
主流操作系统的安全技术 Linux/Unix安全技术 Vindows安全技术 1958 嵌入式系统实验室 2/90 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
2/90 主流操作系统的安全技术 ❖Linux/Unix安全技术 ❖Windows安全技术
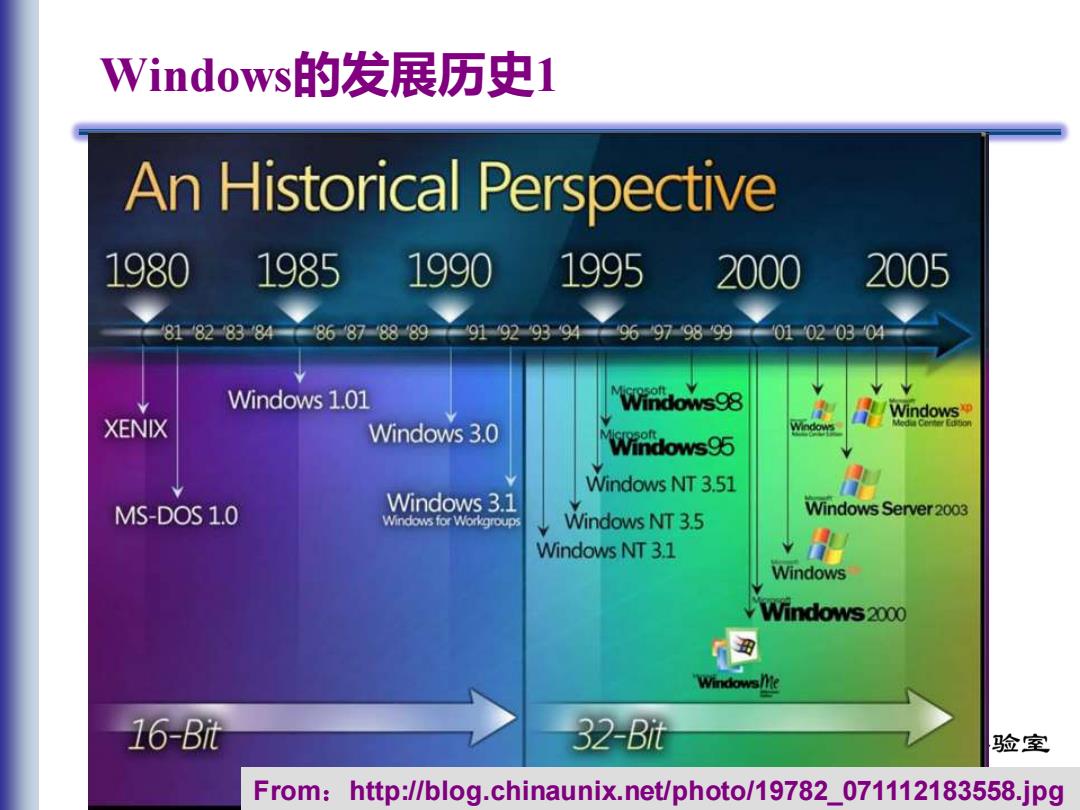
Windows的发展历史1 An Historical Perspective 1980 1985 1990 1995 2000 2005 8182838486878889 919293949697989901020304 Windows 1.01 Windows98 Windows XENIX Windows 3.0 Windows95 Windows NT 3.51 MS-DOS 1.0 Windows 3.1 Windows for Workgroups Windows NT 3.5 Windows Server 2003 Windows NT 3.1 Windows Windows 2000 WindowsMie 16-Bt 32-Bt 验室 From:http://blog.chinaunix.net/photo/19782_071112183558.jpg
3/90 Windows的发展历史1 From:http://blog.chinaunix.net/photo/19782_071112183558.jpg

Vindows的发展历史2 Windows 1.0 2.0 3.0 3.1 Medla Center 2003 Media Center 2005 XP foc x64 31 3.11 95 98 Millennium Fundamentals for Legacy PCs 3.11 WMWG Starter Edition OSR1 98SE OSR2 XP OSR2.5 XP SP2 Vista OSR3 Home NT Professional 2000 XP for IA64 Server Media Center 2003 Workstation Professional Embedded Server Server Multiple Advanced Server Advanced Server varants Data Center Adv Server IA64 Datacenter IA64 1985 1987 1990 1992 1995 1998 2000 2002 2006 From:http://www.xuecs.com/img/upload/osx/windows.jpg 嵌入式系统实验室 4/90 EMBEDDED SYSTEM LABORATORY 百uE料DUAN0 ITUTE FOR AOVANCED5 FUOY DF U百TC
4/90 Windows的发展历史2 From:http://www.xuecs.com/img/upload/osx/windows.jpg
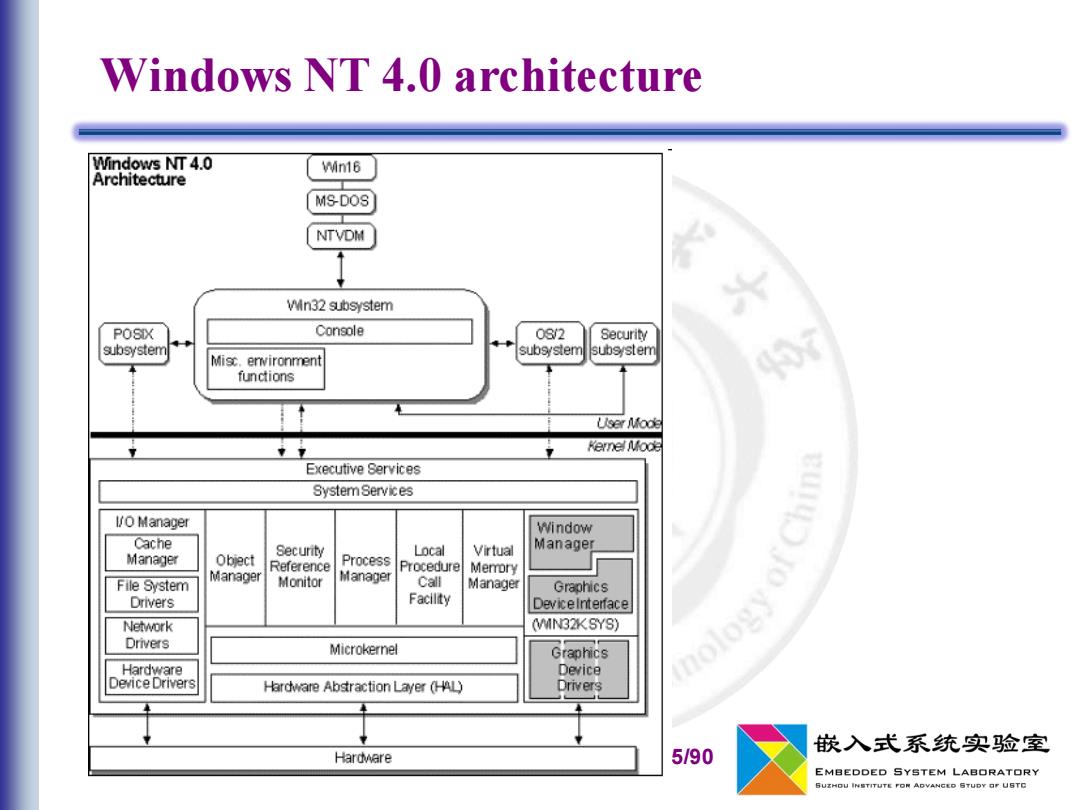
