
高级加密标准AES要点 15 AES是一种分组密码,用以取代DES的商业应用。 其分组长度为128位,密钥长度为128位、192位 或256位。 ·AES没有使用Feistel结构,每轮由四个独立的运 算组成:字节代换、置换、有限域上的算术运算, 以及与密钥的异或运算。 平四 2022/10/9 现代密码学理论与实践05 2/29
2022/10/9 现代密码学理论与实践05 2/29 高级加密标准AES要点 ⚫ AES是一种分组密码,用以取代DES的商业应用。 其分组长度为128位,密钥长度为128位、192位 或256位。 ⚫ AES没有使用Feistel结构,每轮由四个独立的运 算组成:字节代换、置换、有限域上的算术运算, 以及与密钥的异或运算

AES的评估准则 15 ●AES的起源 因为DES的不安全,建议用3DES,: 密钥168位 抵御密码分析攻击。但是3DES用软件实现速度较 慢,分组短,仅64位。 美国国家标准技术协会NIST在1997年征集新标准, 要求分组128位,密钥128、192或256位。 15种候选算法在1998年6月通过了第一轮评估,仅 有5个候选算法在1999年8月通过了第二轮评估。 ● 2000年10月,NIST选择Riindael作为AES算法, Rijndael的作者是比利时的密码学家Joan Daemen 博士和Vincent Rijment博士。 2001年11月,NIST完成评估并发布了最终标准 FIPS PUB197。 nn量 2022/10/9 现代密码学理论与实践05 3/29
2022/10/9 现代密码学理论与实践05 3/29 AES的评估准则 ⚫ AES的起源 ⚫ 因为DES的不安全,建议用3DES,密钥168位, 抵御密码分析攻击。但是3DES用软件实现速度较 慢,分组短,仅64位。 ⚫ 美国国家标准技术协会NIST在1997年征集新标准, 要求分组128位,密钥128、192或256位。 ⚫ 15种候选算法在1998年6月通过了第一轮评估,仅 有5个候选算法在1999年8月通过了第二轮评估。 ⚫ 2000年10月,NIST选择Rijndael作为AES算法, Rijndael的作者是比利时的密码学家Joan Daemen 博士和Vincent Rijmen博士。 ⚫ 2001年11月,NIST完成评估并发布了最终标准 FIPS PUB 197

车太 AES的评估 1950 ·AES评估准则的三大类别 。安全性:指密码分析方法分析一个算法所需的代价 ● 成本:期望AES能够广泛应用于各种实际应用,计 算效率要高 算法和执行特征:算法灵活性、适合于多种硬件和 软件方式的实现、简洁性,便于分析安全性 平N里 2022/10/9 现代密码学理论与实践05 4/29
2022/10/9 现代密码学理论与实践05 4/29 AES的评估 ⚫ AES评估准则的三大类别 ⚫ 安全性:指密码分析方法分析一个算法所需的代价 ⚫ 成本:期望AES能够广泛应用于各种实际应用,计 算效率要高 ⚫ 算法和执行特征:算法灵活性、适合于多种硬件和 软件方式的实现、简洁性,便于分析安全性

