正在加载图片...
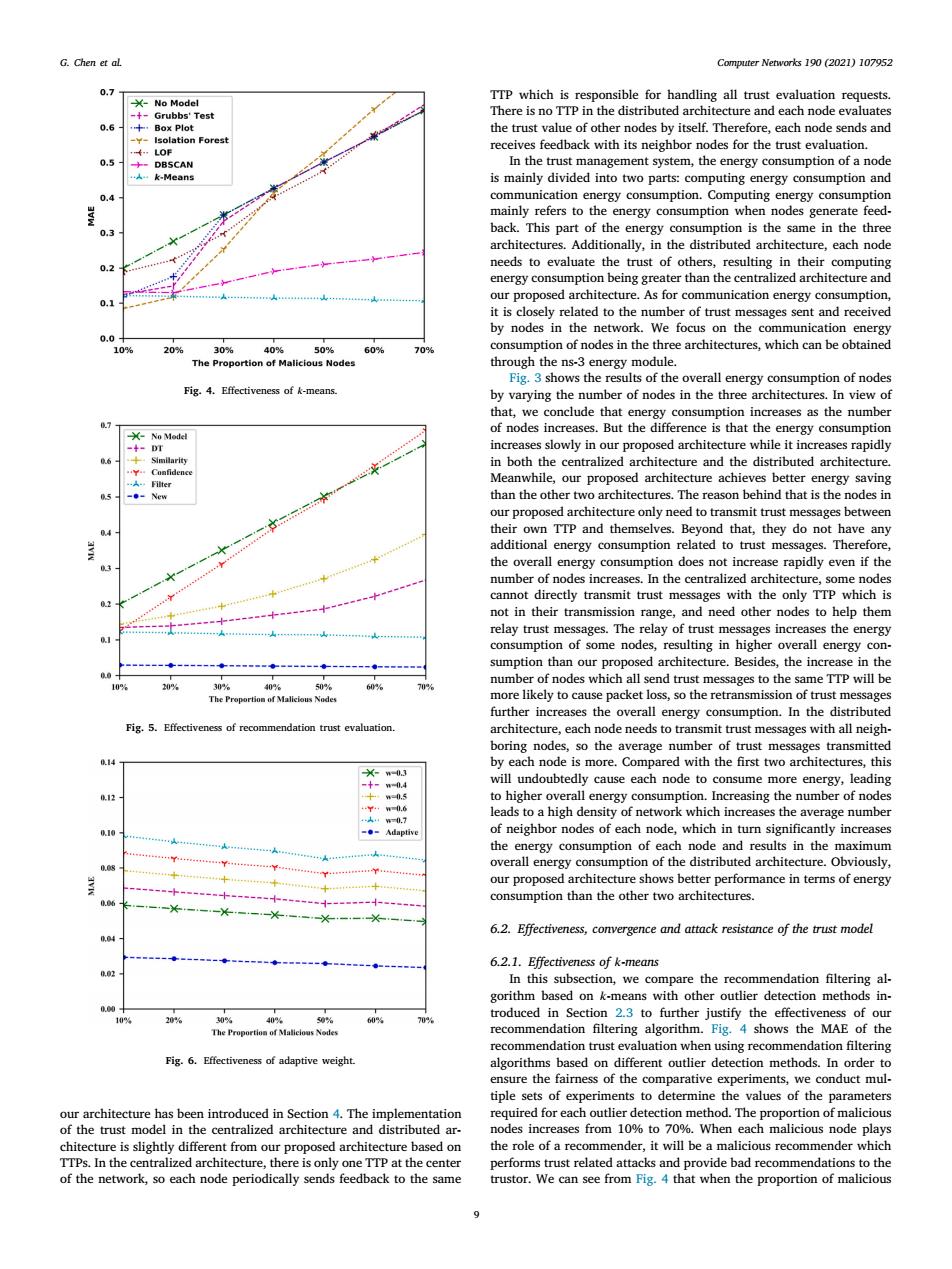
G.Chen et al. Computer Networks 190(2021)107952 0.7 TTP which is responsible for handling all trust evaluation requests. -No Model -t-Grubbs'Test There is no TTP in the distributed architecture and each node evaluates 0.6 十Box Plot the trust value of other nodes by itself.Therefore,each node sends and -Y-Isolation Forest LOF receives feedback with its neighbor nodes for the trust evaluation. 0.5 -DBSCAN In the trust management system,the energy consumption of a node A.k-Means is mainly divided into two parts:computing energy consumption and 0.4 communication energy consumption.Computing energy consumption mainly refers to the energy consumption when nodes generate feed- 0,3 back.This part of the energy consumption is the same in the three architectures.Additionally,in the distributed architecture,each node 0.2 needs to evaluate the trust of others,resulting in their computing energy consumption being greater than the centralized architecture and our proposed architecture.As for communication energy consumption, 0.1 it is closely related to the number of trust messages sent and received by nodes in the network.We focus on the communication energy 0.0 10% 20% 30% 40% 509% 60% consumption of nodes in the three architectures,which can be obtained The Proportion of Malicious Nodes through the ns-3 energy module. Fig.3 shows the results of the overall energy consumption of nodes Fig.4.Effectiveness of k-means. by varying the number of nodes in the three architectures.In view of that,we conclude that energy consumption increases as the number (-No Model of nodes increases.But the difference is that the energy consumption increases slowly in our proposed architecture while it increases rapidly in both the centralized architecture and the distributed architecture. Filter Meanwhile,our proposed architecture achieves better energy saving 05 than the other two architectures.The reason behind that is the nodes in our proposed architecture only need to transmit trust messages between 4 their own TTp and themselves.Beyond that,they do not have any additional energy consumption related to trust messages.Therefore, the overall energy consumption does not increase rapidly even if the number of nodes increases.In the centralized architecture,some nodes cannot directly transmit trust messages with the only TTP which is 03 not in their transmission range,and need other nodes to help them relay trust messages.The relay of trust messages increases the energy consumption of some nodes,resulting in higher overall energy con- sumption than our proposed architecture.Besides,the increase in the number of nodes which all send trust messages to the same TTP will be 109 30% 409% 50% The Proportion of Malicious Nodes more likely to cause packet loss,so the retransmission of trust messages further increases the overall energy consumption.In the distributed Fig.5.Effectiven dation rust evaluation architecture,each node needs to transmit trust messages with all neigh- boring nodes,so the average number of trust messages transmitted h14 by each node is more.Compared with the first two architectures,this Xn0.3 will undoubtedly cause each node to consume more energy,leading 0.12 to higher overall energy consumption.Increasing the number of nodes leads