Windows NT 4.0 architecture Windows NT 4.0 Win16 Architecture MS-DOS NTVDM Win32 subsystem POSIX Console 082 Security subsystem subsystem subsystem Misc.ervironment functions User MMode Kernel MMode Executive Services SystemServices lO Manager Window Cache Manager Object Security Local Virtual Manager Process Procedurel File System Manager Reference Memory Monitor Manager Call Manager Graphics Drivers Facilty Devicelnterface Network (IN32KSYS) Drivers hology of China Microkernel Graphics Hardware Device Device Drivers Hardware Abstraction Layer (HAL) Drivers 嵌入式系统实验室 Hardware 5/90 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
5/90 Windows NT 4.0 architecture
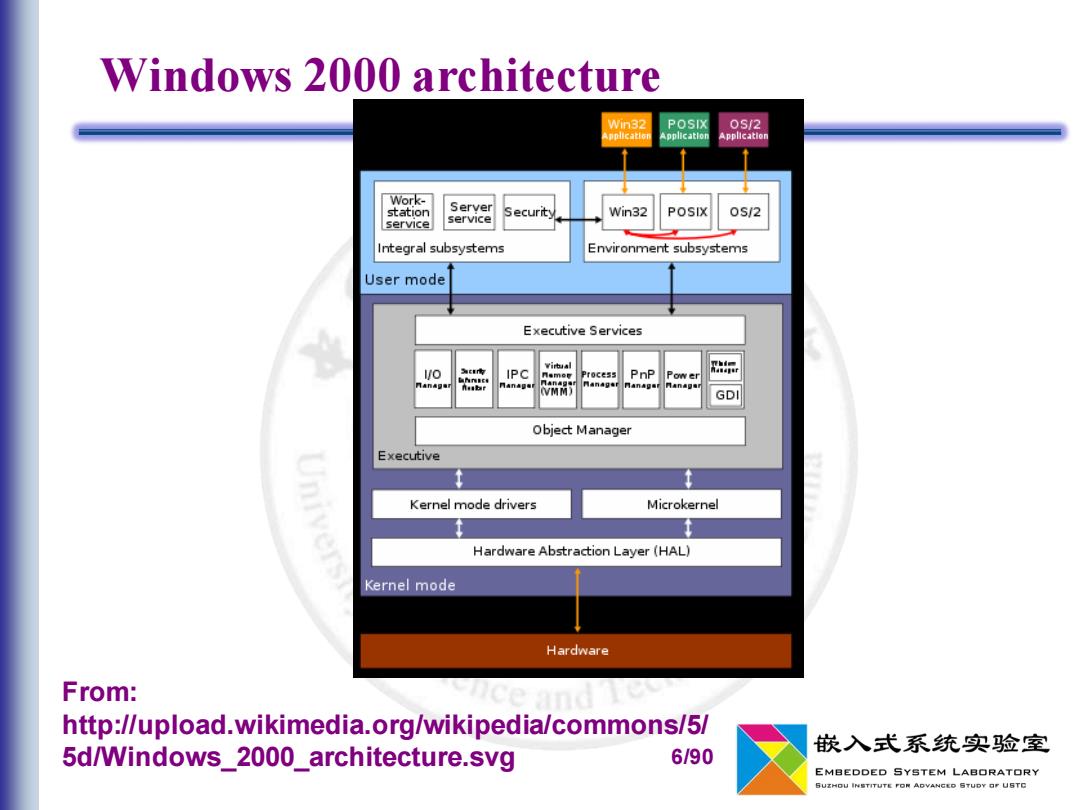
Windows 2000 architecture Win32 POSIX 0S2 Application Application Application Work- station Server Securty Win32 POSIX 0S/2 service service Integral subsystems Environment subsystems User mode Executive Services 量b。 lO IPC 门smer Process PnP 品 n。。t 门n4日 GDI Object Manager Executive Kernel mode drivers Microkernel Hardware Abstraction Layer(HAL) Kernel mode Hardware From: http://upload.wikimedia.org/wikipedia/commons/5/ 5d/Windows_2000_architecture.svg 嵌入式系统实验室 6/90 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
6/90 Windows 2000 architecture From: http://upload.wikimedia.org/wikipedia/commons/5/ 5d/Windows_2000_architecture.svg

