
Android application security
Android application security

As the most popular mobile OS,android platform is a growing target for security attacks from many sources
• As the most popular mobile OS, android platform is a growing target for security attacks from many sources

。Untrusted developer -the prevalence of installed applications coming from unknown developers 。Open app markets raising concerns about how risky third-party applications are and how they may misuse or improperly handle users'privacy-sensitive data
• Untrusted developer – the prevalence of installed applications coming from unknown developers • Open app markets – raising concerns about how risky third-party applications are and how they may misuse or improperly handle users’ privacy-sensitive data

。Mobile users know the security risk when a downloaded app is installed on their phones monitor the run-time operations during the apps are running ·Trusted Developer make secure enough apps,such as internet banking apps no vulnerability could be exploited by attackers to bring serious damage
• Mobile users – know the security risk when a downloaded app is installed on their phones – monitor the run-time operations during the apps are running • Trusted Developer – make secure enough apps, such as internet banking apps – no vulnerability could be exploited by attackers to bring serious damage

security validation for android apps ensure that the new app conforms to the security requirements a platform is built for app markets and developers to perform security verification and validation of these massive apps automatically evaluate the security of apps
security validation for android apps • ensure that the new app conforms to the security requirements • a platform is built for app markets and developers to perform security verification and validation of these massive apps – automatically evaluate the security of apps

Effective tracking mechanism for run-time properties:control-flow and data-flow Patterns of security violation,pattern expression and matching Vulnerability Scanning Applicable for three categories of apps:web, native and hybrid Practical consideration,such as performance, accuracy,.… So-called best practices
• Effective tracking mechanism for run-time properties: control-flow and data-flow • Patterns of security violation, pattern expression and matching • Vulnerability Scanning • Applicable for three categories of apps: web, native and hybrid • Practical consideration, such as performance, accuracy, … • So-called best practices

Malware,softwares that exhibits malicious behavior, -virus,worm,Trojan horse
• Malware, softwaresthat exhibits malicious behavior, – virus, worm, Trojan horse

We need to develop methods to automate the malware analysis process 。Signature-based Specific patterns in the bytecode and API calls Machine learning-based Features from an application's behavior Machine learning algorithms
• We need to develop methods to automate the malware analysis process • Signature-based – Specific patterns in the bytecode and API calls • Machine learning-based – Features from an application’s behavior – Machine learning algorithms
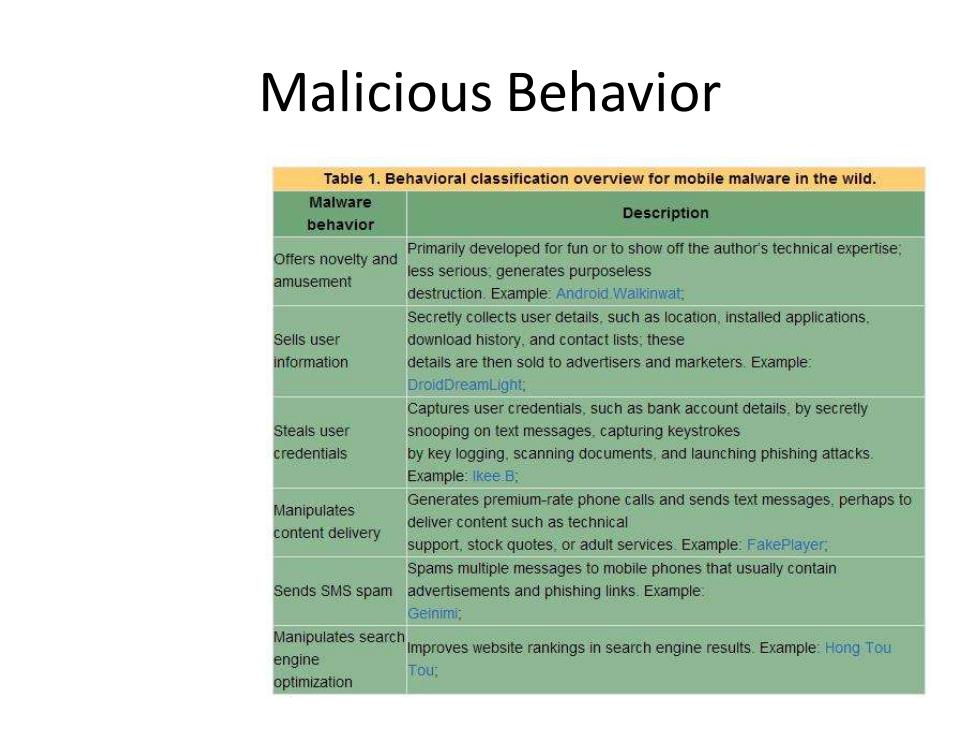
Malicious Behavior Table 1.Behavioral classification overview for mobile malware in the wild. Malware Description behavior Primarily developed for fun or to show off the author's technical expertise, Offers novelty and less serious,generates purposeless amusement destruction.Example:Android Walkinwat Secretly collects user details.such as location,installed applications. Sells user download history.and contact lists:these information details are then sold to advertisers and marketers.Example: DroidDreamLight: Captures user credentials,such as bank account details.by secretly Steals user snooping on text messages.capturing keystrokes credentials by key logging,scanning documents.and launching phishing attacks Example:Ikee B: Manipulates Generates premium-rate phone calls and sends text messages.perhaps to deliver content such as technical content delivery support,stock quotes.or adult services.Example:FakePlayer, Spams multiple messages to mobile phones that usually contain Sends SMS spam advertisements and phishing links.Example Geinimi: Manipulates search Improves website rankings in search engine results.Example:Hong Tou engine optimization
Malicious Behavior

Static analysis finding malicious characteristics or bad code segments in an application without executing them Preliminary analysis,obvious security threats
Static analysis • finding malicious characteristics or bad code segments in an application without executing them • Preliminary analysis, obvious security threats