正在加载图片...
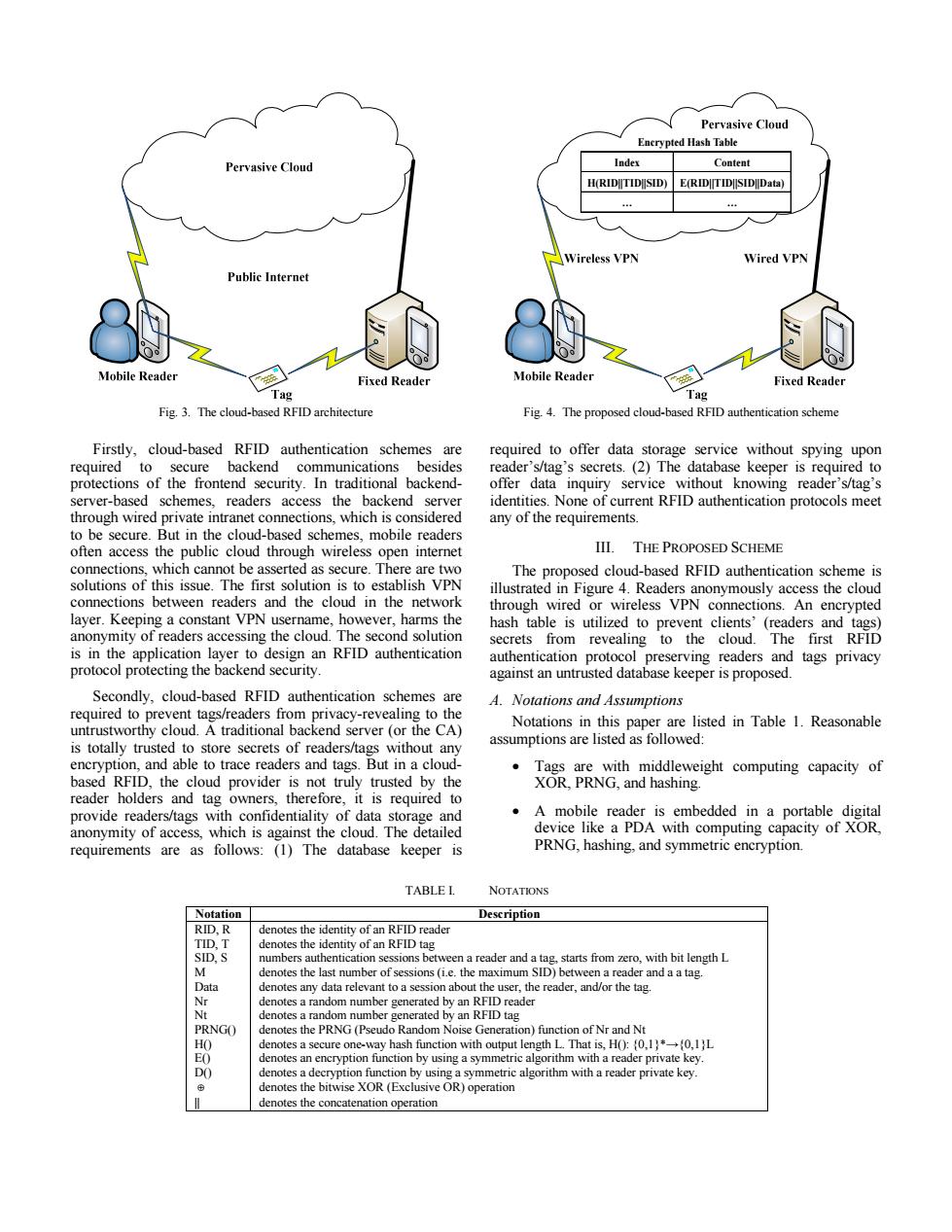
Pervasive Cloud Encrypted Hash Table Pervasive Cloud Index Content H(RIDITIDSID)E(RIDITIDSIDData) 444 Wireless VPN Wired VPN Public Internet Mobile Reader Fixed Reader Mobile Reader Fixed Reader Tag Tag Fig.3.The cloud-based RFID architecture Fig.4.The proposed cloud-based RFID authentication scheme Firstly,cloud-based RFID authentication schemes are required to offer data storage service without spying upon required to secure backend communications besides reader's/tag's secrets.(2)The database keeper is required to protections of the frontend security.In traditional backend- offer data inquiry service without knowing reader's/tag's server-based schemes.readers access the backend server identities.None of current RFID authentication protocols meet through wired private intranet connections,which is considered any of the requirements. to be secure.But in the cloud-based schemes,mobile readers often access the public cloud through wireless open internet III.THE PROPOSED SCHEME connections,which cannot be asserted as secure.There are two The proposed cloud-based RFID authentication scheme is solutions of this issue.The first solution is to establish VPN illustrated in Figure 4.Readers anonymously access the cloud connections between readers and the cloud in the network through wired or wireless VPN connections.An encrypted layer.Keeping a constant VPN username,however,harms the hash table is utilized to prevent clients'(readers and tags) anonymity of readers accessing the cloud.The second solution secrets from revealing to the cloud.The first RFID is in the application layer to design an RFID authentication authentication protocol preserving readers and tags privacy protocol protecting the backend security. against an untrusted database keeper is proposed. Secondly,cloud-based RFID authentication schemes are A.Notations and Assumptions required to prevent tags/readers from privacy-revealing to the untrustworthy cloud.A traditional backend server (or the CA) Notations in this paper are listed in Table 1.Reasonable is totally trusted to store secrets of readers/tags without any assumptions are listed as followed: encryption,and able to trace readers and tags.But in a cloud- Tags are with middleweight computing capacity of based RFID,the cloud provider is not truly trusted by the XOR,PRNG,and hashing. reader holders and tag owners,therefore,it is required to provide readers/tags with confidentiality of data storage and ● A mobile reader is embedded in a portable digital anonymity of access,which is against the cloud.The detailed device like a PDA with computing capacity of XOR, requirements are as follows:(1)The database keeper is PRNG,hashing,and symmetric encryption. TABLE I. NOTATIONS Notation Description RID,R denotes the identity of an RFID reader TID.T denotes the identity of an RFID tag SID,S numbers authentication sessions between a reader and a tag,starts from zero,with bit length L denotes the last number of sessions(i.e.the maximum SID)between a reader and a a tag. Data denotes any data relevant to a session about the user,the reader,and/or the tag. Nr denotes a random number generated by an RFID reader Nt denotes a random number generated by an RFID tag PRNGO) denotes the PRNG(Pseudo Random Noise Generation)function of Nr and Nt HO denotes a secure one-way hash function with output length L.That is,HO):(0,1)*(0,1L EO denotes an encryption function by using a symmetric algorithm with a reader private key. DO denotes a decryption function by using a symmetric algorithm with a reader private key. denotes the bitwise XOR (Exclusive OR)operation denotes the concatenation operationFig. 