Vindows安全:NT是分水岭 NT设计目标:TCSEC标准的C2级 >在用户级实现自主访问控制 >提供对客体的访问的审计机制 >实现客体重用 Windows NT 4.0 1958 >1999年11月通过美国国防部TCSEC C2级安全认证 >Windows NT安全子系统 ●提供身份鉴别、自主访问控制、客体共享和安全审计等安全 特性。 ● 主要由本地安全授权(LSA)、安全账户管理(SAM)和安 全参考监视器(SRM)等组成 嵌入式系统实验室 7190 EMBEDDED SYSTEM LABORATORY 5uE料DUN0 ITUTE FOR AOVANCED5 UOY DF U百TC
7/90 Windows安全:NT是分水岭 ❖NT设计目标:TCSEC标准的C2级 ➢在用户级实现自主访问控制 ➢提供对客体的访问的审计机制 ➢实现客体重用 ❖Windows NT 4.0 ➢1999年11月通过美国国防部TCSEC C2级安全认证 ➢Windows NT安全子系统 ⚫提供身份鉴别、自主访问控制、客体共享和安全审计等安全 特性。 ⚫主要由本地安全授权(LSA)、安全账户管理(SAM)和安 全参考监视器(SRM)等组成

"[security]...really is a journey rather than a destination." 1958 From:Hacking Exposed Windows:Windows Security Secrets Solutions Bill Gates,"Trustworthy Computing",January 2002 Refer:http://www.microsoft.com/mscorp/execmail/2002/07-18twc.mspx 嵌入式系统实验室 8/90 EMBEDDED SYSTEM LABORATORY 5uE料DUAN0 ITUTE FOR AOVANCED5 FUOY OF U百TC
8/90 From:Hacking Exposed Windows: Windows Security Secrets & Solutions Bill Gates,“Trustworthy Computing”,January 2002 Refer:http://www.microsoft.com/mscorp/execmail/2002/07-18twc.mspx “[security]… really is a journey rather than a destination

security wheel What asset am I trying to secure? What are the asset's security requirements? What are the risks unique to that asset's security requirements? How do I prioritize and most efficiently address those risks(especially those with heavy impact such as industry and regulatory compliance