正在加载图片...
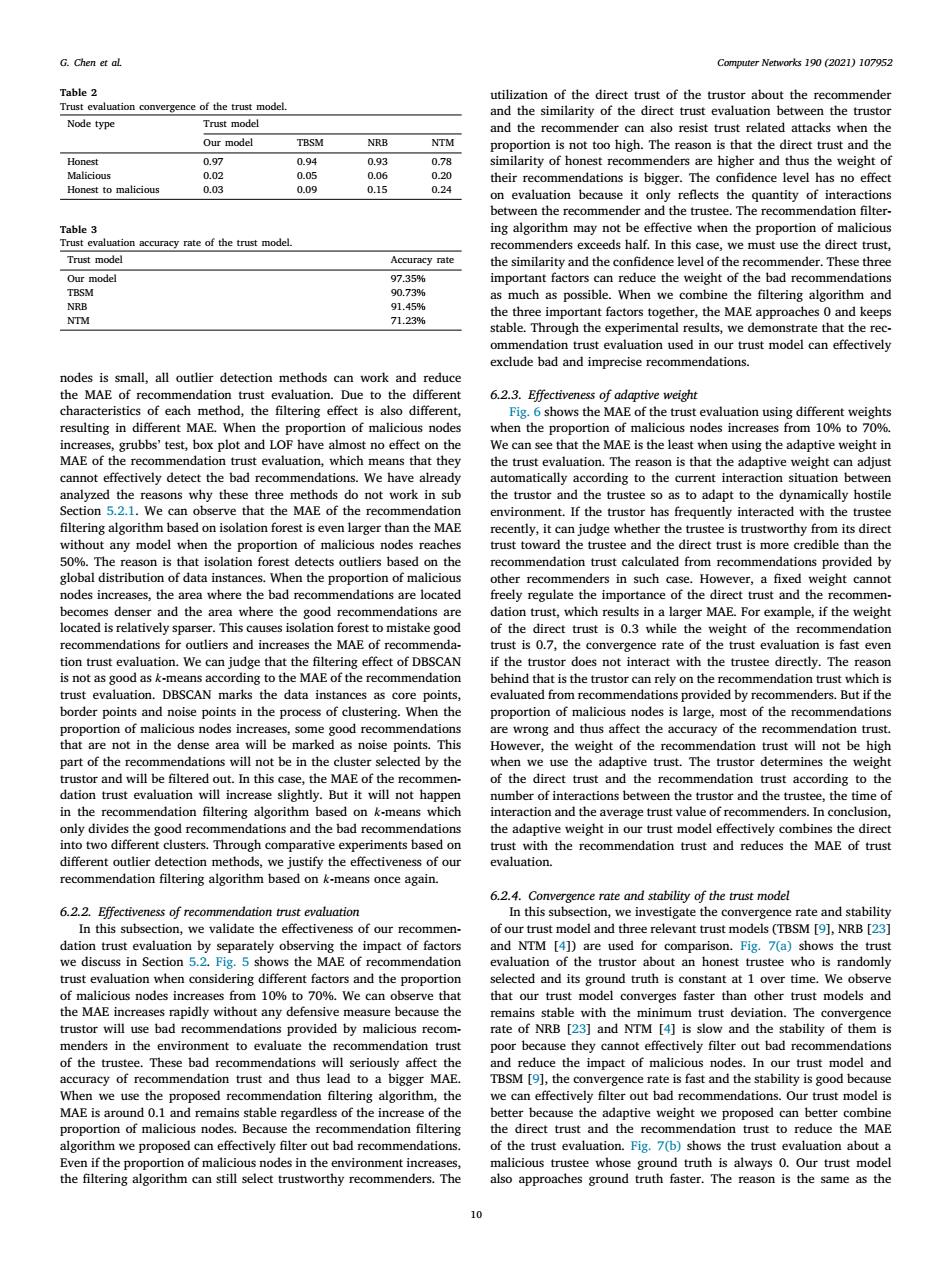
G.Chen et al. Computer Networks 190 (2021)107952 Table 2 utilization of the direct trust of the trustor about the recommender Trust evaluation convergence of the trust model. and the similarity of the direct trust evaluation between the trustor Node type Trust model and the recommender can also resist trust related attacks when the Our model TBSM NRB NTM proportion is not too high.The reason is that the direct trust and the Honest 0.97 0.94 0.93 0.78 similarity of honest recommenders are higher and thus the weight of Malicious 0.02 0.05 0.06 0.20 their recommendations is bigger.The confidence level has no effect Honest to malicious 0.03 0.09 0.15 0.24 on evaluation because it only reflects the quantity of interactions between the recommender and the trustee.The recommendation filter- Table 3 ing algorithm may not be effective when the proportion of malicious Trust evaluation accuracy rate of the trust model. recommenders exceeds half.In this case,we must use the direct trust, Trust model Accuracy rate the similarity and the confidence level of the recommender.These three Our model 97.35% important factors can reduce the weight of the bad recommendations TBSM 90.73% as much as possible.When we combine the filtering algorithm and NrB 91.45% NTM the three important factors together,the MAE approaches 0 and keeps 71.23% stable.Through the experimental results,we demonstrate that the rec- ommendation trust evaluation used in our trust model can effectively exclude bad and imprecise recommendations. nodes is small,all outlier detection methods can work and reduce the MAE of recommendation trust evaluation.Due to the different 6.2.3.Effectiveness of adaptive weight characteristics of each method,the filtering effect is also different, Fig.6 shows the MAE of the trust evaluation using different weights resulting in different MAE.When the proportion of malicious nodes when the proportion of malicious nodes increases from 10%to 70%. increases,grubbs'test,box plot and LOF have almost no effect on the We can see that the MAE is the least when using the adaptive weight in MAE of the recommendation trust evaluation,which means that they the trust evaluation.The reason is that the adaptive weight can adjust cannot effectively detect the bad recommendations.We have already automatically according to the current interaction situation between analyzed the reasons why these three methods do not work in sub the trustor and the trustee so as to adapt to the dynamically hostile Section 5.2.1.We can observe that the MAE of the recommendation environment.If the trustor has frequently interacted with the trustee filtering algorithm based on isolation forest is even larger than the MAE recently,it can judge whether the trustee is trustworthy from its direct without any model when the proportion of malicious nodes reaches trust toward the trustee and the direct trust is more credible than the 50%.The reason is that isolation forest detects outliers based on the recommendation trust calculated from recommendations provided by global distribution of data instances.When the proportion of malicious other recommenders in such case.However,a fixed weight cannot nodes increases,the area where the bad recommendations are located freely regulate the importance of the direct trust and the recommen- becomes denser and the area where the good recommendations are dation trust,which results in a larger MAE.For example,if the weight located is relatively sparser.This causes isolation forest to mistake good of the direct trust is 0.3 while the weight of the recommendation recommendations for outliers and increases the MAE of recommenda- trust is 0.7,the convergence rate of the trust evaluation is fast even tion trust evaluation.We can judge that the filtering effect of DBSCAN if the trustor does not interact with the trustee directly.The reason is not as good as k-means