正在加载图片...
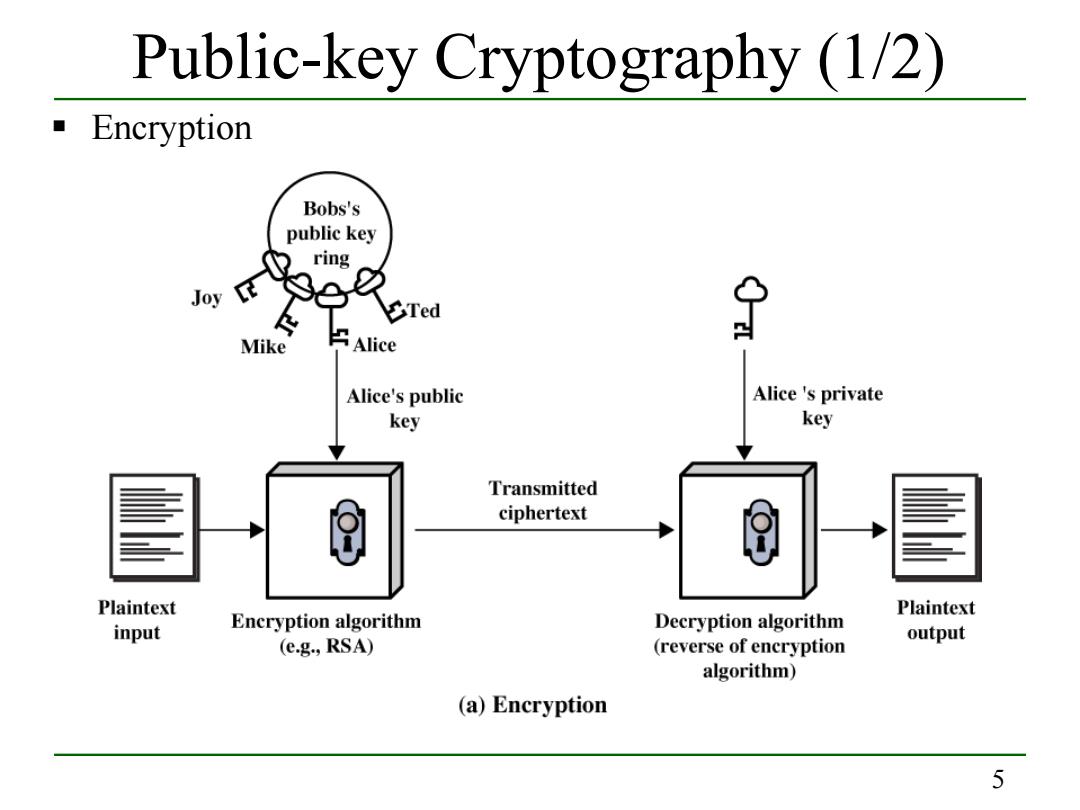
Public-key Cryptography (1/2) Encryption Bobs's public key ring Joy Mike Alice Alice's public Alice 's private key key Transmitted ciphertext Plaintext Plaintext input Encryption algorithm Decryption algorithm (e.g.,RSA) output (reverse of encryption algorithm) (a)Encryption 55 Public-key Cryptography (1/2) Encryption