Table 5.1 NIST Evaluation Criteria for AES(September 12,1997)(page 1 of 2) SECURITY .Actual security:compared to other submitted algorithms(at the same key and block size). .Randomness:The extent to which the algorithm output is indistinguishable from a random permutation on the input block. .Soundness:of the mathematical basis for the algorithm's security. .Other security factors:raised by the public during the evaluation process,including any attacks which demonstrate that the actual security of the algorithm is less than the strength claimed by the submitter. COST .Licensing requirements:NIST intends that when the AES is issued,the algorithm(s) specified in the AES shall be available on a worldwide,non-exclusive,royalty-free basis. .Computational efficiency:The evaluation of computational efficiency will be applicable to both hardware and software implementations.Round 1 analysis by NIST will focus primarily on software implementations and specifically on one key-block size combination (128-128);more attention will be paid to hardware implementations and other supported key-block size combinations during Round 2 analysis.Computational efficiency essentially refers to the speed of the algorithm.Public comments on each algorithm's efficiency (particularly for various platforms and applications)will also be taken into consideration by NIST. .Memory requirements:The memory required to implement a candidate algorithm--for both hardware and software implementations of the algorithm--will also be considered during the evaluation process.Round 1 analysis by NIST will focus primarily on software implementations;more attention will be paid to hardware implementations during Round 2. 2022/10/1 Memory requirements will include such factors as gate counts for hardware implementations,and code size and RAM requirements for software implementations. 5/29
2022/10/9 现代密码学理论与实践05 5/29
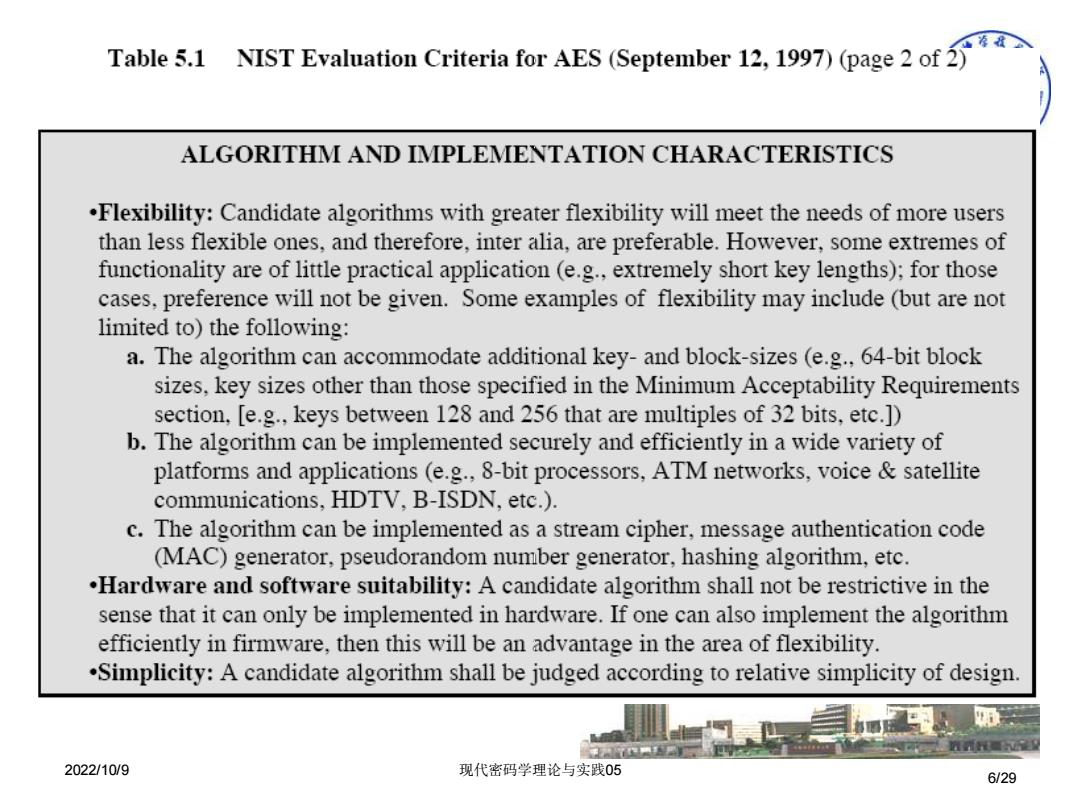
Table 5.1 NIST Evaluation Criteria for AES(September 12,1997)(page 2of ALGORITHM AND IMPLEMENTATION CHARACTERISTICS .Flexibility:Candidate algorithms with greater flexibility will meet the needs of more users than less flexible ones,and therefore,inter alia,are preferable.However,some extremes of functionality are of little practical application(e.g.,extremely short key lengths);for those cases,preference will not be given.Some examples of flexibility may include (but are not limited to)the following: a.The algorithm can accommodate additional key-and block-sizes (e.g.,64-bit block sizes,key sizes other than those specified in the Minimum Acceptability Requirements section,[e.g.,keys between 128 and 256 that are multiples of 32 bits,etc.] b.The algorithm can be implemented securely and efficiently in a wide variety of platforms and applications (e.g.,8-bit processors,ATM networks,voice satellite communications,HDTV,B-ISDN,etc.). c.The algorithm can be implemented as a stream cipher,message authentication code (MAC)generator,pseudorandom number generator,hashing algorithm,etc. .Hardware and software suitability:A candidate algorithm shall not be restrictive in the sense that it can only be implemented in hardware.If one can also implement the algorithm efficiently in firmware,then this will be an advantage in the area of flexibility. .Simplicity:A candidate algorithm shall be judged according to relative simplicity of design 2022/10/9 现代密码学理论与实践05 6/29
2022/10/9 现代密码学理论与实践05 6/29