3. The cloud-based RFID architecture Encrypted Hash Table Index Content H(RID||TID||SID) E(RID||TID||SID||Data) … … Fig. 4. The proposed cloud-based RFID authentication scheme TABLE I. NOTATIONS Notation Description RID, R denotes the identity of an RFID reader TID, T denotes the identity of an RFID tag SID, S numbers authentication sessions between a reader and a tag, starts from zero, with bit length L M denotes the last number of sessions (i.e. the maximum SID) between a reader and a a tag. Data denotes any data relevant to a session about the user, the reader, and/or the tag. Nr denotes a random number generated by an RFID reader Nt denotes a random number generated by an RFID tag PRNG() denotes the PRNG (Pseudo Random Noise Generation) function of Nr and Nt H() denotes a secure one-way hash function with output length L. That is, H(): {0,1}*→{0,1}L E() denotes an encryption function by using a symmetric algorithm with a reader private key. D() denotes a decryption function by using a symmetric algorithm with a reader private key. ⊕ denotes the bitwise XOR (Exclusive OR) operation || denotes the concatenation operation Firstly, cloud-based RFID authentication schemes are required to secure backend communications besides protections of the frontend security. In traditional backendserver-based schemes, readers access the backend server through wired private intranet connections, which is considered to be secure. But in the cloud-based schemes, mobile readers often access the public cloud through wireless open internet connections, which cannot be asserted as secure. There are two solutions of this issue. The first solution is to establish VPN connections between readers and the cloud in the network layer. Keeping a constant VPN username, however, harms the anonymity of readers accessing the cloud. The second solution is in the application layer to design an RFID authentication protocol protecting the backend security. Secondly, cloud-based RFID authentication schemes are required to prevent tags/readers from privacy-revealing to the untrustworthy cloud. A traditional backend server (or the CA) is totally trusted to store secrets of readers/tags without any encryption, and able to trace readers and tags. But in a cloudbased RFID, the cloud provider is not truly trusted by the reader holders and tag owners, therefore, it is required to provide readers/tags with confidentiality of data storage and anonymity of access, which is against the cloud. The detailed requirements are as follows: (1) The database keeper is required to offer data storage service without spying upon reader’s/tag’s secrets. (2) The database keeper is required to offer data inquiry service without knowing reader’s/tag’s identities. None of current RFID authentication protocols meet any of the requirements. III. THE PROPOSED SCHEME The proposed cloud-based RFID authentication scheme is illustrated in Figure 4. Readers anonymously access the cloud through wired or wireless VPN connections. An encrypted hash table is utilized to prevent clients’ (readers and tags) secrets from revealing to the cloud. The first RFID authentication protocol preserving readers and tags privacy against an untrusted database keeper is proposed. A. Notations and Assumptions Notations in this paper are listed in Table 1. Reasonable assumptions are listed as followed: • Tags are with middleweight computing capacity of XOR, PRNG, and hashing. • A mobile reader is embedded in a portable digital device like a PDA with computing capacity of XOR, PRNG, hashing, and symmetric encryption