
2017Fall:Software Security Lecture 5:Practical Control Flow Hijack Defense: StackGuard,DEP,and ASLR Bing Mao maobingon ju.edu.cn Department of Computer Science
2017Fall:Software Security Lecture 5 : Practical Control Flow Hijack Defense: StackGuard, DEP, and ASLR Bing Mao ♠❛♦❜✐♥❣❅♥❥✉✳❡❞✉✳❝♥ Department of Computer Science

Outline Soltware Security Background Control Flow Hijack Background Carerf Fies Hpck Control Flow Hijack Defense CaciaFas Hick Delinie Canary Defense Cattary Codenas B:s0a时 StackGuard 9S0ia过ana StackGuard Weakness DnG 4na中eCanin DiffGuard Data Execution Polymorphic Canary Prevention Dutidan Data Execution Prevention Fghim-ta-soc Arad Definition ASLR DEP Scorecard A9月 Return-to-libc Attack ASLR ASLR Randomization ASLR Nanjng Uivarsity
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Outline Background Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR
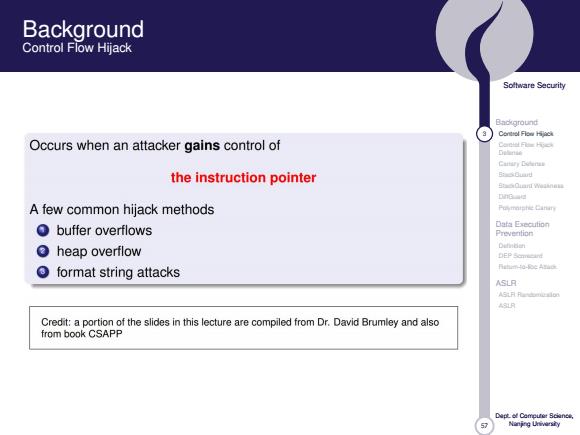
Background Control Flow Hijack Soltware Security Background Contol Flow Hijack Occurs when an attacker gains control of Carnial Fis Hyck Delinie Cattary Codenas the instruction pointer s0au时 SOianT weianat DnG A few common hijack methods Puymnishie Cinin buffer overflows Data Execution Prevention heap overflow Dutidan format string attacks ASLR ASLR Credit:a portion of the slides in this lecture are compiled from Dr.David Brumley and also from book CSAPP Nanjng Uivarsty
57 Software Security Background 3 Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack
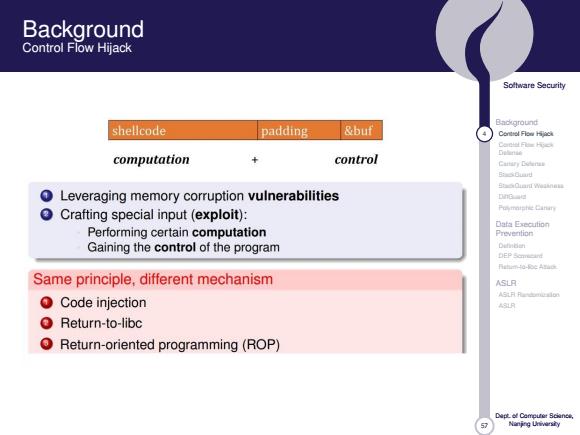
Background Control Flow Hijack Soltware Security Background shellcode padding &buf Contol Flow Hijack Carnial Fis Hyck control Delinie computation Cattary Codenas Bs0au时 SOianT weaneu 0 Leveraging memory corruption vulnerabilities DnG Crafting special input(exploit): Puymnishie Cinin Data Execution Performing certain computation Prevention Gaining the control of the program Dh6的 Same principle,different mechanism ASLR Code injection ASLR Return-to-libc OReturn-oriented programming(ROP) Nanjng Urivarsiy
57 Software Security Background 4 Control Flow Hijack Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack

Background Control Flow Hijack Defense Soltware Security Background 5】 Cordol月ea Detinse Vulnerabilities(bugs)are the root cause of hijacks Cattary Codenas Bs0au时 Identify vulnerabilities with analysis tools(before attackers) SOianT weianei DnG Prove program correctness Puymnishie Cinin Data Execution Prevention Mitigation Techniques: Dutidan Canaries-StackGuard Data Execution Prevention(DEP)/No eXecute(NX) ASLR Address Space Layout Randomization(ASLR) ASLR Nanjng Uivarsty
57 Software Security Background Control Flow Hijack 5 Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack Defense
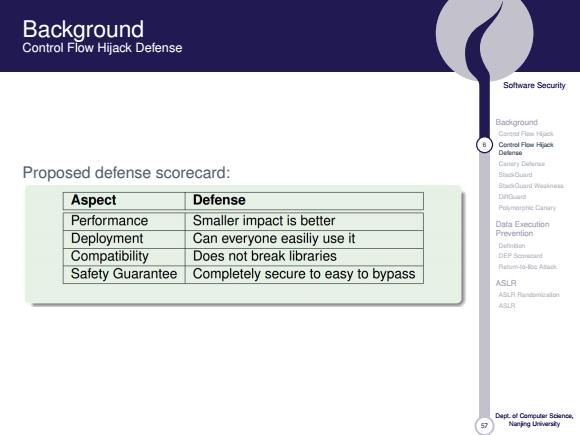
Background Control Flow Hijack Defense Soltware Security Background Cordol月e Definse Cattary Codenas Proposed defense scorecard: BS0au时 SOianT weaneu Aspect Defense DnG Puymnishie Cinin Performance Smaller impact is better Data Execution Deployment Can everyone easiliy use it Prevention Dutidan Compatibility Does not break libraries Fghim-ta-soc Arad Safety Guarantee Completely secure to easy to bypass ASLR ASLR Nanjng Urivarsiy
57 Software Security Background Control Flow Hijack 6 Control Flow Hijack Defense Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Background Control Flow Hijack Defense Proposed defense scorecard:

Canary-Based Protection Canary Defense Soltware Security Background Wikipedia:"the historic practice of using canaries in coal mines,since they would be affected by toxic gases earlier than )Carary Delarse the miners,thus providing a biological warning system." DnG Pulmnishie Cinin Data Execution Prevention Dutindan Canary Stack Cookies ASLR A9月
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense 7 Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection Canary Defense
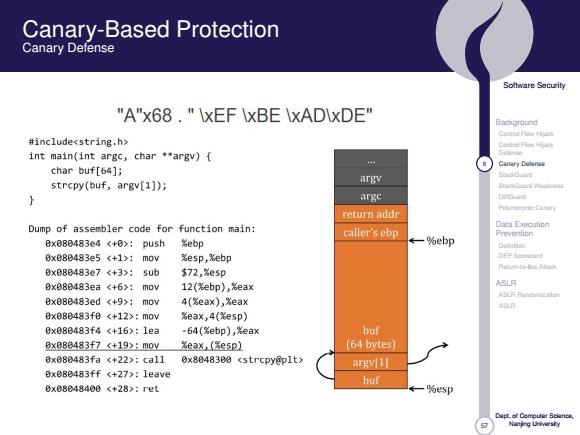