according to the MAE of the recommendation behind that is the trustor can rely on the recommendation trust which is trust evaluation.DBSCAN marks the data instances as core points, evaluated from recommendations provided by recommenders.But if the border points and noise points in the process of clustering.When the proportion of malicious nodes is large,most of the recommendations proportion of malicious nodes increases,some good recommendations are wrong and thus affect the accuracy of the recommendation trust. that are not in the dense area will be marked as noise points.This However,the weight of the recommendation trust will not be high part of the recommendations will not be in the cluster selected by the when we use the adaptive trust.The trustor determines the weight trustor and will be filtered out.In this case,the MAE of the recommen- of the direct trust and the recommendation trust according to the dation trust evaluation will increase slightly.But it will not happen number of interactions between the trustor and the trustee,the time of in the recommendation filtering algorithm based on k-means which interaction and the average trust value of recommenders.In conclusion, only divides the good recommendations and the bad recommendations the adaptive weight in our trust model effectively combines the direct into two different clusters.Through comparative experiments based on trust with the recommendation trust and reduces the MAE of trust different outlier detection methods,we justify the effectiveness of our evaluation. recommendation filtering algorithm based on k-means once again. 6.2.4.Convergence rate and stability of the trust model 6.2.2.Effectiveness of recommendation trust evaluation In this subsection,we investigate the convergence rate and stability In this subsection,we validate the effectiveness of our recommen- of our trust model and three relevant trust models(TBSM [9],NRB [23] dation trust evaluation by separately observing the impact of factors and NTM [4])are used for comparison.Fig.7(a)shows the trust we discuss in Section 5.2.Fig.5 shows the MAE of recommendation evaluation of the trustor about an honest trustee who is randomly trust evaluation when considering different factors and the proportion selected and its ground truth is constant at 1 over time.We observe of malicious nodes increases from 10%to 70%.We can observe that that our trust model converges faster than other trust models and the MAE increases rapidly without any defensive measure because the remains stable with the minimum trust deviation.The convergence trustor will use bad recommendations provided by malicious recom- rate of NRB [23]and NTM [4]is slow and the stability of them is menders in the environment to evaluate the recommendation trust poor because they cannot effectively filter out bad recommendations of the trustee.These bad recommendations will seriously affect the and reduce the impact of malicious nodes.In our trust model and accuracy of recommendation trust and thus lead to a bigger MAE. TBSM [9],the convergence rate is fast and the stability is good because When we use the proposed recommendation filtering algorithm,the we can effectively filter out bad recommendations.Our trust model is MAE is around 0.1 and remains stable regardless of the increase of the better because the adaptive weight we proposed can better combine proportion of malicious nodes.Because the recommendation filtering the direct trust and the recommendation trust to reduce the MAE algorithm we proposed can effectively filter out bad recommendations. of the trust evaluation.Fig.7(b)shows the trust evaluation about a Even if the proportion of malicious nodes in the environment increases, malicious trustee whose ground truth is always 0.Our trust model the filtering algorithm can still select trustworthy recommenders.The also approaches ground truth faster.The reason is the same as the 10Computer