wi) HA Expertise HA enhancement parameters Service 1 Service 1 HA pattem P(Ci) P(C2) P(C3) capturer Topology with Component 1 Component 1 Component 1 weak points Map with Resource C1 Resource C1 Resource C1 A Pattern Reposito a HA pattern P(C4) HA pattern transfommation Component 1 →Dependency Link Resource C1 HA pattem appled topolog☑ T ○pplicaton Fig.5.Example of BPEL workflow two services,which are mapped to three IT resources,C1, Fig.6.HA pattern mapping and transformation C2 and C3,plus one implicit resource C4 that is not explicitly included in the business workflow.Note that,at the application given deployment topology;next,the solutions that satisfy level,Component 1 depends on Component 2 to implement the overall availability requirements are selected as candidates; Service 1,and Component 2 depends on Component 3 to finally,among these candidates,the one with minimum cost is implement Service 2;these dependencies are implicit business selected as the best solution.Unfortunately.this method can dependencies.We denote the availability capability of resource only be applied to simple scenarios because when the number Ci as P(Ci);therefore,based on the implicit dependencies of IT resources in the IT infrastructure grows linearly,the discovered above,the availabilities for the two services are computational complexity grows exponentially;consequently, P(C)·P(C2)·P(C3)andP(C2)·P(C3).Thus,the avail-- the exhaustive iteration method can hardly be applied to real- ability for the workflow is P(C1).P(C2)2.P(C3)2,and the world scenarios.Moveover,in SOA environments,the IT matrix for business workflow Wi is set to [1,2,2,0].For a infrastructure must be very flexible so that it can quickly adapt standalone service that has no dependency relationships,we to changing business requirements;therefore,the HA analysis can simply set Ri.i to 1 for all its referenced resources,and may be invoked frequently and should be processed quickly 0 for its unreferenced resources. to provide a cost-effective solution. To address the above challenges,we describe a weak-point B.Weak-Point Analysis Module analysis methodology in Section III.It utilizes a Lagrange The Weak-Point Analysis Module uses the workflow- multiplier method of constrained optimization to calculate resource relationship matrix to calculate a near-optimal HA the optimal HA enhancement recommendation over the SOA enhancement recommendation.Traditionally,HA analysis lo- deployment topology subject to a utility function,and produces cates single points of failure in the IT infrastructure topology; the HA enhancement parameters for each relevant IT resource. for example,if there is no HA solution applied to a Web server,then it is regarded as a single point of failure.This C.HA Pattern Mapping Module method can be applied simply but has limitations in current Based on the optimized HA enhancement recommendation. SOA environments.For example,even if an IT resource has the HA Pattern Mapping Module applies relevant HA patterns been made redundant,it still could be a weak point and to the identified weak points.These patterns may be generic more redundancy could be required to satisfy the availability (e.g.,clustering,hot standby)or product-specific (e.g.,DB2 requirements of the corresponding business workflows.Fur- HADR-High Availability for Disaster Recovery).The goal thermore,the cost and HA capabilities of redundancy vary of this module is to finally produce an HA-enhanced de- for different IT resource types;thus,it is critical to find the ployment topology that satisfies the business-level availability points in the IT infrastructure where it is most cost-effective requirements with a minimum overall cost. to apply an HA solution.Based on the workflow-resource In this module (see Fig.6),each HA pattern is associated relationship matrix,weak-point analysis identifies these weak with an applicable IT resource type (e.g.,a J2EE application points in the IT infrastructure and calculates the cost-effective server or a DB2 database),and provides transformation and HA enhancement parameters. configuration logic for applying the pattern.For each weak At first sight,it looks like an exhaustive iteration method point identified in the IT infrastructure,a list of compatible should be used to identify the weak points and produce HA HA patterns is generated using two matching mechanisms. enhancement parameters.The algorithm would be as follows: The first is the applicable-type match:if the weak point is a first,identify all the possible enhancement solutions for the single IT resource,then HA patterns whose applicable typeFig. 5. Example of BPEL workflow two services, which are mapped to three IT resources, C1, C2 and C3, plus one implicit resource C4 that is not explicitly included in the business workflow. Note that, at the application level, Component 1 depends on Component 2 to implement Service 1, and Component 2 depends on Component 3 to implement Service 2; these dependencies are implicit business dependencies. We denote the availability capability of resource Ci as P(Ci); therefore, based on the implicit dependencies discovered above, the availabilities for the two services are P(C1) · P(C2) · P(C3) and P(C2) · P(C3). Thus, the availability for the workflow is P(C1) · P(C2) 2 · P(C3) 2 , and the matrix for business workflow W1 is set to [1,2,2,0]. For a standalone service that has no dependency relationships, we can simply set Ri,j to 1 for all its referenced resources, and 0 for its unreferenced resources. B. Weak-Point Analysis Module The Weak-Point Analysis Module uses the workflowresource relationship matrix to calculate a near-optimal HA enhancement recommendation. Traditionally, HA analysis locates single points of failure in the IT infrastructure topology; for example, if there is no HA solution applied to a Web server, then it is regarded as a single point of failure. This method can be applied simply but has limitations in current SOA environments. For example, even if an IT resource has been made redundant, it still could be a weak point and more redundancy could be required to satisfy the availability requirements of the corresponding business workflows. Furthermore, the cost and HA capabilities of redundancy vary for different IT resource types; thus, it is critical to find the points in the IT infrastructure where it is most cost-effective to apply an HA solution. Based on the workflow-resource relationship matrix, weak-point analysis identifies these weak points in the IT infrastructure and calculates the cost-effective HA enhancement parameters. At first sight, it looks like an exhaustive iteration method should be used to identify the weak points and produce HA enhancement parameters. The algorithm would be as follows: first, identify all the possible enhancement solutions for the Fig. 6. HA pattern mapping and transformation given deployment topology; next, the solutions that satisfy the overall availability requirements are selected as candidates; finally, among these candidates, the one with minimum cost is selected as the best solution. Unfortunately, this method can only be applied to simple scenarios because when the number of IT resources in the IT infrastructure grows linearly, the computational complexity grows exponentially; consequently, the exhaustive iteration method can hardly be applied to realworld scenarios. Moveover, in SOA environments, the IT infrastructure must be very flexible so that it can quickly adapt to changing business requirements; therefore, the HA analysis may be invoked frequently and should be processed quickly to provide a cost-effective solution. To address the above challenges, we describe a weak-point analysis methodology in Section III. It utilizes a Lagrange multiplier method of constrained optimization to calculate the optimal HA enhancement recommendation over the SOA deployment topology subject to a utility function, and produces the HA enhancement parameters for each relevant IT resource. C. HA Pattern Mapping Module Based on the optimized HA enhancement recommendation, the HA Pattern Mapping Module applies relevant HA patterns to the identified weak points. These patterns may be generic (e.g., clustering, hot standby) or product-specific (e.g., DB2 HADR — High Availability for Disaster Recovery). The goal of this module is to finally produce an HA-enhanced deployment topology that satisfies the business-level availability requirements with a minimum overall cost. In this module (see Fig. 6), each HA pattern is associated with an applicable IT resource type (e.g., a J2EE application server or a DB2 database), and provides transformation and configuration logic for applying the pattern. For each weak point identified in the IT infrastructure, a list of compatible HA patterns is generated using two matching mechanisms. The first is the applicable-type match: if the weak point is a single IT resource, then HA patterns whose applicable type