正在加载图片...
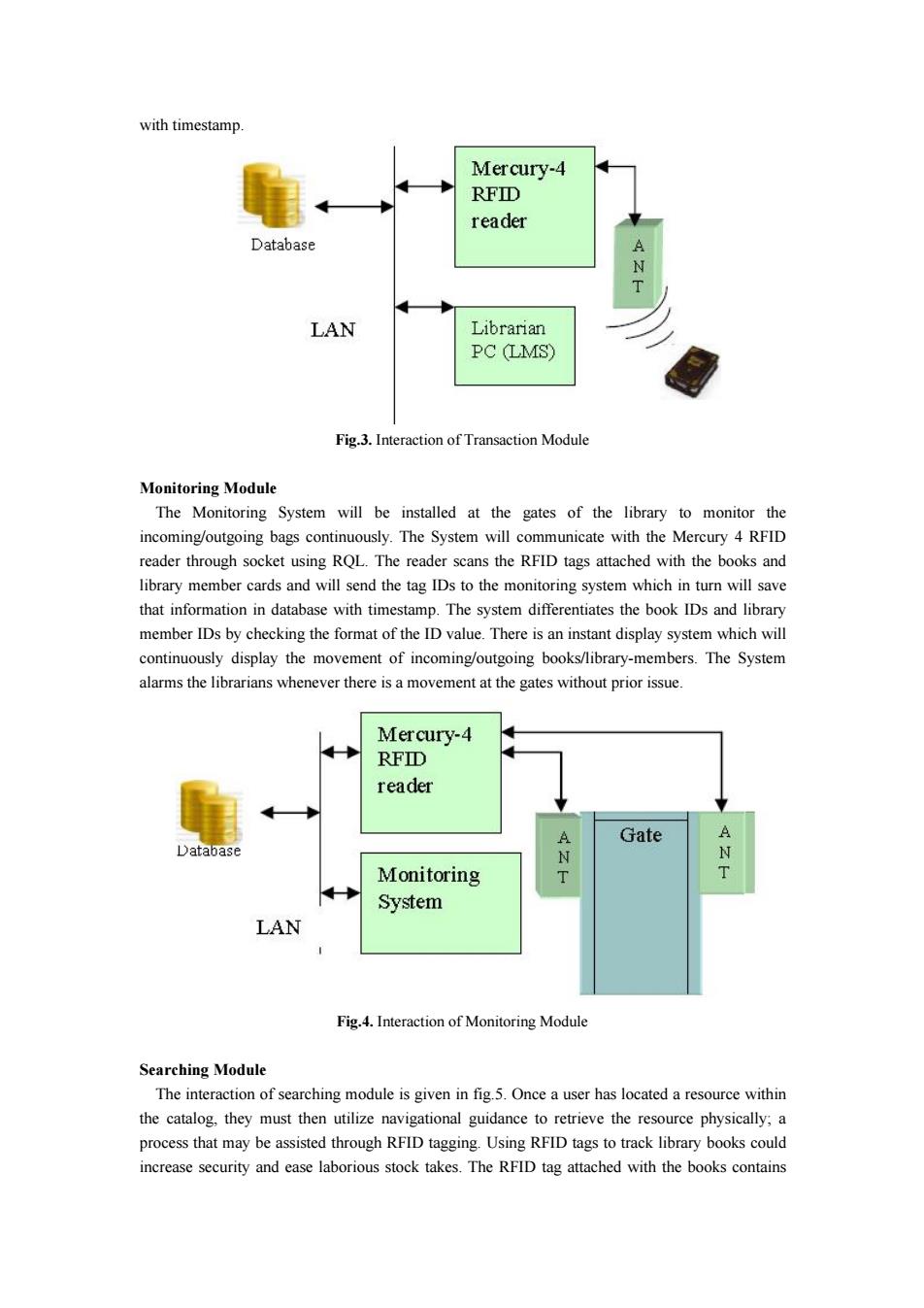
with timestamp. Mercury-4 RFID reader Database A 入 LAN Librarian PC LMS) Fig.3.Interaction of Transaction Module Monitoring Module The Monitoring System will be installed at the gates of the library to monitor the incoming/outgoing bags continuously.The System will communicate with the Mercury 4 RFID reader through socket using RQL.The reader scans the RFID tags attached with the books and library member cards and will send the tag IDs to the monitoring system which in turn will save that information in database with timestamp.The system differentiates the book IDs and library member IDs by checking the format of the ID value.There is an instant display system which will continuously display the movement of incoming/outgoing books/library-members.The System alarms the librarians whenever there is a movement at the gates without prior issue. Mercury-4 RFID reader Gate Database Monitoring T T System LAN Fig.4.Interaction of Monitoring Module Searching Module The interaction of searching module is given in fig.5.Once a user has located a resource within the catalog,they must then utilize navigational guidance to retrieve the resource physically;a process that may be assisted through RFID tagging.Using RFID tags to track library books could increase security and ease laborious stock takes.The RFID tag attached with the books containswith timestamp. Fig.3. Interaction of Transaction Module Monitoring Module The Monitoring System will be installed at the gates of the library to monitor the incoming/outgoing bags continuously. The System will communicate with the Mercury 4 RFID reader through socket using RQL. The reader scans the RFID tags attached with the books and library member cards and will send the tag IDs to the monitoring system which in turn will save that information in database with timestamp. The system differentiates the book IDs and library member IDs by checking the format of the ID value. There is an instant display system which will continuously display the movement of incoming/outgoing books/library-members. The System alarms the librarians whenever there is a movement at the gates without prior issue. Fig.4. Interaction of Monitoring Module Searching Module The interaction of searching module is given in fig.5. Once a user has located a resource within the catalog, they must then utilize navigational guidance to retrieve the resource physically; a process that may be assisted through RFID tagging. Using RFID tags to track library books could increase security and ease laborious stock takes. The RFID tag attached with the books contains