正在加载图片...
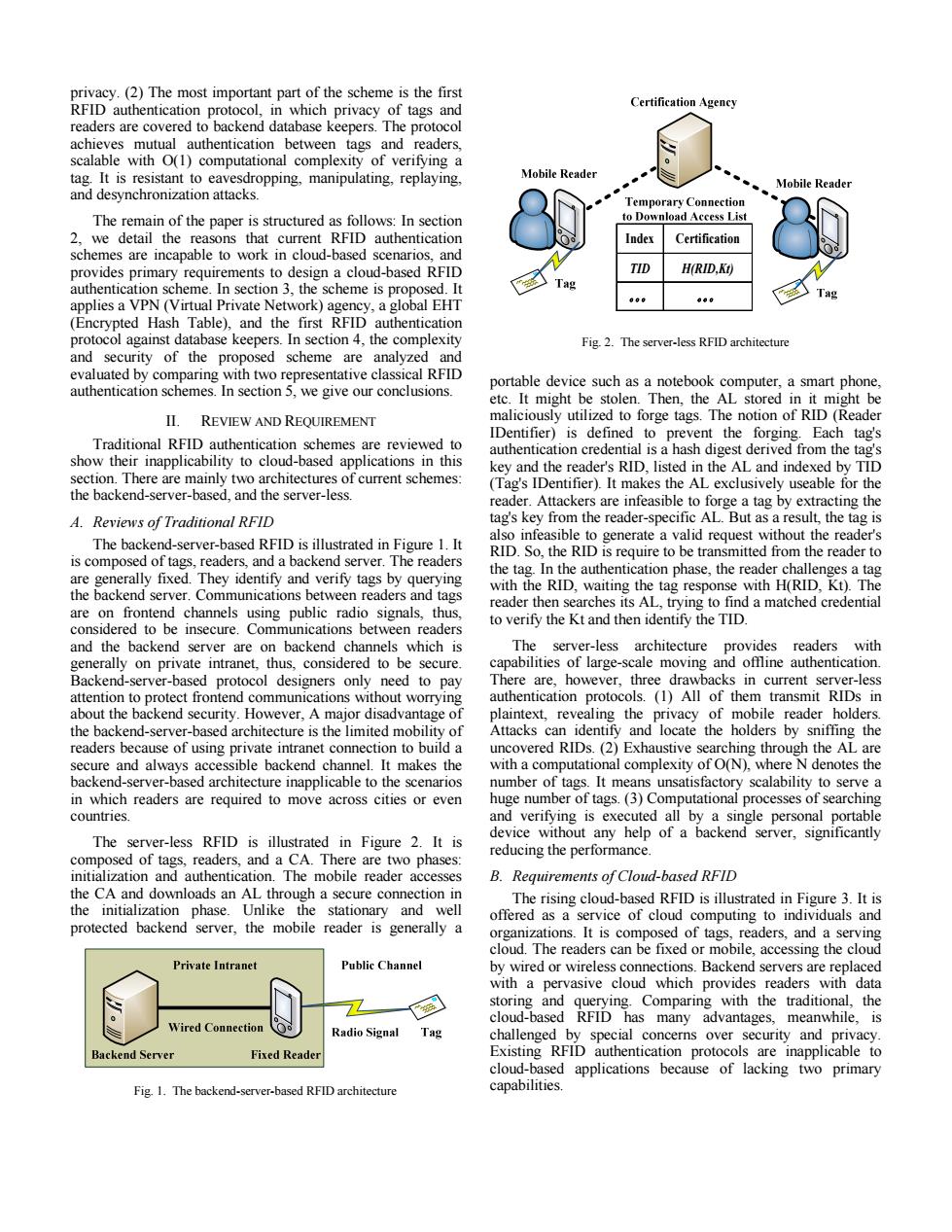
privacy.(2)The most important part of the scheme is the first RFID authentication protocol,in which privacy of tags and Certification Agency readers are covered to backend database keepers.The protocol achieves mutual authentication between tags and readers, scalable with O(1)computational complexity of verifying a tag.It is resistant to eavesdropping,manipulating,replaying, Mobile Reader Mobile Reader and desynchronization attacks. Temporary Connection The remain of the paper is structured as follows:In section to Download Access List 2.we detail the reasons that current RFID authenticatior Index Certification schemes are incapable to work in cloud-based scenarios,and provides primary requirements to design a cloud-based RFID TID H(RID,Kt) authentication scheme.In section 3,the scheme is proposed.It applies a VPN(Virtual Private Network)agency,a global EHT (Encrypted Hash Table),and the first RFID authentication protocol against database keepers.In section 4,the complexity Fig.2.The server-less RFID architecture and security of the proposed scheme are analyzed and evaluated by comparing with two representative classical RFID portable device such as a notebook computer,a smart phone. authentication schemes.In section 5,we give our conclusions. etc.It might be stolen.Then,the AL stored in it might be II.REVIEW AND REOUIREMENT maliciously utilized to forge tags.The notion of RID (Reader Traditional RFID authentication schemes are reviewed to IDentifier)is defined to prevent the forging.Each tag's authentication credential is a hash digest derived from the tag's show their inapplicability to cloud-based applications in this key and the reader's RID.listed in the AL and indexed by TID section.There are mainly two architectures of current schemes: (Tag's IDentifier).It makes the AL exclusively useable for the the backend-server-based.and the server-less. reader.Attackers are infeasible to forge a tag by extracting the A.Reviews of Traditional RFID tag's key from the reader-specific AL.But as a result,the tag is The backend-server-based RFID is illustrated in Figure 1.It also infeasible to generate a valid request without the reader's RID.So,the RID is require to be transmitted from the reader to is composed of tags,readers,and a backend server.The readers the tag.In the authentication phase,the reader challenges a tag are generally fixed.They identify and verify tags by querying the backend server.Communications between readers and tags with the RID,waiting the tag response with H(RID,Kt).The reader then searches its AL,trying to find a matched credential are on frontend channels using public radio signals,thus, to verify the Kt and then identify the TID considered to be insecure.Communications between readers and the backend server are on backend channels which is The server-less architecture provides readers with generally on private intranet,thus,considered to be secure. capabilities of large-scale moving and offline authentication. Backend-server-based protocol designers only need to pay There are,however,three drawbacks in current server-less attention to protect frontend communications without worrying authentication protocols.(1)All of them transmit RIDs in about the backend security.However,A major disadvantage of plaintext,revealing the privacy of mobile reader holders. the backend-server-based architecture is the limited mobility of Attacks can identify and locate the holders by sniffing the readers because of using private intranet connection to build a uncovered RIDs.