Networks 190 (2021) 107952 10 G. Chen et al. Table 2 Trust evaluation convergence of the trust model. Node type Trust model Our model TBSM NRB NTM Honest 0.97 0.94 0.93 0.78 Malicious 0.02 0.05 0.06 0.20 Honest to malicious 0.03 0.09 0.15 0.24 Table 3 Trust evaluation accuracy rate of the trust model. Trust model Accuracy rate Our model 97.35% TBSM 90.73% NRB 91.45% NTM 71.23% nodes is small, all outlier detection methods can work and reduce the MAE of recommendation trust evaluation. Due to the different characteristics of each method, the filtering effect is also different, resulting in different MAE. When the proportion of malicious nodes increases, grubbs’ test, box plot and LOF have almost no effect on the MAE of the recommendation trust evaluation, which means that they cannot effectively detect the bad recommendations. We have already analyzed the reasons why these three methods do not work in sub Section 5.2.1. We can observe that the MAE of the recommendation filtering algorithm based on isolation forest is even larger than the MAE without any model when the proportion of malicious nodes reaches 50%. The reason is that isolation forest detects outliers based on the global distribution of data instances. When the proportion of malicious nodes increases, the area where the bad recommendations are located becomes denser and the area where the good recommendations are located is relatively sparser. This causes isolation forest to mistake good recommendations for outliers and increases the MAE of recommendation trust evaluation. We can judge that the filtering effect of DBSCAN is not as good as 𝑘-means according to the MAE of the recommendation trust evaluation. DBSCAN marks the data instances as core points, border points and noise points in the process of clustering. When the proportion of malicious nodes increases, some good recommendations that are not in the dense area will be marked as noise points. This part of the recommendations will not be in the cluster selected by the trustor and will be filtered out. In this case, the MAE of the recommendation trust evaluation will increase slightly. But it will not happen in the recommendation filtering algorithm based on 𝑘-means which only divides the good recommendations and the bad recommendations into two different clusters. Through comparative experiments based on different outlier detection methods, we justify the effectiveness of our recommendation filtering algorithm based on 𝑘-means once again. 6.2.2. Effectiveness of recommendation trust evaluation In this subsection, we validate the effectiveness of our recommendation trust evaluation by separately observing the impact of factors we discuss in Section 5.2. Fig. 5 shows the MAE of recommendation trust evaluation when considering different factors and the proportion of malicious nodes increases from 10% to 70%. We can observe that the MAE increases rapidly without any defensive measure because the trustor will use bad recommendations provided by malicious recommenders in the environment to evaluate the recommendation trust of the trustee. These bad recommendations will seriously affect the accuracy of recommendation trust and thus lead to a bigger MAE. When we use the proposed recommendation filtering algorithm, the MAE is around 0.1 and remains stable regardless of the increase of the proportion of malicious nodes. Because the recommendation filtering algorithm we proposed can effectively filter out bad recommendations. Even if the proportion of malicious nodes in the environment increases, the filtering algorithm can still select trustworthy recommenders. The utilization of the direct trust of the trustor about the recommender and the similarity of the direct trust evaluation between the trustor and the recommender can also resist trust related attacks when the proportion is not too high. The reason is that the direct trust and the similarity of honest recommenders