正在加载图片...
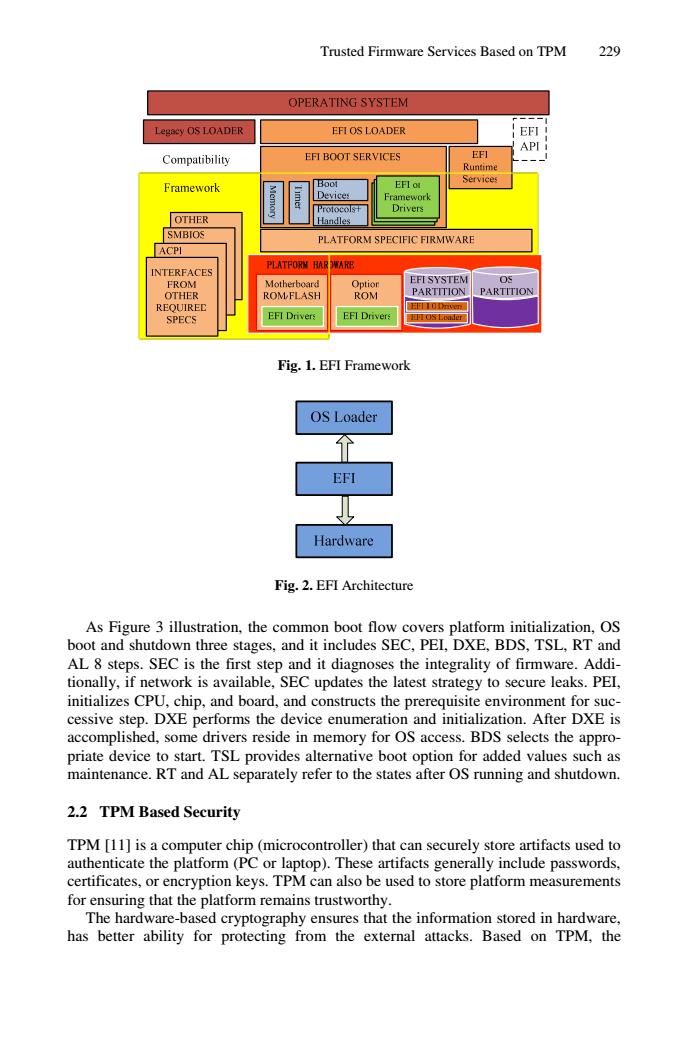
Trusted Firmware Services Based on TPM 229 OPERATING SYSTEM Legacy OS LOADER EFI OS LOADER EFI API Compatibility EFI BOOT SERVICES EFI Runtime Services Framework Boot EFI ot Devices Framework Drivers OTHER Handles SMBIOS PLATFORM SPECIFIC FIRMWARE ACPI INTERFACES 刊ATFORM HAR DWARE FROM Motherboard Option EFI SYSTEM 05 OTHER ROM FLASH ROM PARTITION PARTITION REQUIREC SPECS EFI Drivers EFI Drivers EI OS Loader Fig.1.EFI Framework OS Loader EFI Hardware Fig.2.EFI Architecture As Figure 3 illustration,the common boot flow covers platform initialization,OS boot and shutdown three stages,and it includes SEC,PEL,DXE,BDS,TSL,RT and AL 8 steps.SEC is the first step and it diagnoses the integrality of firmware.Addi- tionally,if network is available,SEC updates the latest strategy to secure leaks.PEI, initializes CPU,chip,and board,and constructs the prerequisite environment for suc- cessive step.DXE performs the device enumeration and initialization.After DXE is accomplished,some drivers reside in memory for OS access.BDS selects the appro- priate device to start.TSL provides alternative boot option for added values such as maintenance.RT and AL separately refer to the states after OS running and shutdown. 2.2 TPM Based Security TPM [11]is a computer chip (microcontroller)that can securely store artifacts used to authenticate the platform (PC or laptop).These artifacts generally include passwords, certificates,or encryption keys.TPM can also be used to store platform measurements for ensuring that the platform remains trustworthy. The hardware-based cryptography ensures that the information stored in hardware, has better ability for protecting from the external attacks.Based on TPM,theTrusted Firmware Services Based on TPM 229 Fig. 1. EFI Framework Fig. 2. EFI Architecture As Figure 3 illustration, the common boot flow covers platform initialization, OS boot and shutdown three stages, and it includes SEC, PEI, DXE, BDS, TSL, RT and AL 8 steps. SEC is the first step and it diagnoses the integrality of firmware. Additionally, if network is available, SEC updates the latest strategy to secure leaks. PEI, initializes CPU, chip, and board, and constructs the prerequisite environment for successive step. DXE performs the device enumeration and initialization. After DXE is accomplished, some drivers reside in memory for OS access. BDS selects the appropriate device to start. TSL provides alternative boot option for added values such as maintenance. RT and AL separately refer to the states after OS running and shutdown. 2.2 TPM Based Security TPM [11] is a computer chip (microcontroller) that can securely store artifacts used to authenticate the platform (PC or laptop). These artifacts generally include passwords, certificates, or encryption keys. TPM can also be used to store platform measurements for ensuring that the platform remains trustworthy. The hardware-based cryptography ensures that the information stored in hardware, has better ability for protecting from the external attacks. Based on TPM, the