正在加载图片...
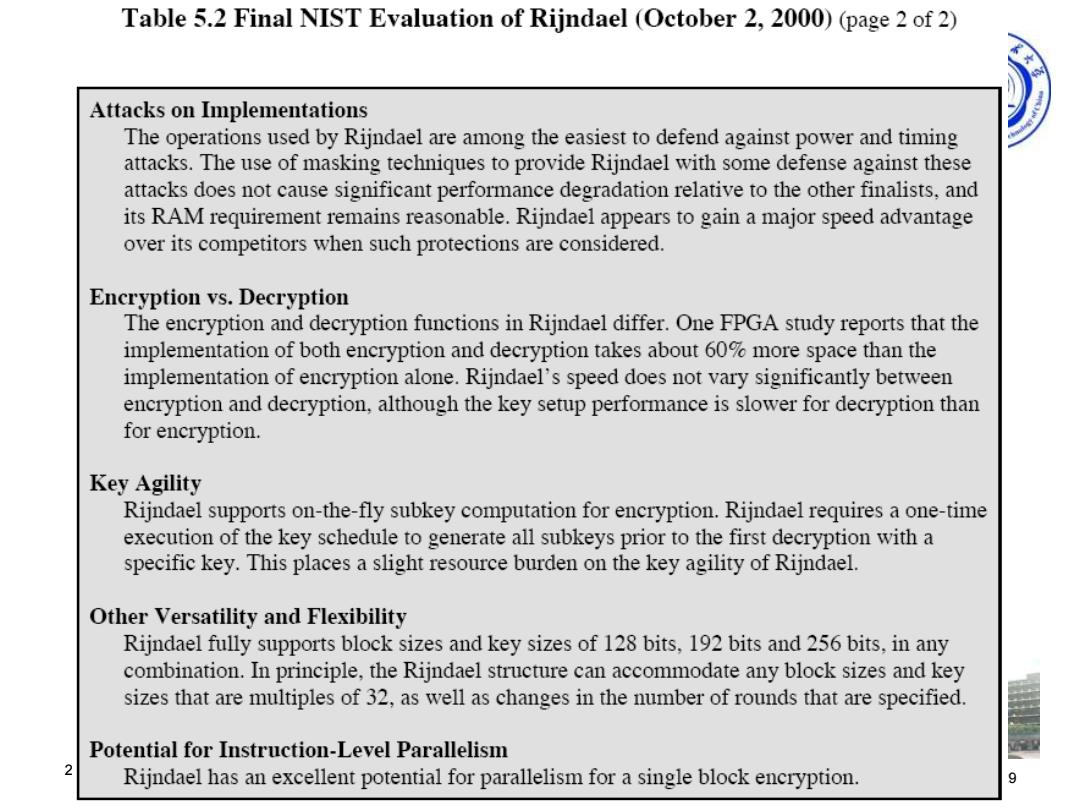
Table 5.2 Final NIST Evaluation of Rijndael (October 2,2000)(page 2 of 2) Attacks on Implementations The operations used by Rijndael are among the easiest to defend against power and timing attacks.The use of masking techniques to provide Rijndael with some defense against these attacks does not cause significant performance degradation relative to the other finalists,and its RAM requirement remains reasonable.Rijndael appears to gain a major speed advantage over its competitors when such protections are considered. Encryption vs.Decryption The encryption and decryption functions in Rijndael differ.One FPGA study reports that the implementation of both encryption and decryption takes about 60%more space than the implementation of encryption alone.Rijndael's speed does not vary significantly between encryption and decryption,although the key setup performance is slower for decryption than for encryption. Key Agility Rijndael supports on-the-fly subkey computation for encryption.Rijndael requires a one-time execution of the key schedule to generate all subkeys prior to the first decryption with a specific key.This places a slight resource burden on the key agility of Rijndael. Other Versatility and Flexibility Rijndael fully supports block sizes and key sizes of 128 bits,192 bits and 256 bits,in any combination.In principle,the Rijndael structure can accommodate any block sizes and key sizes that are multiples of 32,as well as changes in the number of rounds that are specified. Potential for Instruction-Level Parallelism Rijndael has an excellent potential for parallelism for a single block encryption.2022/10/9 现代密码学理论与实践05 9/29