are higher and thus the weight of their recommendations is bigger. The confidence level has no effect on evaluation because it only reflects the quantity of interactions between the recommender and the trustee. The recommendation filtering algorithm may not be effective when the proportion of malicious recommenders exceeds half. In this case, we must use the direct trust, the similarity and the confidence level of the recommender. These three important factors can reduce the weight of the bad recommendations as much as possible. When we combine the filtering algorithm and the three important factors together, the MAE approaches 0 and keeps stable. Through the experimental results, we demonstrate that the recommendation trust evaluation used in our trust model can effectively exclude bad and imprecise recommendations. 6.2.3. Effectiveness of adaptive weight Fig. 6 shows the MAE of the trust evaluation using different weights when the proportion of malicious nodes increases from 10% to 70%. We can see that the MAE is the least when using the adaptive weight in the trust evaluation. The reason is that the adaptive weight can adjust automatically according to the current interaction situation between the trustor and the trustee so as to adapt to the dynamically hostile environment. If the trustor has frequently interacted with the trustee recently, it can judge whether the trustee is trustworthy from its direct trust toward the trustee and the direct trust is more credible than the recommendation trust calculated from recommendations provided by other recommenders in such case. However, a fixed weight cannot freely regulate the importance of the direct trust and the recommendation trust, which results in a larger MAE. For example, if the weight of the direct trust is 0.3 while the weight of the recommendation trust is 0.7, the convergence rate of the trust evaluation is fast even if the trustor does not interact with the trustee directly. The reason behind that is the trustor can rely on the recommendation trust which is evaluated from recommendations provided by recommenders. But if the proportion of malicious nodes is large, most of the recommendations are wrong and thus affect the accuracy of the recommendation trust. However, the weight of the recommendation trust will not be high when we use the adaptive trust. The trustor determines the weight of the direct trust and the recommendation trust according to the number of interactions between the trustor and the trustee, the time of interaction and the average trust value of recommenders. In conclusion, the adaptive weight in our trust model effectively combines the direct trust with the recommendation trust and reduces the MAE of trust evaluation. 6.2.4. Convergence rate and stability of the trust model In this subsection, we investigate the convergence rate and stability of our trust model and three relevant trust models (TBSM [9], NRB [23] and NTM [4]) are used for comparison. Fig. 7(a) shows the trust evaluation of the trustor about an honest trustee who is randomly selected and its ground truth is constant at 1 over time. We observe that our trust model converges faster than other trust models and remains stable with the minimum trust deviation. The convergence rate of NRB [23] and NTM [4] is slow and the stability of them is poor because they cannot effectively filter out bad recommendations and reduce the impact of malicious nodes. In our trust model and TBSM [9], the convergence rate is fast and the stability is good because we can effectively filter out bad recommendations. Our trust model is better because the adaptive weight we proposed can better combine the direct trust and the recommendation trust to reduce the MAE of the trust evaluation. Fig. 7(b) shows the trust evaluation about a malicious trustee whose ground truth is always 0. Our trust model also approaches ground truth faster. The reason is the same as the