AES评估准 车 15 一 般安全性 依赖于密码学界的公共安全分析 软件实现 。软件执行速度, 跨平台执行能力及密钥长度改变时速度变化 ● 受限空间环境 。在诸如智能卡中的应用 ● 硬件实现 硬件执行提高执行速度或缩短代码长度 对执行的攻击 。抵御密码分析攻击 加密与解密 ● 密钥灵活性 。快速改变密钥长度的能力 其他的多功能性和灵活性 ● 指令级并行执行的潜力 题三 平四 2022/10/9 现代密码学理论与实践05 7/29
2022/10/9 现代密码学理论与实践05 7/29 AES评估准则 ⚫ 一般安全性 ⚫ 依赖于密码学界的公共安全分析 ⚫ 软件实现 ⚫ 软件执行速度,跨平台执行能力及密钥长度改变时速度变化 ⚫ 受限空间环境 ⚫ 在诸如智能卡中的应用 ⚫ 硬件实现 ⚫ 硬件执行提高执行速度或缩短代码长度 ⚫ 对执行的攻击 ⚫ 抵御密码分析攻击 ⚫ 加密与解密 ⚫ 密钥灵活性 ⚫ 快速改变密钥长度的能力 ⚫ 其他的多功能性和灵活性 ⚫ 指令级并行执行的潜力

Table 5.2 Final NIST Evaluation of Riindael (October 2,2000)(page 1 of 2) General Security Rijndael has no known security attacks.Rijndael uses S-boxes as nonlinear components. Rijndael appears to have an adequate security margin,but has received some criticism suggesting that its mathematical structure may lead to attacks.On the other hand,the simple structure may have facilitated its security analysis during the timeframe of the AES development process. Software Implementations Rijndael performs encryption and decryption very well across a variety of platforms, including 8-bit and 64-bit platforms,and DSPs.However,there is a decrease in performance with the higher key sizes because of the increased number of rounds that are performed. Rijndael's high inherent parallelism facilitates the efficient use of processor resources, resulting in very good software performance even when implemented in a mode not capable of interleaving.Rijndael's key setup time is fast. Restricted-Space Environments In general,Rijndael is very well suited for restricted-space environments where either encryption or decryption is implemented(but not both).It has very low RAM and ROM requirements.A drawback is that ROM requirements will increase if both encryption and decryption are implemented simultaneously,although it appears to remain suitable for these environments.The key schedule for decryption is separate from encryption. Hardware Implementations Rijndael has the highest throughput of any of the finalists for feedback modes and second highest for non-feedback modes.For the 192 and 256-bit key sizes,throughput falls in standard and unrolled implementations because of the additional number of rounds.For fully pipelined implementations,the area requirement increases,but the throughput is unaffected. 8/29
2022/10/9 现代密码学理论与实践05 8/29
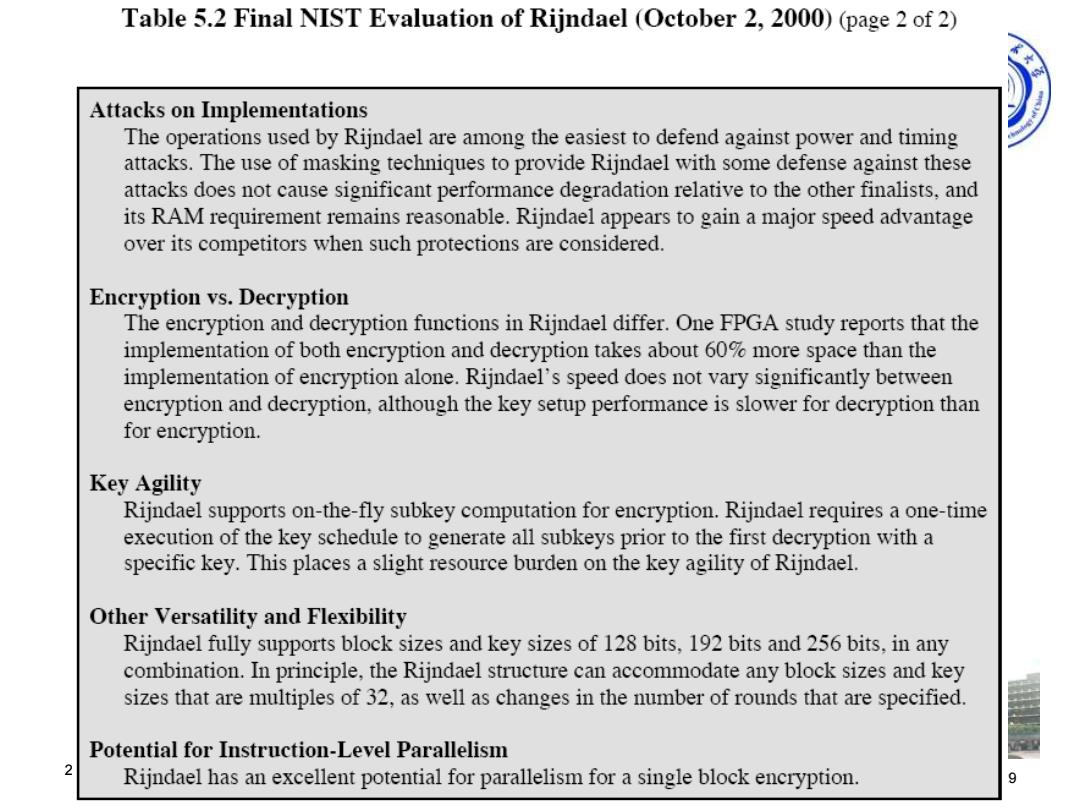
Table 5.2 Final NIST Evaluation of Rijndael (October 2,2000)(page 2 of 2) Attacks on Implementations The operations used by Rijndael are among the easiest to defend against power and timing attacks.The use of masking techniques to provide Rijndael with some defense against these attacks does not cause significant performance degradation relative to the other finalists,and its RAM requirement remains reasonable.Rijndael appears to gain a major speed advantage over its competitors when such protections are considered. Encryption vs.Decryption The encryption and decryption functions in Rijndael differ.One FPGA study reports that the implementation of both encryption and decryption takes about 60%more space than the implementation of encryption alone.Rijndael's speed does not vary significantly between encryption and decryption,although the key setup performance is slower for decryption than for encryption. Key Agility Rijndael supports on-the-fly subkey computation for encryption.Rijndael requires a one-time execution of the key schedule to generate all subkeys prior to the first decryption with a specific key.This places a slight resource burden on the key agility of Rijndael. Other Versatility and Flexibility Rijndael fully supports block sizes and key sizes of 128 bits,192 bits and 256 bits,in any combination.In principle,the Rijndael structure can accommodate any block sizes and key sizes that are multiples of 32,as well as changes in the number of rounds that are specified. Potential for Instruction-Level Parallelism Rijndael has an excellent potential for parallelism for a single block encryption
2022/10/9 现代密码学理论与实践05 9/29

