
Computer Networking Chapter 5 A Top-Down Approach Link Layer KUROSE ROSS A note on the use of these ppt slides: Computer We're making these slides freely available to all(faculty,students,readers). They're in PowerPoint form so you see the animations;and can add,modify. Networking:A and delete slides (including this one)and slide content to suit your needs. They obviously represent a lot of work on our part.In return for use,we only Top Down ask the following: If you use these slides (e.g.,in a class)that you mention their source Approach (after all,we'd like people to use our book!) 6th edition If you post any slides on a www site,that you note that they are adapted from (or perhaps identical to)our slides,and note our copyright of this Jim Kurose,Keith Ross material. Addison-Wesley Thanks and enjoy!JFK/KWR March 2012 t Reserved Link Layer 5-1
Chapter 5 Link Layer Computer Networking: A Top Down Approach 6th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) If you post any slides on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Thanks and enjoy! JFK/KWR All material copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved Link Layer 5-1
Chapter 5:Link layer our goals: understand principles behind link layer services: error detection,correction sharing a broadcast channel:multiple access link layer addressing local area networks:Ethernet,VLANs instantiation,implementation of various link layer technologies Link Layer 5-2
Link Layer 5-2 Chapter 5: Link layer our goals: understand principles behind link layer services: error detection, correction sharing a broadcast channel: multiple access link layer addressing local area networks: Ethernet, VLANs instantiation, implementation of various link layer technologies
Link layer,LANS:outline 5.1 introduction. 5.5 link virtualization: services MPLS 5.2 error detection, 5.6 data center correction networking 5.3 multiple access 5.7 a day in the life of a protocols web request 5.4 LANs addressing,ARP Ethernet ■switches ·VLANS Link Layer 5-3
Link Layer 5-3 Link layer, LANs: outline 5.1 introduction, services 5.2 error detection, correction 5.3 multiple access protocols 5.4 LANs addressing, ARP Ethernet switches VLANS 5.5 link virtualization: MPLS 5.6 data center networking 5.7 a day in the life of a web request
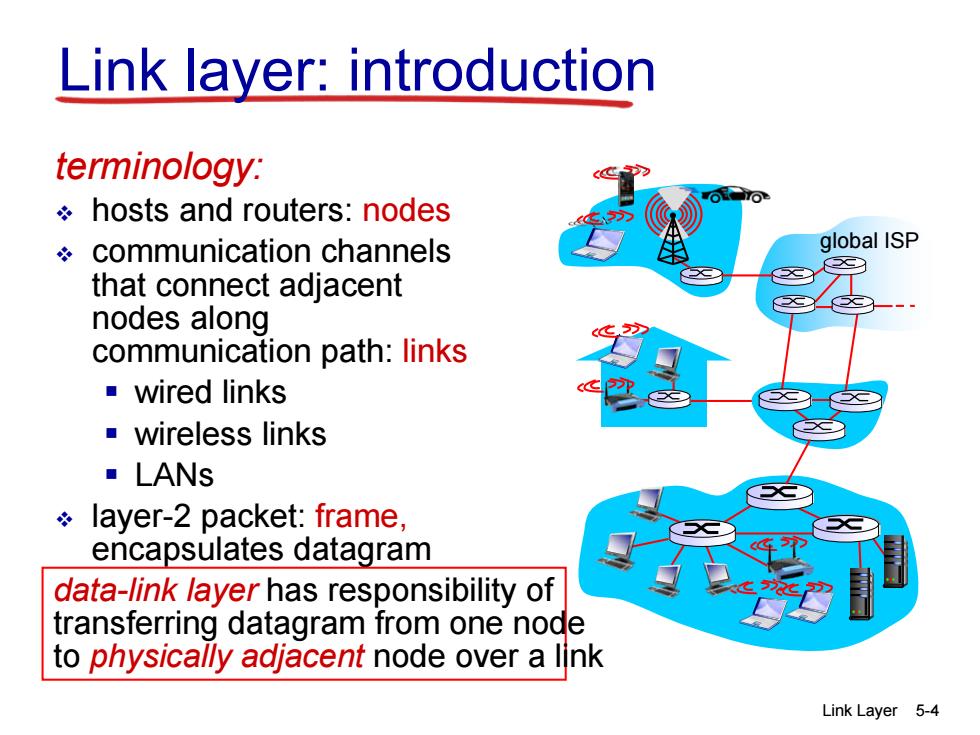
Link layer:introduction terminology: hosts and routers:nodes communication channels global ISP that connect adjacent nodes along communication path:links wired links ■wireless links ■LANS layer-2 packet:frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to physically adjacent node over a link Link Layer 5-4
