正在加载图片...
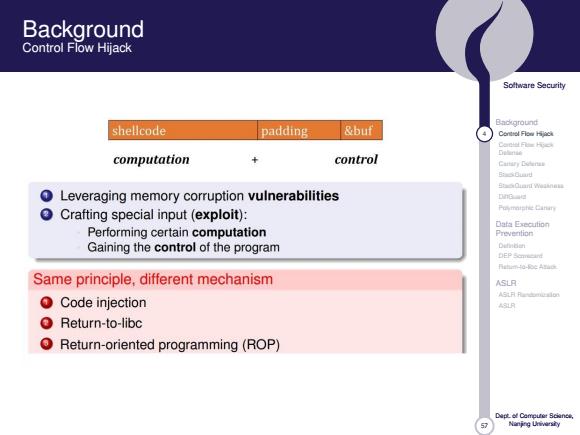
Background Control Flow Hijack Soltware Security Background shellcode padding &buf Contol Flow Hijack Carnial Fis Hyck control Delinie computation Cattary Codenas Bs0au时 SOianT weaneu 0 Leveraging memory corruption vulnerabilities DnG Crafting special input(exploit): Puymnishie Cinin Data Execution Performing certain computation Prevention Gaining the control of the program Dh6的 Same principle,different mechanism ASLR Code injection ASLR Return-to-libc OReturn-oriented programming(ROP) Nanjng Urivarsiy57 Software Security Background 4 Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack