
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Unit 3 Traffic Policing and Shaping 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.1
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.1 Unit 3 Traffic Policing and Shaping

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Roadmap Traffic Shaping and Policing -What and why is traffic shaping and traffic policing Leaky Bucket Token Bucket Traffic -Generic Cell Rate Algorithm (GCRA) -Virtual scheduling algorithm implementati Leaky bucket algorithm implementation 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.2
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.2 Roadmap • Traffic Shaping and Policing What and why is traffic shaping and traffic policing Leaky Bucket Token Bucket Traffic Generic Cell Rate Algorithm (GCRA) -Virtual scheduling algorithm implementati - Leaky bucket algorithm implementation

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Traffic Policing Question: A connection accepted by CAC,it's QoS can be satisfied,if the source obeys the traffic descriptor.What happens if the traffic flow violates the initial contract? Answer: The network may not maintain acceptable performance What can be done? Traffic Policing is performed by the network to ensure that the parameter specified by the user are being complied. Traffic Policing The process of monitoring and enforcing the traffic flow What Traffic Policing do? Discard the nonconforming traffic S Tag the nonconforming traffic with lower priority) 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.3
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.3 Traffic Policing • Question: A connection accepted by CAC, it’s QoS can be satisfied, if the source obeys the traffic descriptor. What happens if the traffic flow violates the initial contract? • Answer: The network may not maintain acceptable performance • What can be done? Traffic Policing is performed by the network to ensure that the parameter specified by the user are being complied. • Traffic Policing The process of monitoring and enforcing the traffic flow • What Traffic Policing do? §Discard the nonconforming traffic §Tag the nonconforming traffic ( with lower priority)
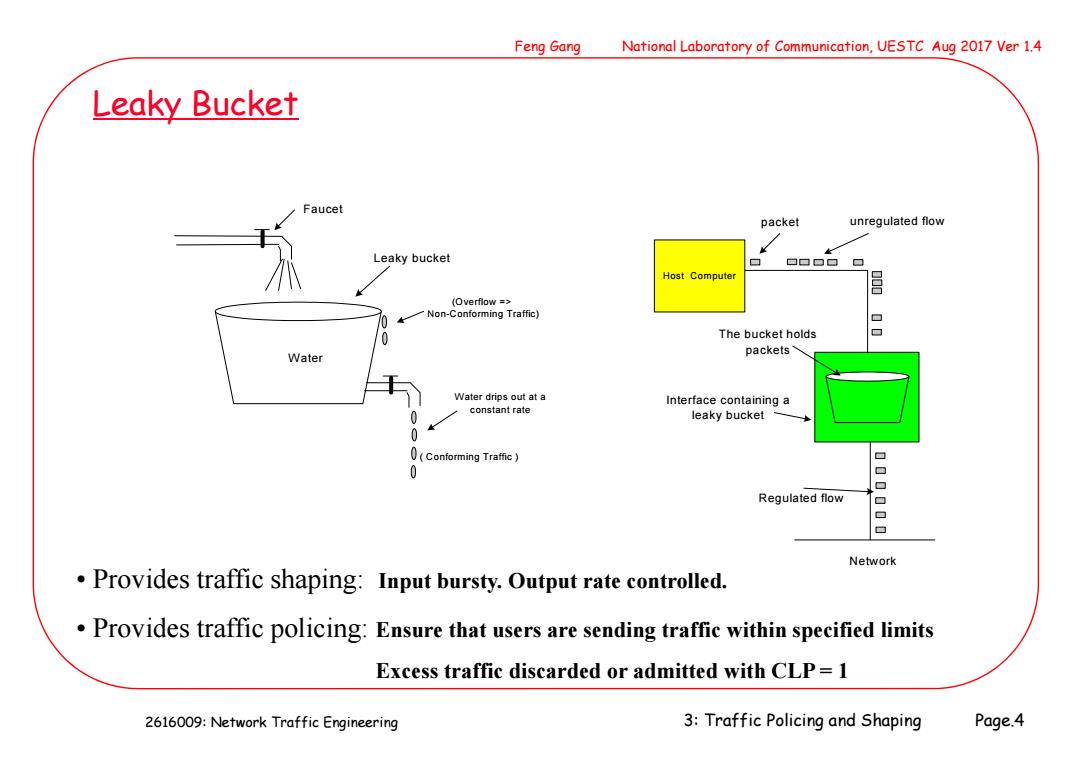
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Leaky Bucket Faucet packet unregulated flow Leaky bucket Host Compute (Overflow = Non-Conforming Traffic) The bucket holds packets Water Water drips out at a Interface containing a constant rate 0 leaky bucket 0 0(Conforming Traffic) 回 0 Regulated flow 口 Network Provides traffic shaping:Input bursty.Output rate controlled. Provides traffic policing:Ensure that users are sending traffic within specified limits Excess traffic discarded or admitted with CLP=1 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.4
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.4 Leaky Bucket Faucet Leaky bucket Water drips out at a constant rate (Overflow => Non-Conforming Traffic) ( Conforming Traffic ) Water unregulated flow Host Computer Network packet The bucket holds packets Regulated flow Interface containing a leaky bucket • Provides traffic shaping: Input bursty. Output rate controlled. • Provides traffic policing: Ensure that users are sending traffic within specified limits Excess traffic discarded or admitted with CLP = 1
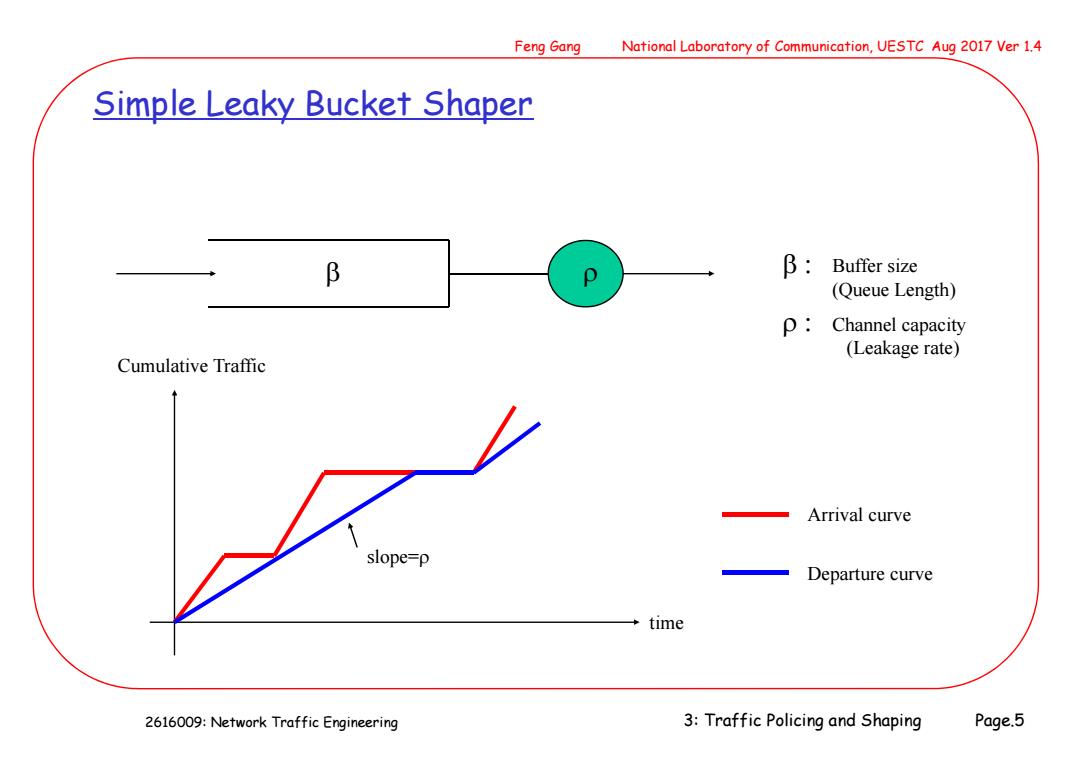
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Simple Leaky Bucket Shaper B β: Buffer size (Queue Length) p:Channel capacity (Leakage rate) Cumulative Traffic Arrival curve slope=p Departure curve time 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.5
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.5 Simple Leaky Bucket Shaper b Cumulative Traffic slope= time Arrival curve Departure curve b: : Buffer size (Queue Length) Channel capacity (Leakage rate)

