正在加载图片...
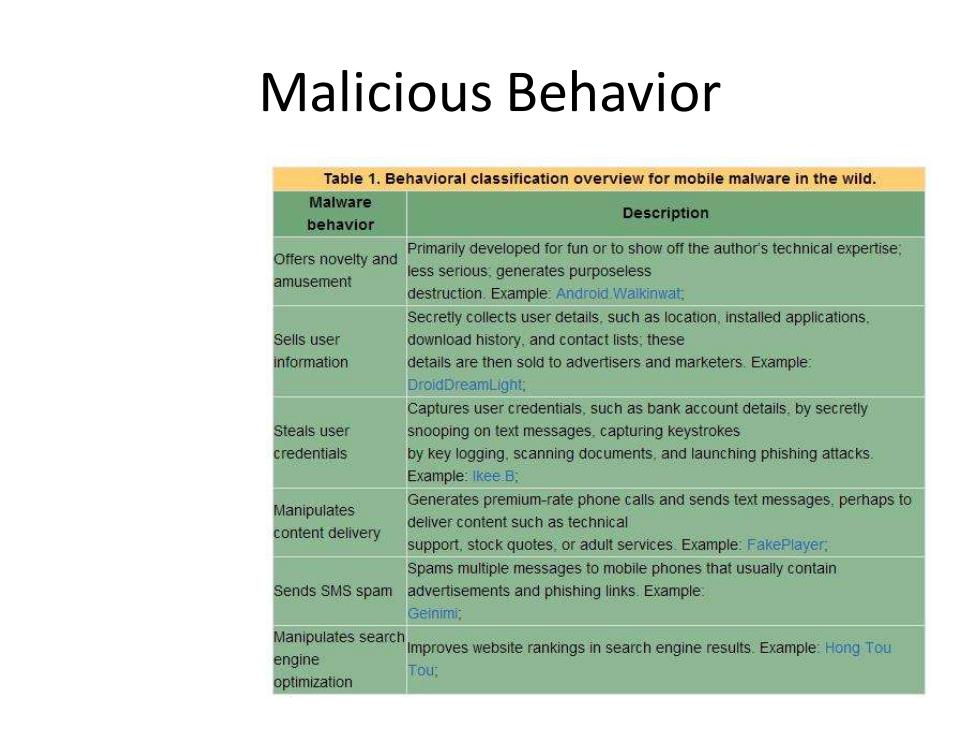
Malicious Behavior Table 1.Behavioral classification overview for mobile malware in the wild. Malware Description behavior Primarily developed for fun or to show off the author's technical expertise, Offers novelty and less serious,generates purposeless amusement destruction.Example:Android Walkinwat Secretly collects user details.such as location,installed applications. Sells user download history.and contact lists:these information details are then sold to advertisers and marketers.Example: DroidDreamLight: Captures user credentials,such as bank account details.by secretly Steals user snooping on text messages.capturing keystrokes credentials by key logging,scanning documents.and launching phishing attacks Example:Ikee B: Manipulates Generates premium-rate phone calls and sends text messages.perhaps to deliver content such as technical content delivery support,stock quotes.or adult services.Example:FakePlayer, Spams multiple messages to mobile phones that usually contain Sends SMS spam advertisements and phishing links.Example Geinimi: Manipulates search Improves website rankings in search engine results.Example:Hong Tou engine optimization Malicious Behavior