◆养不 NIST对AES的要求 15 。对称密钥分组密码 ·128位分组,密钥长度可以分别是128/192/256位 ·要求比Triple-DES更安全和更快 ·至少能够安全工作20-30年 ·提供完整的规范说明和设计细节 ·能够用C或Java实现 NIST公布了所有提交的算法和不保密的分析资料, 最终通过评估,选择了Riindael 甲A四两 2022/10/9 现代密码学理论与实践05 10/29
2022/10/9 现代密码学理论与实践05 10/29 NIST对AES的要求 ⚫ 对称密钥分组密码 ⚫ 128位分组,密钥长度可以分别是128/192/256位 ⚫ 要求比Triple-DES更安全和更快 ⚫ 至少能够安全工作20-30年 ⚫ 提供完整的规范说明和设计细节 ⚫ 能够用C或Java实现 ⚫ NIST公布了所有提交的算法和不保密的分析资料, 最终通过评估,选择了Rijndael

车长 AES密码 15 ·AES的分组长度为128位,密钥长度可以是 128/192/256的任意一种 ·未采用Feistel密码结构而是用迭代方式 。数据分成4组,每组4字节 ·每一轮对整个分组进行操作 ·Riindael具有如下特性 对所有已知的攻击具有免疫性 在各种CPU平台上其执行速度快且代码紧凑 设计简单 甲A四两 2022/10/9 现代密码学理论与实践05 11/29
2022/10/9 现代密码学理论与实践05 11/29 AES密码 ⚫ AES的分组长度为128位,密钥长度可以是 128/192/256的任意一种 ⚫ 未采用Feistel密码结构而是用迭代方式 ⚫ 数据分成4组,每组4字节 ⚫ 每一轮对整个分组进行操作 ⚫ Rijndael具有如下特性 ⚫ 对所有已知的攻击具有免疫性 ⚫ 在各种CPU平台上其执行速度快且代码紧凑 ⚫ 设计简单