
Advance in Intrusion Detection Techniques Associate Prof.Fang Xianjin(方贤进) Computer Science Engineering SchoolofAUST
Advance in Intrusion Detection Techniques Associate Prof. Fang Xianjin(方贤进) Computer Science & Engineering School of AUST

Outline Context of computer security problem ● Brief summaries of computer security system What is IDS? Architecture and Classification of IDS Intrusion detection techniques My current research works Questions and answer
Outline ⚫ Context of computer security problem ⚫ Brief summaries of computer security system ⚫ What is IDS? ⚫ Architecture and Classification of IDS ⚫ Intrusion detection techniques ⚫ My current research works ⚫ Questions and answer
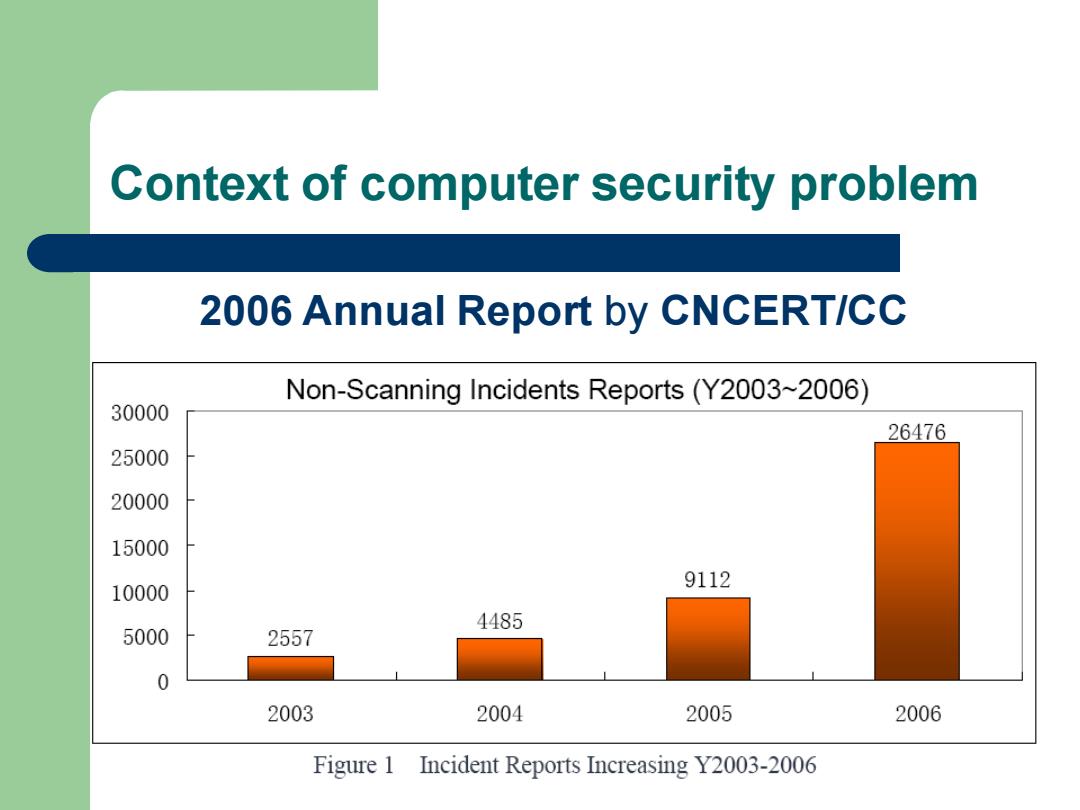
Context of computer security problem 2006 Annual Report by CNCERT/CC Non-Scanning Incidents Reports(Y2003~2006) 30000 26476 25000 20000 15000 10000 9112 4485 5000 2557 0 2003 2004 2005 2006 Figure 1 Incident Reports Increasing Y2003-2006
Context of computer security problem 2006 Annual Report by CNCERT/CC
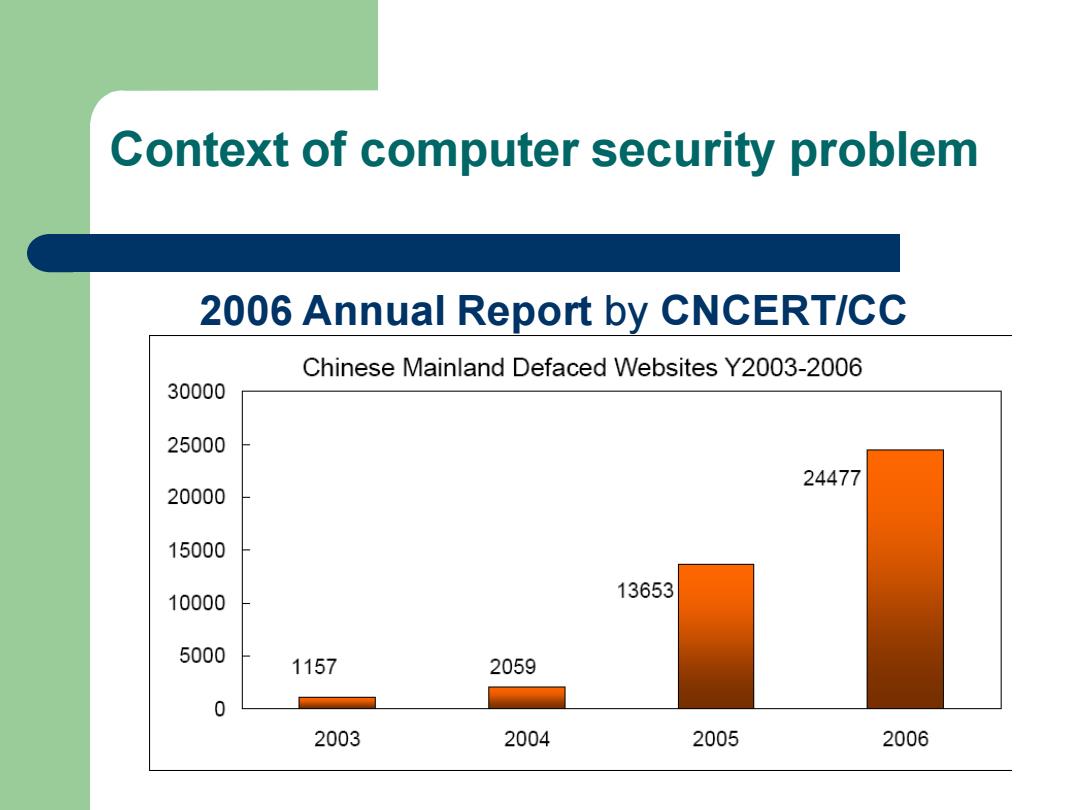
