正在加载图片...
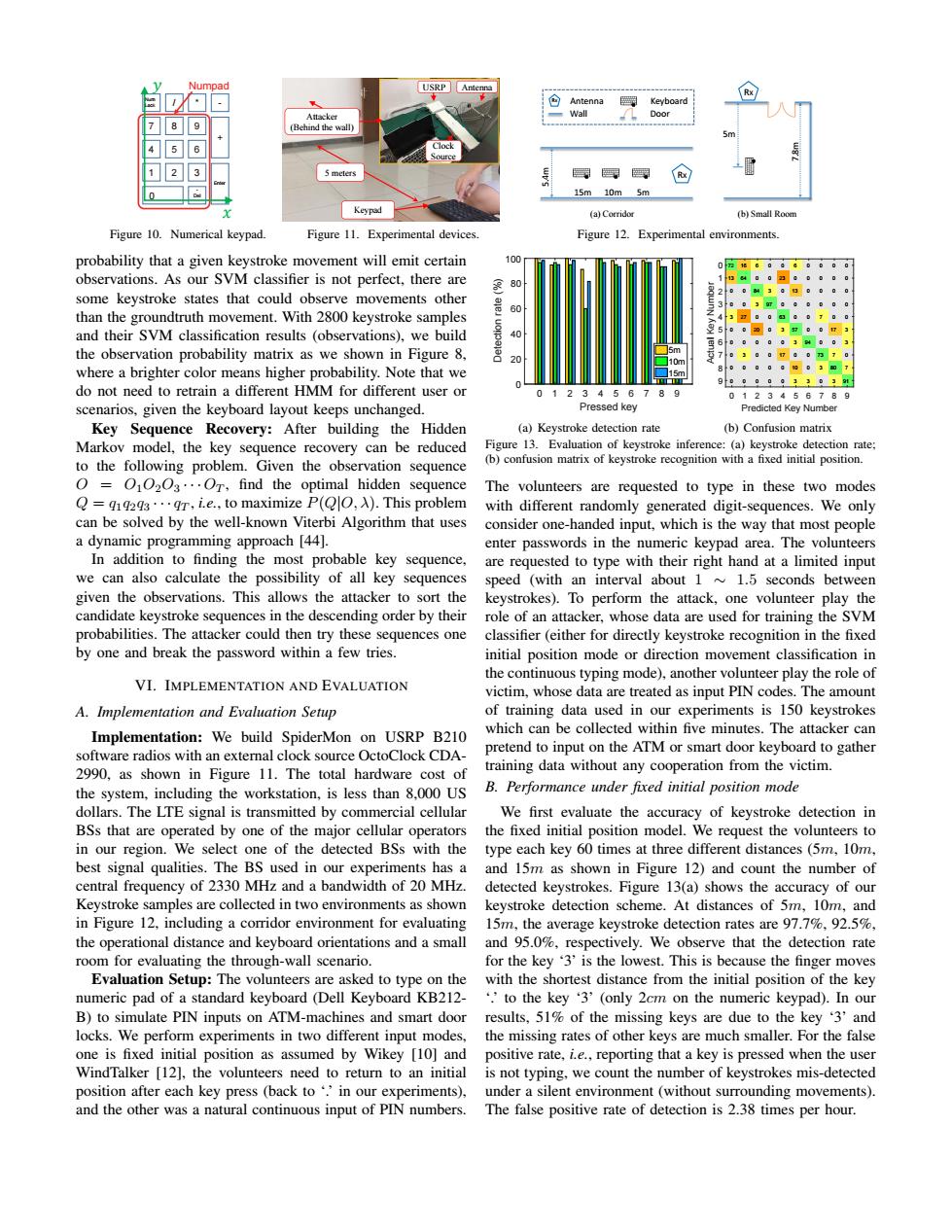
USRP Antenn Antenna Keyboard Wall Door (Behind the wall) 5 meters 骨受受 15m10m5m Keypad (b)Small Room Figure 10.Numerical keypad. Figure 11.Experimental devices. Figure 12.Experimental environments. probability that a given keystroke movement will emit certain 100 0 observations.As our SVM classifier is not perfect,there are 0 0 多 some keystroke states that could observe movements other than the groundtruth movement.With 2800 keystroke samples and their SVM classification results (observations),we build the observation probability matrix as we shown in Figure 8. where a brighter color means higher probability.Note that we 3 do not need to retrain a different HMM for different user or 2 345678 0123456789 scenarios,given the keyboard layout keeps unchanged. Pressed kev Predicted Key Number Key Sequence Recovery:After building the Hidden (a)Keystroke detection rate (b)Confusion matrix Markov model,the key sequence recovery can be reduced Figure 13.Evaluation of keystroke inference:(a)keystroke detection rate: to the following problem.Given the observation sequence (b)confusion matrix of keystroke recognition with a fixed initial position. 0 010203...Or,find the optimal hidden sequence The volunteers are requested to type in these two modes Q=g1q293...gr,i.e.,to maximize P(QO,A).This problem with different randomly generated digit-sequences.We only can be solved by the well-known Viterbi Algorithm that uses consider one-handed input,which is the way that most people a dynamic programming approach [44]. enter passwords in the numeric keypad area.The volunteers In addition to finding the most probable key sequence, are requested to type with their right hand at a limited input we can also calculate the possibility of all key sequences speed (with an interval about 1 ~1.5 seconds between given the observations.This allows the attacker to sort the keystrokes).To perform the attack,one volunteer play the candidate keystroke sequences in the descending order by their role of an attacker,whose data are used for training the SVM probabilities.The attacker could then try these sequences one classifier (either for directly keystroke recognition in the fixed by one and break the password within a few tries. initial position mode or direction movement classification in the continuous typing mode),another volunteer play the role of VI.IMPLEMENTATION AND EVALUATION victim,whose data are treated as input PIN codes.The amount A.Implementation and Evaluation Setup of training data used in our experiments is 150 keystrokes Implementation:We build SpiderMon on USRP B210 which can be collected within five minutes.The attacker can software radios with an external clock source OctoClock CDA- pretend to input on the ATM or smart door keyboard to gather 2990,as shown in Figure 11.The total hardware cost of training data without any cooperation from the victim. the system,including the workstation,is less than 8,000 US B.Performance under fixed initial position mode dollars.The LTE signal is transmitted by commercial cellular We first evaluate the accuracy of keystroke detection in BSs that are operated by one of the major cellular operators the fixed initial position model.We request the volunteers to in our region.We select one of the detected BSs with the type each key 60 times at three different distances(5m,10m, best signal qualities.The BS used in our experiments has a and 15m as shown in Figure 12)and count the number of