Link Layer 5-4 Link layer: introduction terminology: hosts and routers: nodes communication channels that connect adjacent nodes along communication path: links wired links wireless links LANs layer-2 packet: frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to physically adjacent node over a link global ISP
Link layer:context datagram transferred by transportation analogy: different link protocols trip from Princeton to Lausanne over different links: limo:Princeton to JFK e.g.,Ethernet on first ■plane:JFK to Geneva link,frame relay on train:Geneva to Lausanne intermediate links, tourist datagram 802.11 on last link transport segment each link protocol communication link provides different services transportation mode link e.g.,may or may not layer protocol provide rdt over link travel agent routing algorithm Link Layer 5-5
Link Layer 5-5 Link layer: context datagram transferred by different link protocols over different links: e.g., Ethernet on first link, frame relay on intermediate links, 802.11 on last link each link protocol provides different services e.g., may or may not provide rdt over link transportation analogy: trip from Princeton to Lausanne limo: Princeton to JFK plane: JFK to Geneva train: Geneva to Lausanne tourist = datagram transport segment = communication link transportation mode = link layer protocol travel agent = routing algorithm

Link layer services framing,link access: encapsulate datagram into frame,adding header, trailer channel access if shared medium ■“MAC”addresses used in frame headers to identify source,dest ·different from IP address! reliable delivery between adjacent nodes ■we learned how to do this already(chapter3)! seldom used on low bit-error link(fiber,some twisted pair) wireless links:high error rates Q:why both link-level and end-end reliability? Link Layer 5-6
Link Layer 5-6 Link layer services framing, link access: encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! reliable delivery between adjacent nodes we learned how to do this already (chapter 3)! seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability?
Link layer services (more) ÷flow control:. pacing between adjacent sending and receiving nodes error detection: errors caused by signal attenuation,noise. receiver detects presence of errors: signals sender for retransmission or drops frame error correction: receiver identifies and corrects bit error(s)without resorting to retransmission half-duplex and full-duplex with half duplex,nodes at both ends of link can transmit,but not at same time Link Layer 5-7
