正在加载图片...
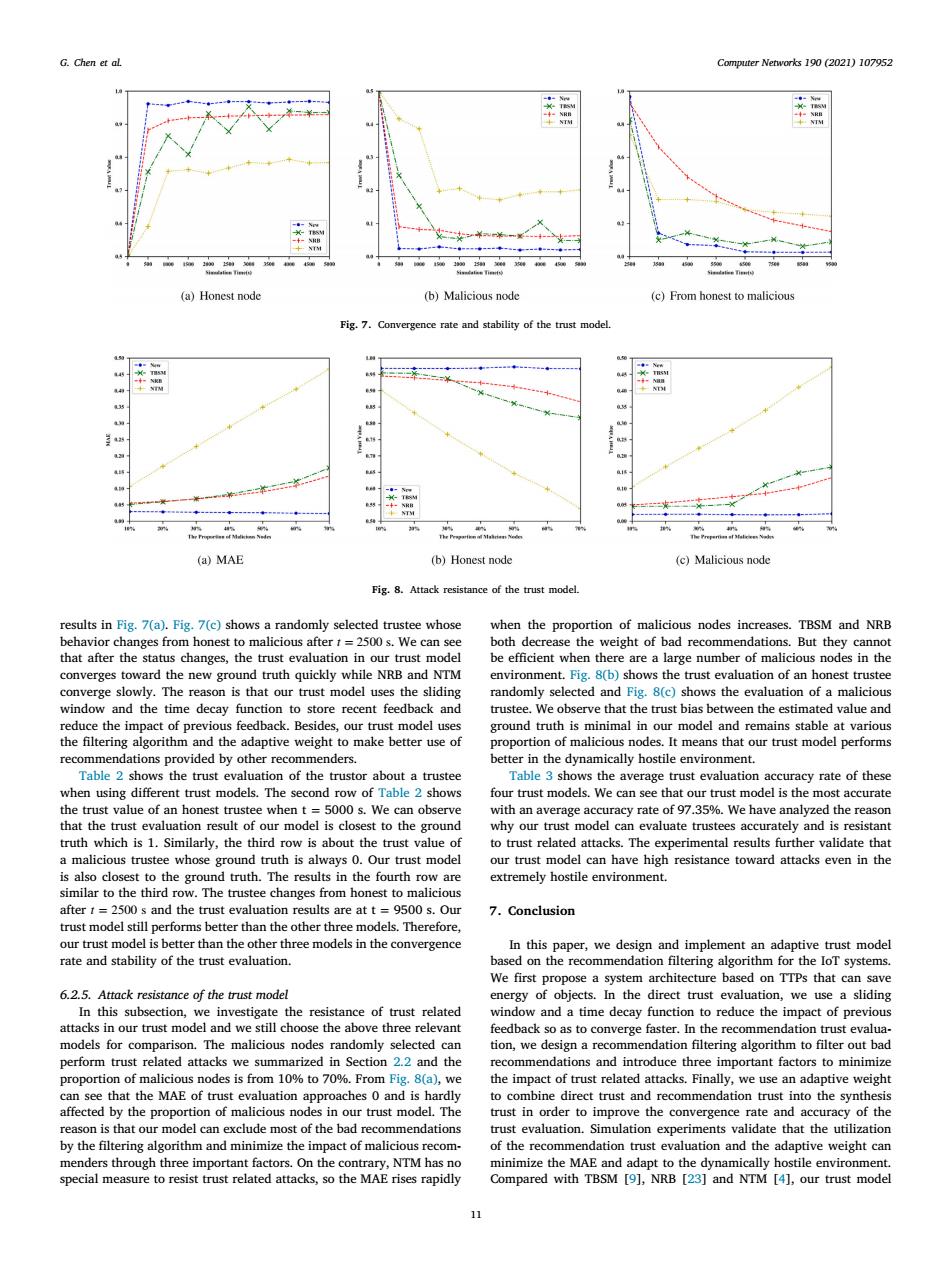
G.Chen et al. Computer Networks 190 (2021)107952 (a)Honest node (b)Malicious node (c)From honest to malicious Fig.7.Convergence rate and stability of the trust model. 4- 48- (a)MAE (b)Honest node (c)Malicious node Fig.8.Attack resistance of the trust model. results in Fig.7(a).Fig.7(c)shows a randomly selected trustee whose when the proportion of malicious nodes increases.TBSM and NRB behavior changes from honest to malicious aftert=2500s.We can see both decrease the weight of bad recommendations.But they cannot that after the status changes,the trust evaluation in our trust model be efficient when there are a large number of malicious nodes in the converges toward the new ground truth quickly while NRB and NTM environment.Fig.8(b)shows the trust evaluation of an honest trustee converge slowly.The reason is that our trust model uses the sliding randomly selected and Fig.8(c)shows the evaluation of a malicious window and the time decay function to store recent feedback and trustee.We observe that the trust bias between the estimated value and reduce the impact of previous feedback.Besides,our trust model uses ground truth is minimal in our model and remains stable at various the filtering algorithm and the adaptive weight to make better use of proportion of malicious nodes.It means that our trust model performs recommendations provided by other recommenders. better in the dynamically hostile environment. Table 2 shows the trust evaluation of the trustor about a trustee Table 3 shows the average trust evaluation accuracy rate of these when using different trust models.The second row of Table 2 shows four trust models.We can see that our trust model is the most accurate the trust value of an honest trustee when t =5000 s.We can observe with an average accuracy rate of 97.35%.We have analyzed the reason that the trust evaluation result of our model is closest to the ground why our trust model can evaluate trustees accurately and is resistant truth which is 1.Similarly,the third row is about the trust value of to trust related attacks.The experimental results further validate that a malicious trustee whose ground truth is always 0.Our trust model our trust model can have high resistance toward attacks even in the is also closest to the ground truth.The results in the fourth row are extremely hostile environment. similar to the third row.The trustee changes from honest to malicious after 1=2500 s and the trust evaluation results are at t =9500 s.Our 7.Conclusion trust model still performs better than the other three models.Therefore, our trust model is better than the other three models in the convergence In this paper,we design and implement an adaptive trust model rate and stability of the trust evaluation. based on the recommendation filtering algorithm for the IoT systems. We first propose a system architecture based on TTPs that can save 6.2.5.Attack resistance of the trust model energy of objects.In the direct trust evaluation,we use a sliding In this subsection,we investigate the resistance of trust related window and a time decay function to reduce the impact of previous attacks in our trust model and we still choose the above three relevant feedback so as to converge faster.In the recommendation trust evalua- models for comparison.The malicious nodes randomly selected can tion,we design a recommendation filtering algorithm to filter out bad perform trust related attacks we summarized in Section 2.2 and the recommendations and introduce three important factors to minimize proportion of malicious nodes is from 10%to 70%.From Fig.8(a),we the impact of trust related attacks.Finally,we use an adaptive weight can see that the MAE of trust evaluation approaches 0 and is hardly to combine direct trust and recommendation trust into the synthesis affected by the proportion of malicious nodes in our trust model.The trust in order to improve the convergence rate and accuracy of the reason is that our model can exclude most of the bad recommendations trust evaluation.Simulation experiments validate that the utilization by the filtering algorithm and minimize the impact of malicious recom- of the recommendation trust evaluation and the adaptive weight can menders through three important factors.On the contrary,NTM has no minimize the MAE and adapt to the dynamically hostile environment. special measure to resist trust related attacks,so the MAE rises rapidly Compared with