(2)Exhaustive searching through the AL are secure and always accessible backend channel.It makes the with a computational complexity of O(N),where N denotes the backend-server-based architecture inapplicable to the scenarios number of tags.It means unsatisfactory scalability to serve a in which readers are required to move across cities or even huge number of tags.(3)Computational processes of searching countries. and verifying is executed all by a single personal portable The server-less RFID is illustrated in Figure 2.It is device without any help of a backend server,significantly composed of tags,readers,and a CA.There are two phases: reducing the performance. initialization and authentication.The mobile reader accesses B.Requirements of Cloud-based RFID the CA and downloads an AL through a secure connection in The rising cloud-based RFID is illustrated in Figure 3.It is the initialization phase.Unlike the stationary and well offered as a service of cloud computing to individuals and protected backend server,the mobile reader is generally a organizations.It is composed of tags,readers,and a serving cloud.The readers can be fixed or mobile,accessing the cloud Private Intranet Public Channel by wired or wireless connections.Backend servers are replaced with a pervasive cloud which provides readers with data storing and querying.Comparing with the traditional,the cloud-based RFID has many advantages,meanwhile,is Wired Connection Radio Signal Tag challenged by special concerns over security and privacy. Backend Server Fixed Reader Existing RFID authentication protocols are inapplicable to cloud-based applications because of lacking two primary Fig.1.The backend-server-based RFID architecture capabilities.Fig. 1. The backend-server-based RFID architecture Index Certification TID H(RID,Kt) 。。。 。。。 Fig. 2. The server-less RFID architecture privacy. (2) The most important part of the scheme is the first RFID authentication protocol, in which privacy of tags and readers are covered to backend database keepers. The protocol achieves mutual authentication between tags and readers, scalable with O(1) computational complexity of verifying a tag. It is resistant to eavesdropping, manipulating, replaying, and desynchronization attacks. The remain of the paper is structured as follows: In section 2, we detail the reasons that current RFID authentication schemes are incapable to work in cloud-based scenarios, and provides primary requirements to design a cloud-based RFID authentication scheme. In section 3, the scheme is proposed. It applies a VPN (Virtual Private Network) agency, a global EHT (Encrypted Hash Table), and the first RFID authentication protocol against database keepers. In section 4, the complexity and security of the proposed scheme are analyzed and evaluated by comparing with two representative classical RFID authentication schemes. In section 5, we give our conclusions. II. REVIEW AND REQUIREMENT Traditional RFID authentication schemes are reviewed to show their inapplicability to cloud-based applications in this section. There are mainly two architectures of current schemes: the backend-server-based, and the server-less. A. Reviews of Traditional RFID The backend-server-based RFID is illustrated in Figure 1. It is composed of tags, readers, and a backend server. The readers are generally fixed. They identify and verify tags by querying the backend