正在加载图片...
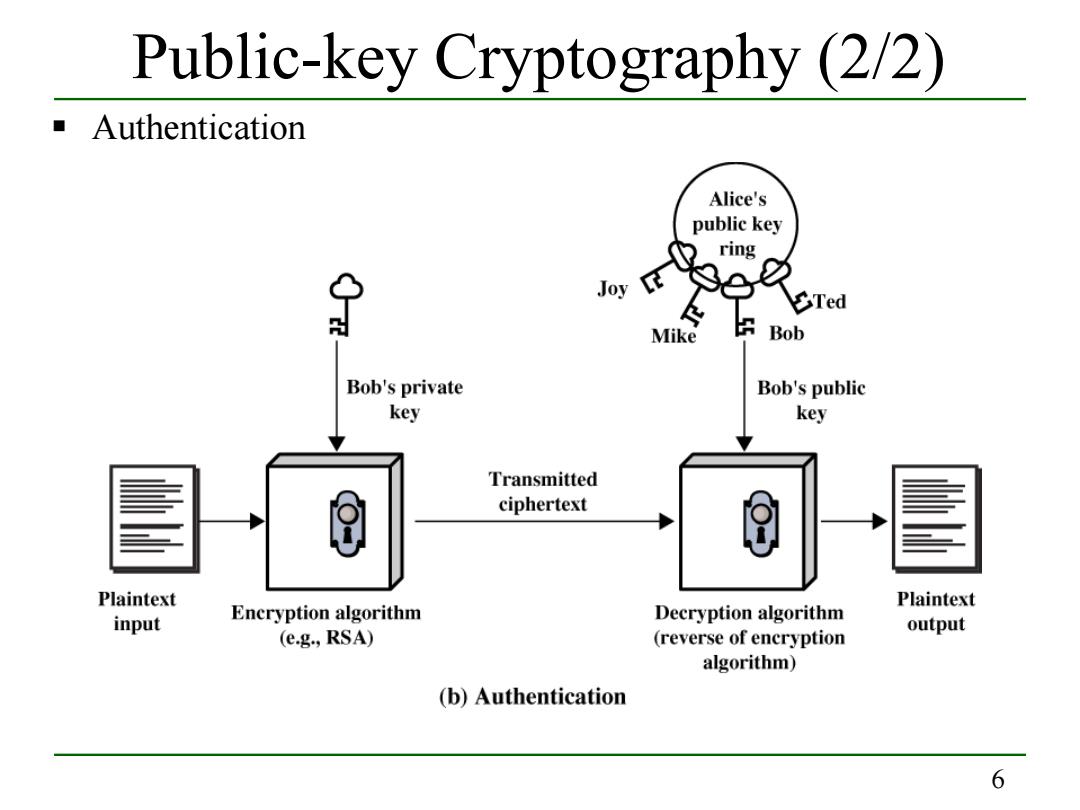
Public-key Cryptography (2/2) Authentication Alice's public key ring Joy 9e1 必 Ted Mike Bob Bob's private Bob's public key key Transmitted ciphertext Plaintext Plaintext Decryption algorithm input Encryption algorithm output (e.g.,RSA) (reverse of encryption algorithm) (b)Authentication 66 Public-key Cryptography (2/2) Authentication