to a high density of network which increases the average number 人4w0.7 --Adaptive of neighbor nodes of each node,which in turn significantly increases the energy consumption of each node and results in the maximum 44 overall energy consumption of the distributed architecture.Obviously, + our proposed architecture shows better performance in terms of energy consumption than the other two architectures 6.2.Effectiveness,convergence and attack resistance of the trust model 6.2.1.Effectiveness of k-means h.01 In this subsection,we compare the recommendation filtering al. gorithm based on k-means with other outlier detection methods in- 30% 40% troduced in Section 2.3 to further justify the effectiveness of our 0% 60% The Proportion of Malicious Nodes recommendation filtering algorithm.Fig.4 shows the MAE of the recommendation trust evaluation when using recommendation filtering Fig.6.Effectiveness of adaptive weight algorithms based on different outlier detection methods.In order to ensure the fairness of the comparative experiments,we conduct mul- tiple sets of experiments to determine the values of the parameters our architecture has been introduced in Section 4.The implementation required for each outlier detection method.The proportion of malicious of the trust model in the centralized architecture and distributed ar- nodes increases from 10%to 70%.When each malicious node plays chitecture is slightly different from our proposed architecture based on the role of a recommender,it will be a malicious recommender which TTPs.In the centralized architecture,there is only one TTP at the center performs trust related attacks and provide bad recommendations to the of the network,so each node periodically sends feedback to the same trustor.We can see from Fig.4 that when the proportion of malicious 9Computer Networks 190 (2021) 107952 9 G. Chen et al. Fig. 4. Effectiveness of 𝑘-means. Fig. 5. Effectiveness of recommendation trust evaluation. Fig. 6. Effectiveness of adaptive weight. our architecture has been introduced in Section 4. The implementation of the trust model in the centralized architecture and distributed architecture is slightly different from our proposed architecture based on TTPs. In the centralized architecture, there is only one TTP at the center of the network, so each node periodically sends feedback to the same TTP which is responsible for handling all trust evaluation requests. There is no TTP in the distributed architecture and each node evaluates the trust value of other nodes by itself. Therefore, each node sends and receives feedback with its neighbor nodes for the trust evaluation. In the trust management system, the energy consumption of a node is mainly divided into two parts: computing energy consumption and communication energy consumption. Computing energy consumption mainly refers to the energy consumption when nodes generate feedback. This part of the energy consumption is the same in the three architectures. Additionally, in the distributed architecture, each node needs to evaluate the trust of others, resulting in their computing energy consumption being greater than the centralized architecture and our proposed architecture. As for communication energy consumption, it is closely related to the number of trust messages sent and received by