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Design Example Sender max.transmission rate of 200Mbps Router capacity is 16Mbps Application generates data in burst of 8Mb,with a burst length of 40ms,once every second. ☑ Application Router 200Mbps Leaky-Bucket 16Mbps 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.6
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.6 - Sender max. transmission rate of 200Mbps - Router capacity is 16Mbps - Application generates data in burst of 8Mb, with a burst length of 40ms, once every second. Application Leaky-Bucket Router 200Mbps 16Mbps Design Example

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Design Example First make sure the router can possibly handle the traffic: Average data rate generated by application is: Total 8Mb/1s 8Mbps router's capacity (16Mbps) Then determines Cfor the leaky bucket: 200Mbps →16Mbps Let A be arrival rate,and Tbe burst length (in seconds),then C>max{(total received in time f)-(total tx in time )Vf =A*t-*t=(A-0t =(200-16)*0.04 =7.36Mbor0.92MB 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.7
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.7 Design Example • First make sure the router can possibly handle the traffic: • Then determines C for the leaky bucket: Average data rate generated by application is: Total = 8Mb/1s = 8Mbps < router’s capacity (16Mbps) 200Mbps 16Mbps C Let A be arrival rate, and T be burst length (in seconds), then C max{(total received in time t)-(total tx in time t)|"t} = A*t - r*t = (A-r)t = (200-16)*0.04 = 7.36Mb or 0.92MB
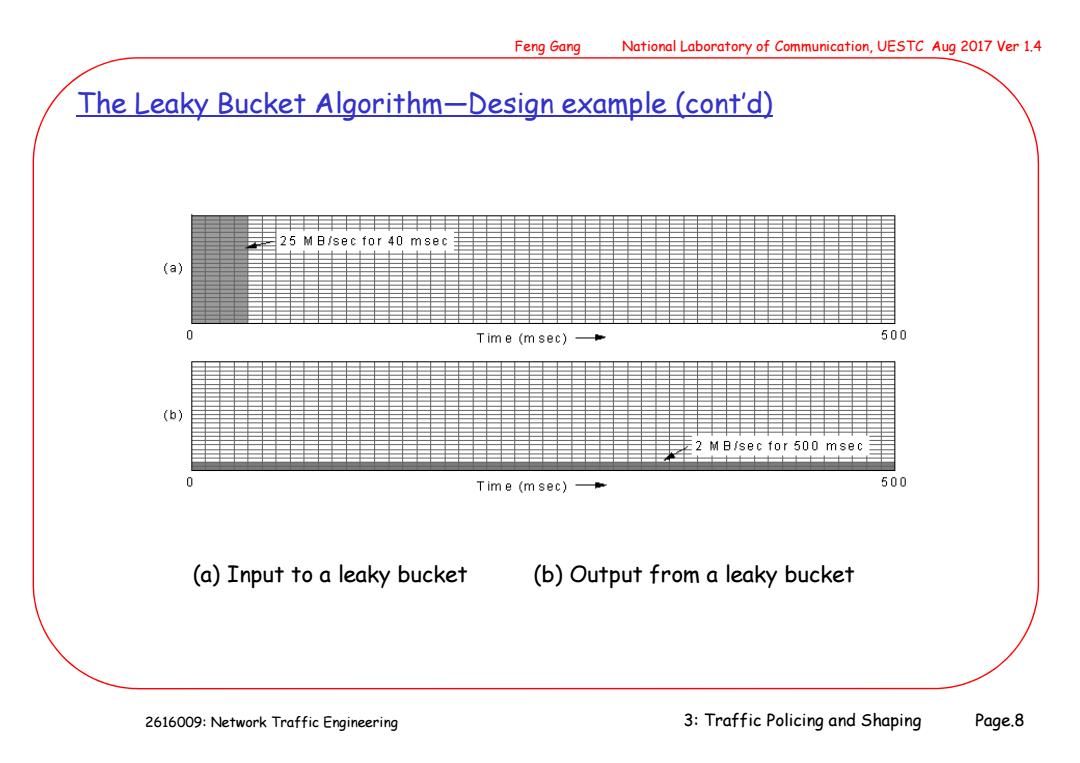
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 The Leaky Bucket Algorithm-Design example (cont'd) 目 25M日/sec for40msec (a】 Tim e (m sec)- 500 (b) 2M日sec for500msec Tim e (m sec) 500 (a)Input to a leaky bucket (b)Output from a leaky bucket 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.8
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.8 The Leaky Bucket Algorithm—Design example (cont’d) (a) Input to a leaky bucket (b) Output from a leaky bucket

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Token Bucket Traffic Shaper Why a token bucket traffic shaper? S Leaky bucket:the output rate is constant when the buffer is not empty: only CBR is allowed. Token Bucket Shaper (Dual-bucket Shaper) §2 buckets One buffer for data One buffer for a pool of tokens:tokens are generated at a constant rate S More flexible:allows for some burstiness in the traffic as long as it is under a certain limit Conforming packets are passed through without further delay 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.9
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.9 Token Bucket Traffic Shaper • Why a token bucket traffic shaper? §Leaky bucket: the output rate is constant when the buffer is not empty: only CBR is allowed. • Token Bucket Shaper (Dual-bucket Shaper) §2 buckets – One buffer for data – One buffer for a pool of tokens: tokens are generated at a constant rate §More flexible: allows for some burstiness in the traffic as long as it is under a certain limit §Conforming packets are passed through without further delay

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 The Token Bucket Algorithm Host Host com puter com puter One token is added The bucket to the buck et holds every△T tokens Networks Networks (a) (b) (a)before (a)after 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.10
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.10 The Token Bucket Algorithm (a) before (a) after