Link Layer 5-7 flow control: pacing between adjacent sending and receiving nodes error detection: errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame error correction: receiver identifies and corrects bit error(s) without resorting to retransmission half-duplex and full-duplex with half duplex, nodes at both ends of link can transmit, but not at same time Link layer services (more)
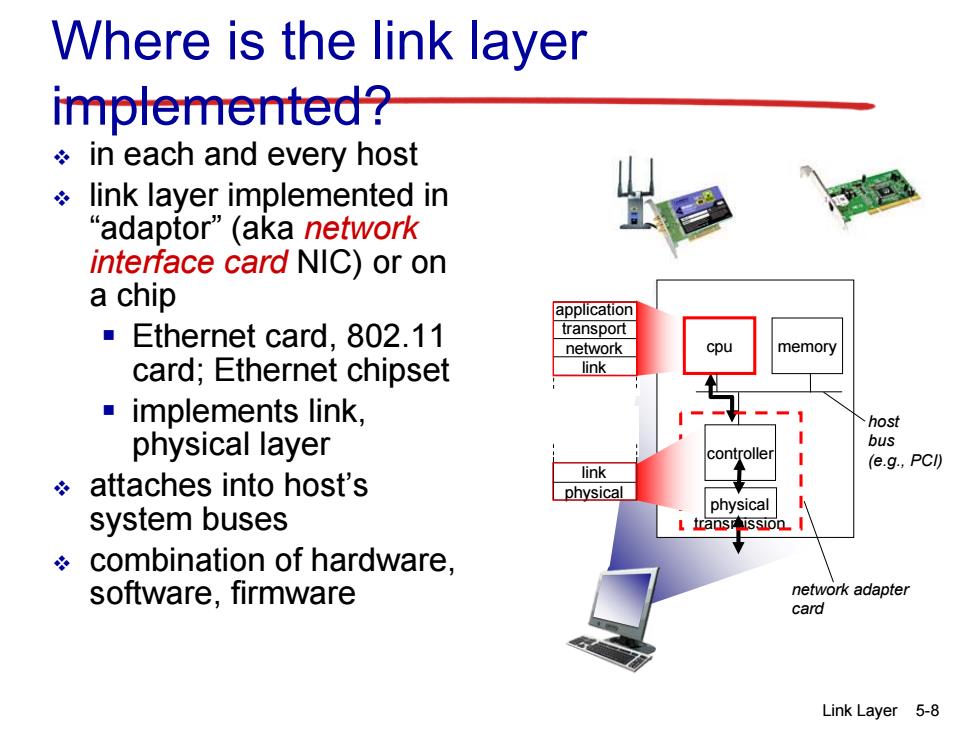
Where is the link layer implemented? ÷in each and every host link layer implemented in "adaptor"(aka network interface card NIC)or on a chip application Ethernet card,802.11 transport network cpu memory card;Ethernet chipset link implements link, host physical layer bus link (e.g.,PCI) attaches into host's physical physical system buses L transrission combination of hardware, software,firmware network adapter card Link Layer 5-8
Link Layer 5-8 Where is the link layer implemented? in each and every host link layer implemented in “adaptor” (aka network interface card NIC) or on a chip Ethernet card, 802.11 card; Ethernet chipset implements link, physical layer attaches into host’s system buses combination of hardware, software, firmware controller physical transmission cpu memory host bus (e.g., PCI) network adapter card application transport network link link physical
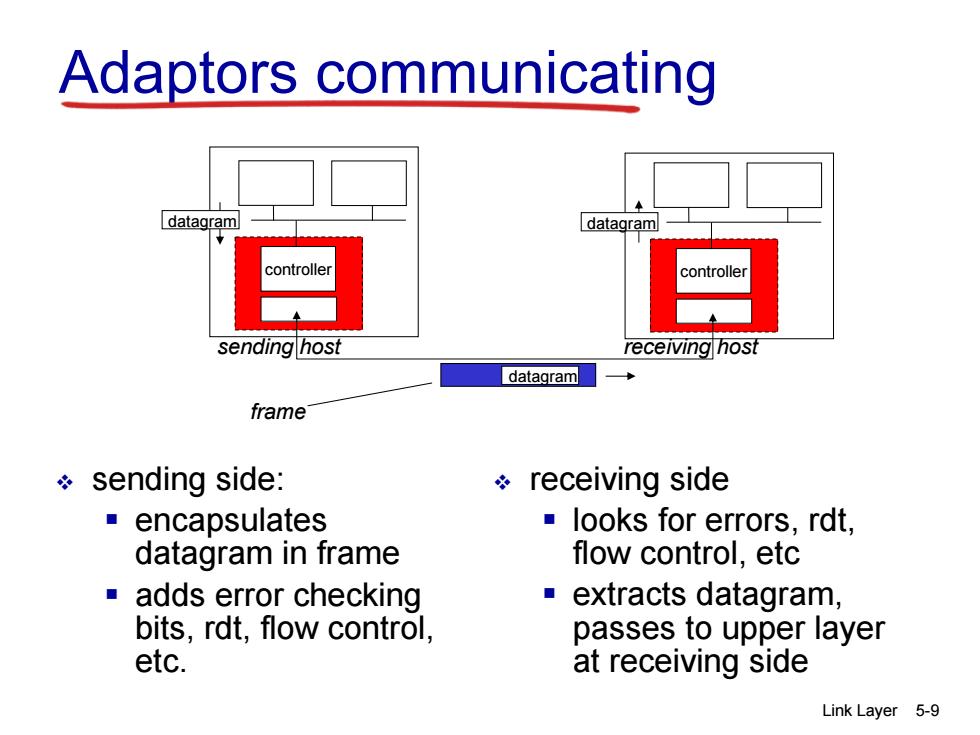
Adaptors communicating datagram datagram ontrolle controller sending host receiving host datagram frame sending side: ÷receiving side ■encapsulates looks for errors,rdt, datagram in frame flow control,etc ■adds error checking extracts datagram, bits,rdt,flow control, passes to upper layer etc. at receiving side Link Layer 5-9
Link Layer 5-9 Adaptors communicating sending side: encapsulates datagram in frame adds error checking bits, rdt, flow control, etc. receiving side looks for errors, rdt, flow control, etc extracts datagram, passes to upper layer at receiving side controller controller sending host receiving host datagram datagram datagram frame
Link layer,LANS:outline 5.1 introduction, 5.5 link virtualization: services MPLS 5.2 error detection, 5.6 data center correction networking 5.3 multiple access 5.7 a day in the life of a protocols web request 5.4 LANs ·addressing,ARP a Ethernet ■switches VLANS Link Layer 5-10
Link Layer 5-10 Link layer, LANs: outline 5.1 introduction, services 5.2 error detection, correction 5.3 multiple access protocols 5.4 LANs addressing, ARP Ethernet switches VLANS 5.5 link virtualization: MPLS 5.6 data center networking 5.7 a day in the life of a web request