requirements)? Plan Incident response(IR) Education and training ●Remediation Communications ●Audit resolution Respond Prevent Security operations ●Recovery Rinse and Repeat Security architecture Detect Automated vulnerability scanning Security event and information management(SEIM) Intrusion detection systems (IDS) Anomaly detection systems(ADS) Security audits (including penetration testing) 、嵌入式系统实验室 From:Hacking Exposed Windows:Windows Security Secrets Solutions
9/90 security wheel From:Hacking Exposed Windows: Windows Security Secrets & Solutions

Kernel User 物理逻辑 Security context Connect As.. ☒ By defaut,you ml connect to the network foider as RIOUoel To connect as anocher user,enter their user name and password below. User name: user Eassword: 88088●0年 Attacking Windows security using both kernel and user mode approaches
10/90 The Windows Security Architecture from the Hacker’s Perspective Attacking Windows security using both kernel and user mode approaches 物理/逻辑

Vindows安全技术 Vindows NT/2000/XP中的常用安全技术 >Windows!身份验证与访问控制 >Windows审核机制 >Windows注册表 >Windows加密文件系统 >Windowsz基准安全注意事项 Windows2003中的新安全技术简介 of Science and Technol 嵌入式系统实验室 11/90 EMBEDDED SYSTEM LABORATORY SUZHOU INSTITUTE FON ADVANCED STUDY OF USTC
11/90 Windows安全技术 ❖Windows NT/2000/XP中的常用安全技术 ➢Windows身份验证与访问控制 ➢Windows审核机制 ➢Windows注册表 ➢Windows加密文件系统 ➢Windows基准安全注意事项 ❖Windows 2003中的新安全技术简介