TBSM [9],NRB [23]and NTM [4],our trust model 11Computer Networks 190 (2021) 107952 11 G. Chen et al. Fig. 7. Convergence rate and stability of the trust model. Fig. 8. Attack resistance of the trust model. results in Fig. 7(a). Fig. 7(c) shows a randomly selected trustee whose behavior changes from honest to malicious after 𝑡 = 2500 s. We can see that after the status changes, the trust evaluation in our trust model converges toward the new ground truth quickly while NRB and NTM converge slowly. The reason is that our trust model uses the sliding window and the time decay function to store recent feedback and reduce the impact of previous feedback. Besides, our trust model uses the filtering algorithm and the adaptive weight to make better use of recommendations provided by other recommenders. Table 2 shows the trust evaluation of the trustor about a trustee when using different trust models. The second row of Table 2 shows the trust value of an honest trustee when t = 5000 s. We can observe that the trust evaluation result of our model is closest to the ground truth which is 1. Similarly, the third row is about the trust value of a malicious trustee whose ground truth is always 0. Our trust model is also closest to the ground truth. The results in the fourth row are similar to the third row. The trustee changes from honest to malicious after 𝑡 = 2500 s and the trust evaluation results are at t = 9500 s. Our trust model still performs better than the other three models. Therefore, our trust model is better than the other three models in the convergence rate and stability of the trust evaluation. 6.2.5. Attack resistance of the trust model In this subsection, we investigate the resistance of trust related attacks in our trust model and we still choose the above three relevant models for comparison. The malicious nodes randomly selected can perform trust related attacks we summarized in Section 2.2 and the proportion of malicious nodes is from 10% to 70%. From Fig. 8(a), we can see that the MAE of trust evaluation approaches 0 and is hardly affected by the proportion of malicious nodes in our trust model. The reason is that our model can exclude most of the bad recommendations by the filtering algorithm and minimize the impact of malicious recommenders through three important factors. On the contrary, NTM has no special measure to resist trust related attacks, so the MAE rises rapidly when the proportion of malicious nodes increases. TBSM and NRB both decrease the weight of bad recommendations. But they cannot be efficient when there are a large number of malicious nodes in the environment. Fig. 8(b) shows the trust evaluation of an honest trustee randomly selected and Fig. 8(c) shows the evaluation of a malicious trustee. We observe that the trust bias between the estimated value and ground truth is minimal in our model and remains stable at various proportion of malicious nodes. It means that our trust model performs better in the dynamically hostile environment. Table 3 shows the average trust evaluation accuracy rate of these four trust models. We can see that our trust model is the most accurate with an average accuracy rate of 97.35%. We have analyzed the reason why our trust model can evaluate trustees accurately and is resistant to trust related attacks. The experimental results further validate that our trust model can have high resistance toward attacks even in the extremely hostile environment. 7. Conclusion In this paper, we design and implement an adaptive trust model based on the recommendation filtering algorithm for the IoT systems. We first propose a system architecture based on TTPs that can save energy of objects. In the direct trust evaluation, we use a sliding window and a time decay function to reduce the impact of previous feedback so as to converge faster. In the recommendation trust evaluation, we design a recommendation filtering algorithm to filter out bad recommendations and introduce three important factors to minimize the impact of trust related attacks. Finally, we use an adaptive weight to combine direct trust and recommendation trust into the synthesis trust in order to improve the convergence rate and accuracy of the trust evaluation. Simulation experiments validate that the utilization of the recommendation trust evaluation and the adaptive weight can minimize the MAE and adapt to the dynamically hostile environment. Compared with TBSM [9], NRB [23] and NTM [4], our trust model