central frequency of 2330 MHz and a bandwidth of 20 MHz. detected keystrokes.Figure 13(a)shows the accuracy of our Keystroke samples are collected in two environments as shown keystroke detection scheme.At distances of 5m,10m,and in Figure 12.including a corridor environment for evaluating 15m,the average keystroke detection rates are 97.7%.92.5% the operational distance and keyboard orientations and a small and 95.0%,respectively.We observe that the detection rate room for evaluating the through-wall scenario. for the key '3'is the lowest.This is because the finger moves Evaluation Setup:The volunteers are asked to type on the with the shortest distance from the initial position of the key numeric pad of a standard keyboard (Dell Keyboard KB212- .to the key '3'(only 2cm on the numeric keypad).In our B)to simulate PIN inputs on ATM-machines and smart door results,51%of the missing keys are due to the key '3'and locks.We perform experiments in two different input modes, the missing rates of other keys are much smaller.For the false one is fixed initial position as assumed by Wikey [10]and positive rate,i.e.,reporting that a key is pressed when the user WindTalker [12],the volunteers need to return to an initial is not typing,we count the number of keystrokes mis-detected position after each key press (back to'in our experiments). under a silent environment(without surrounding movements). and the other was a natural continuous input of PIN numbers. The false positive rate of detection is 2.38 times per hour.4 5 6 1 2 3 7 8 9 / * - + . 0 Del Numpad ݔ ݕ Num Lock Enter Figure 10. Numerical keypad. 5 meters Attacker (Behind the wall) Keypad USRP Antenna Clock Source Figure 11. Experimental devices. Rx 15m 10m 5m 5.4m 5m 7.8m Rx Rx Antenna Wall Keyboard Door (a) Corridor (b) Small Room Figure 12. Experimental environments. probability that a given keystroke movement will emit certain observations. As our SVM classifier is not perfect, there are some keystroke states that could observe movements other than the groundtruth movement. With 2800 keystroke samples and their SVM classification results (observations), we build the observation probability matrix as we shown in Figure 8, where a brighter color means higher probability. Note that we do not need to retrain a different HMM for different user or scenarios, given the keyboard layout keeps unchanged. Key Sequence Recovery: After building the Hidden Markov model, the key sequence recovery can be reduced to the following problem. Given the observation sequence O = O1O2O3 · · · OT , find the optimal hidden sequence Q = q1q2q3 · · · qT , i.e., to maximize P(Q|O, λ). This problem can be solved by the well-known Viterbi Algorithm that uses a dynamic programming approach [44]. In addition to finding the most probable key sequence, we can also calculate the possibility of all key sequences given the observations. This allows the attacker to sort the candidate keystroke sequences in the descending order by their probabilities. The attacker could then try these sequences one by one and break the password within a few tries. VI. IMPLEMENTATION AND EVALUATION A. Implementation and Evaluation Setup Implementation: We build SpiderMon on USRP B210 software radios with an external clock source OctoClock CDA- 2990, as shown in Figure 11. The total hardware cost of the system, including the workstation, is less than 8,000 US dollars. The LTE signal is transmitted by commercial cellular BSs that are operated by one of the major cellular operators in our region. We select one of the detected BSs with the best signal qualities. The BS used in our experiments has a central frequency of 2330 MHz and a bandwidth of 20 MHz. Keystroke samples are collected in two environments as shown in Figure 12, including a corridor environment for evaluating the operational distance and keyboard orientations and a small room for evaluating the through-wall scenario. Evaluation Setup: The volunteers are asked to type on the numeric pad of a standard keyboard (Dell Keyboard KB212- B) to simulate PIN inputs on ATM-machines and smart door locks. We perform experiments in two different input modes, one is fixed initial position as assumed by Wikey [10] and WindTalker [12], the volunteers need to return to an initial position after each key press (back to ‘.’ in our experiments), and the other was a natural continuous input of PIN numbers. 0123456789 Pressed key 0 20 40 60 80 100 Detection rate (%) 5m 10m 15m (a) Keystroke detection rate 7216 6 0 0 6 0 0 0 0 1364 0 0 23 0 0 0 0 0 0 0 84 3 0 13 0 0 0 0 0 0 3 97 0 0 0 0 0 0 3 27 0 0 63 0 0 7 0 0 0 0 20 0 3 57 0 0 17 3 0 0 0 0 0 3 94 0 0 3 0 3 0 0 17 0 0 73 7 0 0 0 0 0 0 10 0 3 80 7 0 0 0 0 0 3 3 0 3 91 0123456789 Predicted Key Number 0 1 2 3 4 5 6 7 8 9 Actual Key Number (b) Confusion matrix Figure 13. Evaluation of keystroke inference: (a) keystroke detection rate; (b) confusion matrix of keystroke recognition with a fixed initial position. The volunteers are requested to type in these two modes with different randomly generated digit-sequences. We only consider one-handed input, which is the way that most people enter passwords in the numeric keypad area. The volunteers are requested to type with their right hand at a limited input speed (with an interval about 1 ∼ 1.5 seconds between keystrokes). To perform the attack, one volunteer play the role of an attacker, whose data are used for training the SVM classifier (either for directly keystroke recognition in the fixed initial position mode or direction movement classification in the continuous typing mode), another volunteer play the role of victim, whose data are treated as input PIN codes. The amount of training data used in our experiments is 150 keystrokes which can be collected within five minutes. The attacker can pretend to input on the ATM or smart door keyboard to gather training data without any cooperation from the victim. B. Performance under fixed initial position mode We first evaluate the accuracy of keystroke detection in the fixed initial position model. We request the volunteers to type each key 60 times at three different distances (5m, 10m, and 15m as shown in Figure 12) and count the number of detected keystrokes. Figure 13(a) shows the accuracy of our keystroke detection scheme. At distances of 5m, 10m, and 15m, the average keystroke detection rates are 97.7%, 92.5%, and 95.0%, respectively. We observe that the detection rate for the key ‘3’ is the lowest. This is because the finger moves with the shortest distance from the initial position of the key ‘.’ to the key ‘3’ (only 2cm on the numeric keypad). In our results, 51% of the missing keys are due to the key ‘3’ and the missing rates of other keys are much smaller. For the false positive rate, i.e., reporting that a key is pressed when the user is not typing, we count the number of keystrokes mis-detected under a silent environment (without surrounding movements). The false positive rate of detection is 2.38 times per hour