正在加载图片...
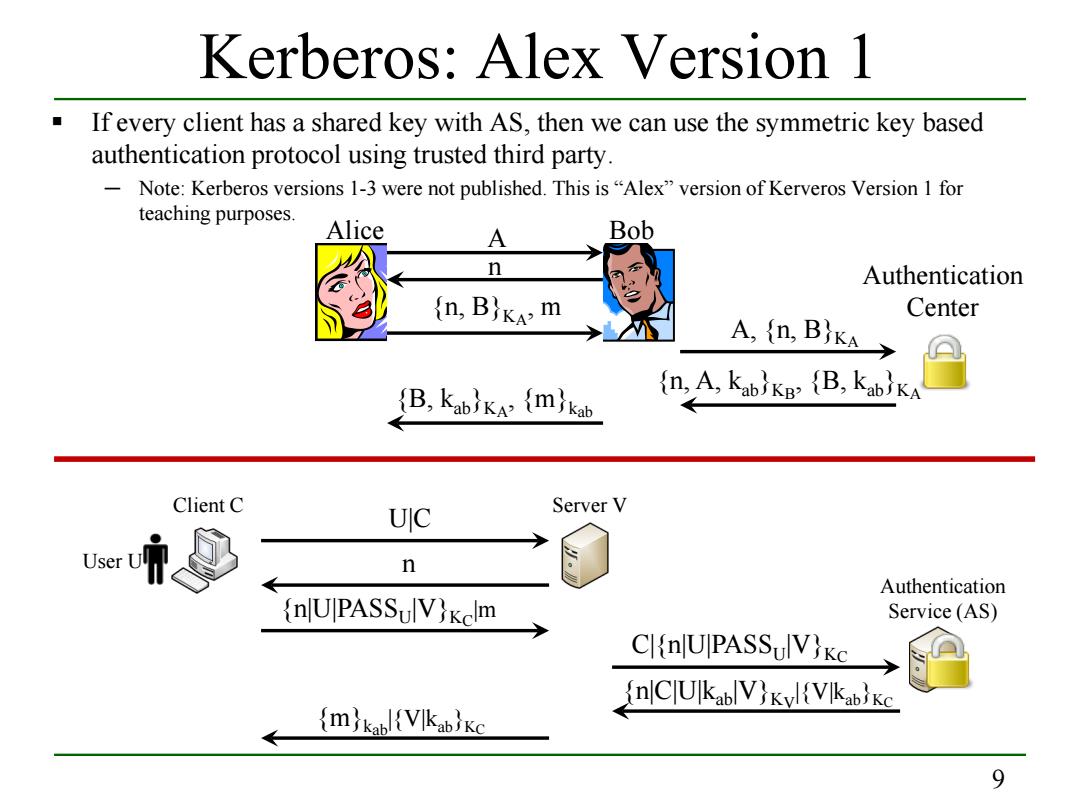
Kerberos:Alex Version 1 If every client has a shared key with AS,then we can use the symmetric key based authentication protocol using trusted third party. Note:Kerberos versions 1-3 were not published.This is"Alex"version of Kerveros Version 1 for teaching purposes. Alice A Bob n Authentication (n,B)KA:m Center A,{,BKA→ (B,KabKa (mkab (n,A,kablkB (B,kabika Client C UIC Server V User n Authentication (nJUPASSulV}Kclm Service(AS) ClinlUIPASSulV)Kc nlClUlkablV}Kyl(Vlkabke (m)kabl{VIkabKc 99 Kerberos: Alex Version 1 If every client has a shared key with AS, then we can use the symmetric key based authentication protocol using trusted third party. ─ Note: Kerberos versions 1-3 were not published. This is “Alex” version of Kerveros Version 1 for teaching purposes. Client C Server V User U Authentication {n|U|PASSU|V}K Service (AS) C|m U|C n C|{n|U|PASSU|V}KC {n|C|U|kab|V}KV|{V|kab}KC {m}kab|{V|kab}KC Alice A Bob n {n, B}KA, m A, {n, B}KA {n, A, kab}KB, {B, kab}KA Authentication Center {B, kab}KA, {m}kab