正在加载图片...
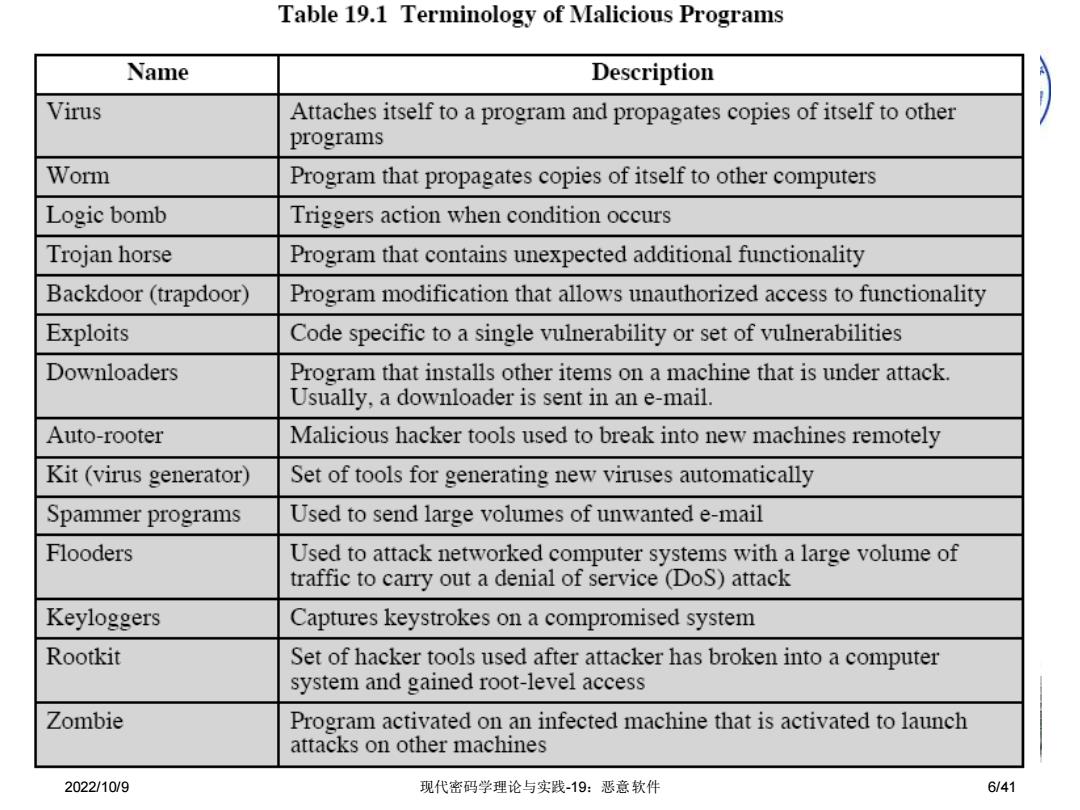
Table 19.1 Terminology of Malicious Programs Name Description Virus Attaches itself to a program and propagates copies of itself to other programs Worm Program that propagates copies of itself to other computers Logic bomb Triggers action when condition occurs Trojan horse Program that contains unexpected additional functionality Backdoor (trapdoor) Program modification that allows unauthorized access to functionality Exploits Code specific to a single vulnerability or set of vulnerabilities Downloaders Program that installs other items on a machine that is under attack. Usually,a downloader is sent in an e-mail. Auto-rooter Malicious hacker tools used to break into new machines remotely Kit(virus generator) Set of tools for generating new viruses automatically Spammer programs Used to send large volumes of unwanted e-mail Flooders Used to attack networked computer systems with a large volume of traffic to carry out a denial of service (DoS)attack Keyloggers Captures keystrokes on a compromised system Rootkit Set of hacker tools used after attacker has broken into a computer system and gained root-level access Zombie Program activated on an infected machine that is activated to launch attacks on other machines 2022/10/9 现代密码学理论与实践-19:恶意软件 6/412022/10/9 现代密码学理论与实践-19:恶意软件 6/41