Canary-Based Protection Canary Defense Soltware Security "A"x68."IxEF IxBE \xADIxDE" Background Carerf Fies Hpck #include int main(int argc,char *argv){ mMeo Cantary Delaree char buf[64]; s0a时 strcpy(buf,argv[1]); argv SOianT weiana argc DnG return addr Puymnishie Cinin Dump of assembler code for function main: Data Execution caller's ebp 0x080483e4:push Xebp ←一%ebp Prevention Dutidan 8xe80483e5:m0v %esp,%ebp 0x080483e7:sub $72,Xesp Bx888483ea:mov 12(%ebp),%eax ASLR ASL月月uo Bx880483ed(+9>:mov 4(影eax),%eax ASLR 8xe80483f8:mov eax,4(%esp) 8x080483f4:1ea -64(%ebp),Xeax buf 0x888483f7:m0w%eaX,(Xe5p】 (64 bytes) 0x08483fac+22>:ca110x80483e0(strcpy@p1t> argv[1l 8x080483ff《+27,:1eave buf 8x08048408《+28>:ret ←一%esp Nanjng Uivarsiy
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense 8 Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection Canary Defense
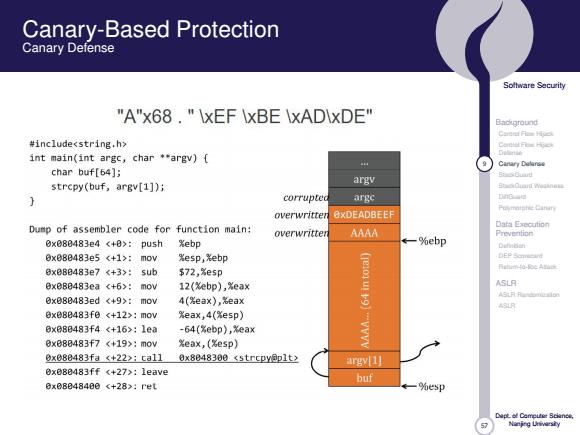
Canary-Based Protection Canary Defense Soltware Security "A"x68."IxEF IxBE \xADIxDE" Background Carerf Fies Hpck #includesstring.h> mMeo int main(int argc,char argv){ 4 Cantary Delaree char buf[64]; strcpy(buf,argv[1]); argv corrupte argc DnG overwritten OxDEADBEEF Puymnishie Cinin Dump of assembler code for function main: Data Execution overwritter AAAA 0x080483e4 :push %ebp -%ebp Prevention Dutidan 0xe88483e5:mov %esp,Xebp 9xe88483e7:sub $72,%e5p 0x0B0483ea :mov 12(%ebp),%eax ASLR AS月月o 0x08B483ed:mov 4(%eax),名eax ASLR 0x08B483f0:mov eax,4(%esp) 0xeBB483f4:1ea -64(Xebp),%eax 0xe88483f7:mov xeax,(%esp)】 0x088483fa:ret %esp Naning Ueivarsiy
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense 9 Canary Defense StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection Canary Defense
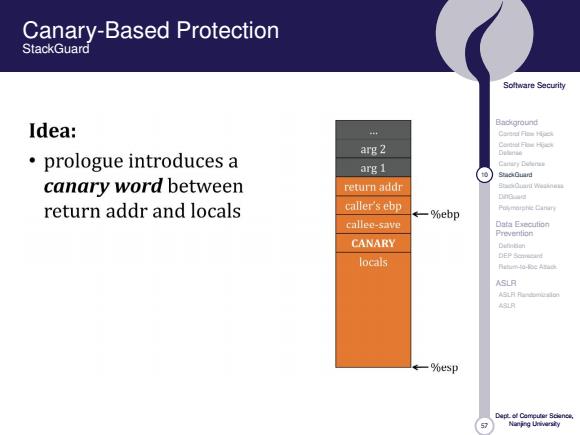
Canary-Based Protection StackGuard Soltware Security Idea: Background arg 2 e prologue introduces a arg 1 Cattary Dodenzs © ShackCurd canary word between return addr StaCianf Waaanat DnG return addr and locals caller's ebp ←-%ebp Puymnishie Cinin callee-save Data Execution Prevention CANARY Dutindan locals ASLR A9月 一%esp
57 Software Security Background Control Flow Hijack Control Flow Hijack Defense Canary Defense 10 StackGuard StackGuard Weakness DiffGuard Polymorphic Canary Data Execution Prevention Definition DEP Scorecard Return-to-libc Attack ASLR ASLR Randomization ASLR Dept. of Computer Science, Nanjing University Canary-Based Protection StackGuard