
Operating-System Structures
Operating-System Structures

Outline Operating System Services User Operating System Interface ·System Calls ·Types of System Calls ·System Programs Operating System Design and Implementation Operating System Structure Operating System Debugging Operating System Generation ·System Boot
Outline • Operating System Services • User Operating System Interface • System Calls • Types of System Calls • System Programs • Operating System Design and Implementation • Operating System Structure • Operating System Debugging • Operating System Generation • System Boot
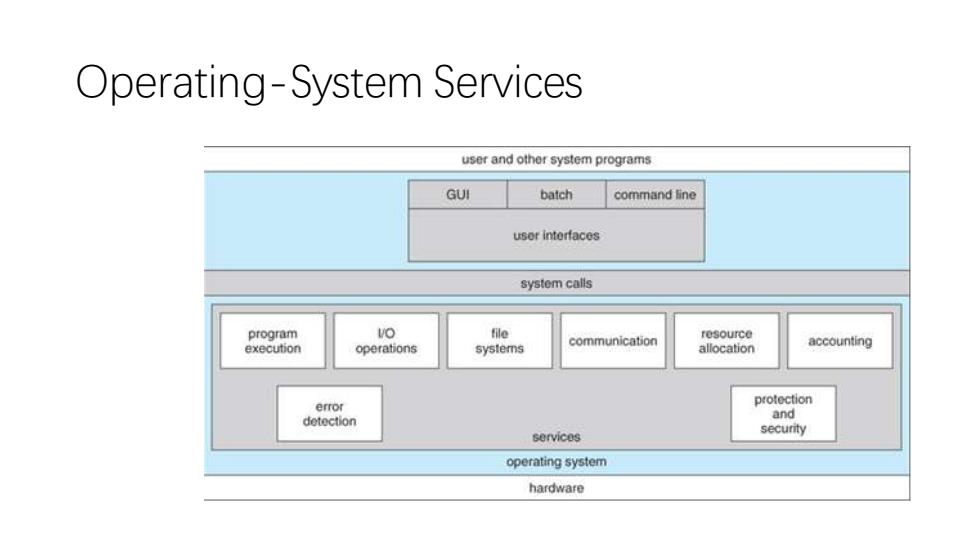
Operating-System Services user and other system programs GUI batch command line usor interfaces system calls program VO file resource communication execution operations systems allocation accounting error protection detection and secunty services operating system hardware
Operating-System Services

User Interfaces -Means by which users can issue commands to the system. a command-line interface e.g.sh,csh,ksh,tcsh,etc.) a GUl interface e.g.Windows,X-Windows,KDE,Gnome,etc. or a batch command systems.The latter are generally older systems using punch cards of job-control language,JCL,but may still be used today for specialty systems designed for a single purpose
• User Interfaces - Means by which users can issue commands to the system. • a command-line interface ( e.g. sh, csh, ksh, tcsh, etc. ), • a GUI interface ( e.g. Windows, X-Windows, KDE, Gnome, etc. ) • or a batch command systems. The latter are generally older systems using punch cards of job-control language, JCL, but may still be used today for specialty systems designed for a single purpose

Program Execution-The OS must be able to load a program into RAM,run the program,and terminate the program,either normally or abnormally.(process lifecycle) 1/O Operations -The OS is responsible for transferring data to and from 1/O devices,including keyboards,terminals,printers,and storage devices. File-System Manipulation -In addition to raw data storage,the OS is also responsible for maintaining directory and subdirectory structures,mapping file names to specific blocks of data storage, and providing tools for navigating and utilizing the file system
• Program Execution - The OS must be able to load a program into RAM, run the program, and terminate the program, either normally or abnormally.(process lifecycle) • I/O Operations - The OS is responsible for transferring data to and from I/O devices, including keyboards, terminals, printers, and storage devices. • File-System Manipulation - In addition to raw data storage, the OS is also responsible for maintaining directory and subdirectory structures, mapping file names to specific blocks of data storage, and providing tools for navigating and utilizing the file system

Communications -Inter-process communications,IPC,either between processes running on the same processor,or between processes running on separate processors or separate machines. May be implemented as either shared memory or message passing,or some systems may offer both. Error Detection -Both hardware and software errors must be detected and handled appropriately.Some systems may include complex error avoidance or recovery systems,including backups, RAID drives,and other redundant systems.Debugging and diagnostic tools aid users and administrators in tracing down the cause of problems
• Communications - Inter-process communications, IPC, either between processes running on the same processor, or between processes running on separate processors or separate machines. May be implemented as either shared memory or message passing, ( or some systems may offer both. ) • Error Detection - Both hardware and software errors must be detected and handled appropriately. Some systems may include complex error avoidance or recovery systems, including backups, RAID drives, and other redundant systems. Debugging and diagnostic tools aid users and administrators in tracing down the cause of problems

Resource Allocation -E.g.CPU cycles,main memory,storage space,and peripheral devices. Accounting -Keeping track of system activity and resource usage, either for billing purposes or for statistical record keeping that can be used to optimize future performance
• Resource Allocation - E.g. CPU cycles, main memory, storage space, and peripheral devices. • Accounting - Keeping track of system activity and resource usage, either for billing purposes or for statistical record keeping that can be used to optimize future performance

Protection and Security-Preventing harm to the system and to resources,either through wayward internal processes or malicious outsiders. Authentication,ownership,and restricted access are obvious parts of this system. Highly secure systems may log all process activity down to excruciating detail,and security regulation dictate the storage of those records on permanent non-erasable medium for extended times in secure off-site facilities
• Protection and Security - Preventing harm to the system and to resources, either through wayward internal processes or malicious outsiders. • Authentication, ownership, and restricted access are obvious parts of this system. • Highly secure systems may log all process activity down to excruciating detail, and security regulation dictate the storage of those records on permanent non-erasable medium for extended times in secure ( off-site ) facilities

User Operating-System Interface ·Command Interpreter Graphical User Interface,GUl 。Choice of interface
User Operating-System Interface • Command Interpreter • Graphical User Interface, GUI • Choice of interface

Command Interpreter Gets and processes the next user request,and launches the requested programs. In some systems the CI may be incorporated directly into the kernel. More commonly the Cl is a separate program that launches once the user logs in or otherwise accesses the system
- Command Interpreter • Gets and processes the next user request, and launches the requested programs. • In some systems the CI may be incorporated directly into the kernel. • More commonly the CI is a separate program that launches once the user logs in or otherwise accesses the system