nodes in the network. We focus on the communication energy consumption of nodes in the three architectures, which can be obtained through the ns-3 energy module. Fig. 3 shows the results of the overall energy consumption of nodes by varying the number of nodes in the three architectures. In view of that, we conclude that energy consumption increases as the number of nodes increases. But the difference is that the energy consumption increases slowly in our proposed architecture while it increases rapidly in both the centralized architecture and the distributed architecture. Meanwhile, our proposed architecture achieves better energy saving than the other two architectures. The reason behind that is the nodes in our proposed architecture only need to transmit trust messages between their own TTP and themselves. Beyond that, they do not have any additional energy consumption related to trust messages. Therefore, the overall energy consumption does not increase rapidly even if the number of nodes increases. In the centralized architecture, some nodes cannot directly transmit trust messages with the only TTP which is not in their transmission range, and need other nodes to help them relay trust messages. The relay of trust messages increases the energy consumption of some nodes, resulting in higher overall energy consumption than our proposed architecture. Besides, the increase in the number of nodes which all send trust messages to the same TTP will be more likely to cause packet loss, so the retransmission of trust messages further increases the overall energy consumption. In the distributed architecture, each node needs to transmit trust messages with all neighboring nodes, so the average number of trust messages transmitted by each node is more. Compared with the first two architectures, this will undoubtedly cause each node to consume more energy, leading to higher overall energy consumption. Increasing the number of nodes leads to a high density of network which increases the average number of neighbor nodes of each node, which in turn significantly increases the energy consumption of each node and results in the maximum overall energy consumption of the distributed architecture. Obviously, our proposed architecture shows better performance in terms of energy consumption than the other two architectures. 6.2. Effectiveness, convergence and attack resistance of the trust model 6.2.1. Effectiveness of 𝑘-means In this subsection, we compare the recommendation filtering algorithm based on 𝑘-means with other outlier detection methods introduced in Section 2.3 to further justify the effectiveness of our recommendation filtering algorithm. Fig. 4 shows the MAE of the recommendation trust evaluation when using recommendation filtering algorithms based on different outlier detection methods. In order to ensure the fairness of the comparative experiments, we conduct multiple sets of experiments to determine the values of the parameters required for each outlier detection method. The proportion of malicious nodes increases from 10% to 70%. When each malicious node plays the role of a recommender, it will be a malicious recommender which performs trust related attacks and provide bad recommendations to the trustor. We can see from Fig. 4 that when the proportion of malicious