server. Communications between readers and tags are on frontend channels using public radio signals, thus, considered to be insecure. Communications between readers and the backend server are on backend channels which is generally on private intranet, thus, considered to be secure. Backend-server-based protocol designers only need to pay attention to protect frontend communications without worrying about the backend security. However, A major disadvantage of the backend-server-based architecture is the limited mobility of readers because of using private intranet connection to build a secure and always accessible backend channel. It makes the backend-server-based architecture inapplicable to the scenarios in which readers are required to move across cities or even countries. The server-less RFID is illustrated in Figure 2. It is composed of tags, readers, and a CA. There are two phases: initialization and authentication. The mobile reader accesses the CA and downloads an AL through a secure connection in the initialization phase. Unlike the stationary and well protected backend server, the mobile reader is generally a portable device such as a notebook computer, a smart phone, etc. It might be stolen. Then, the AL stored in it might be maliciously utilized to forge tags. The notion of RID (Reader IDentifier) is defined to prevent the forging. Each tag's authentication credential is a hash digest derived from the tag's key and the reader's RID, listed in the AL and indexed by TID (Tag's IDentifier). It makes the AL exclusively useable for the reader. Attackers are infeasible to forge a tag by extracting the tag's key from the reader-specific AL. But as a result, the tag is also infeasible to generate a valid request without the reader's RID. So, the RID is require to be transmitted from the reader to the tag. In the authentication phase, the reader challenges a tag with the RID, waiting the tag response with H(RID, Kt). The reader then searches its AL, trying to find a matched credential to verify the Kt and then identify the TID. The server-less architecture provides readers with capabilities of large-scale moving and offline authentication. There are, however, three drawbacks in current server-less authentication protocols. (1) All of them transmit RIDs in plaintext, revealing the privacy of mobile reader holders. Attacks can identify and locate the holders by sniffing the uncovered RIDs. (2) Exhaustive searching through the AL are with a computational complexity of O(N), where N denotes the number of tags. It means unsatisfactory scalability to serve a huge number of tags. (3) Computational processes of searching and verifying is executed all by a single personal portable device without any help of a backend server, significantly reducing the performance. B. Requirements of Cloud-based RFID The rising cloud-based RFID is illustrated in Figure 3. It is offered as a service of cloud computing to individuals and organizations. It is composed of tags, readers, and a serving cloud. The readers can be fixed or mobile, accessing the cloud by wired or wireless connections. Backend servers are replaced with a pervasive cloud which provides readers with data storing and querying. Comparing with the traditional, the cloud-based RFID has many advantages, meanwhile, is challenged by special concerns over security and privacy. Existing RFID authentication protocols are inapplicable to cloud-based applications because of lacking two primary capabilities