Context of computer security problem 2006 Annual Report by CNCERT/CC Chinese Mainland Defaced Websites Y2003-2006 30000 25000 24477 20000 15000 10000 13653 5000 1157 2059 0 2003 2004 2005 2006
Context of computer security problem 2006 Annual Report by CNCERT/CC
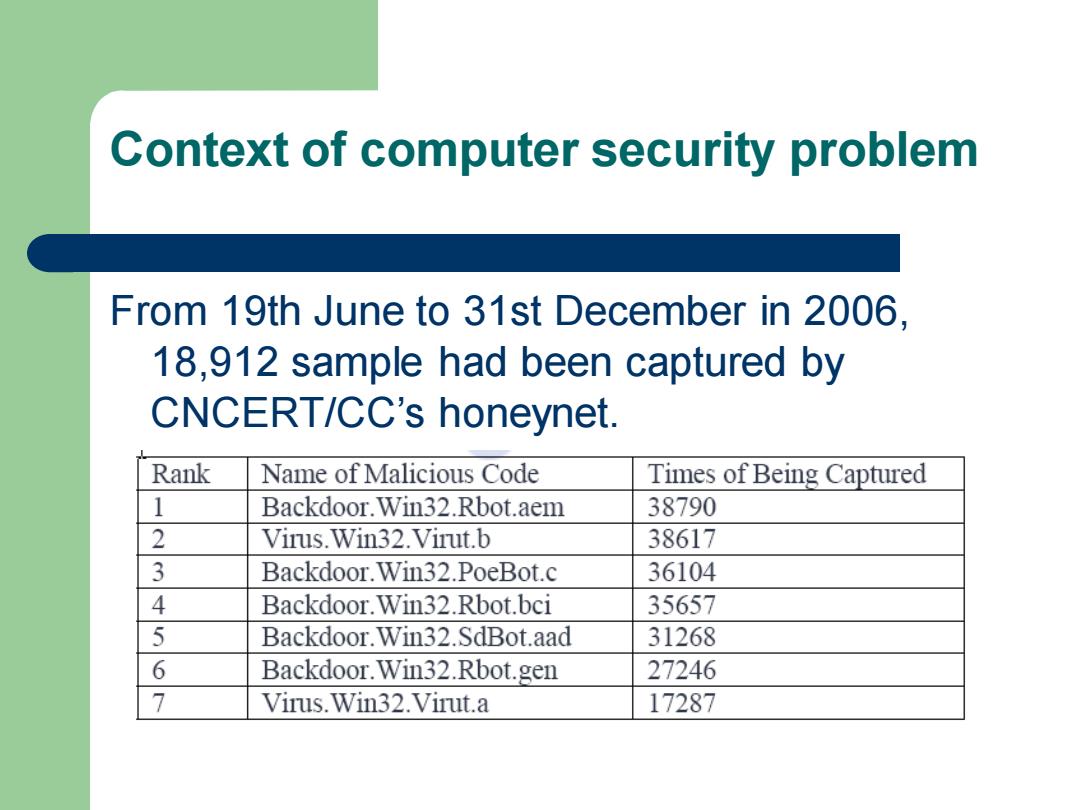
Context of computer security problem From 19th June to 31st December in 2006. 18,912 sample had been captured by CNCERT/CC's honeynet. Rank Name of Malicious Code Times of Being Captured 1 Backdoor.Win32.Rbot.aem 38790 2 Virus.Win32.Virut.b 38617 3 Backdoor.Win32.PoeBot.c 36104 4 Backdoor.Win32.Rbot.bci 35657 5 Backdoor.Win32.SdBot.aad 31268 6 Backdoor.Win32.Rbot.gen 27246 Virus.Win32.Virut.a 17287
Context of computer security problem From 19th June to 31st December in 2006, 18,912 sample had been captured by CNCERT/CC’s honeynet
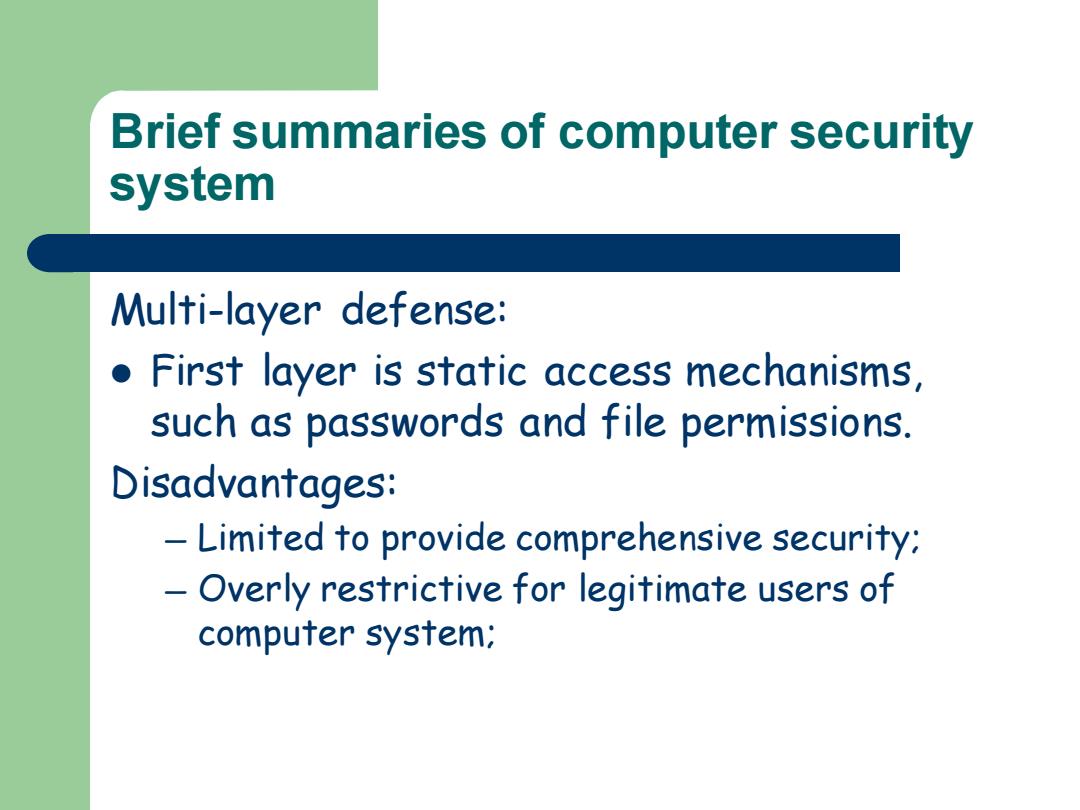
Brief summaries of computer security system Multi-layer defense: First layer is static access mechanisms, such as passwords and file permissions. Disadvantages: Limited to provide comprehensive security; Overly restrictive for legitimate users of computer system;
Brief summaries of computer security system Multi-layer defense: ⚫ First layer is static access mechanisms, such as passwords and file permissions. Disadvantages: — Limited to provide comprehensive security; — Overly restrictive for legitimate users of computer system;
Brief summaries of computer security system Multi-layer defense: second layer is cryptography,which is used for providing secure channels and host authentication Another layer is firewall,which filters out undesirable network traffic in a network system
Brief summaries of computer security system Multi-layer defense: ⚫ second layer is cryptography, which is used for providing secure channels and host authentication ⚫ Another layer is firewall, which filters out undesirable network traffic in a network system
Brief summaries of computer security system Multi-layer defense: The latest layer of defense is provided by dynamic protection systems that can detect and prevent intrusion,namely,is known as Intrusion Detection System(IDS)
Brief summaries of computer security system Multi-layer defense: ⚫ The latest layer of defense is provided by dynamic protection systems that can detect and prevent intrusion, namely, is known as Intrusion Detection System(IDS)
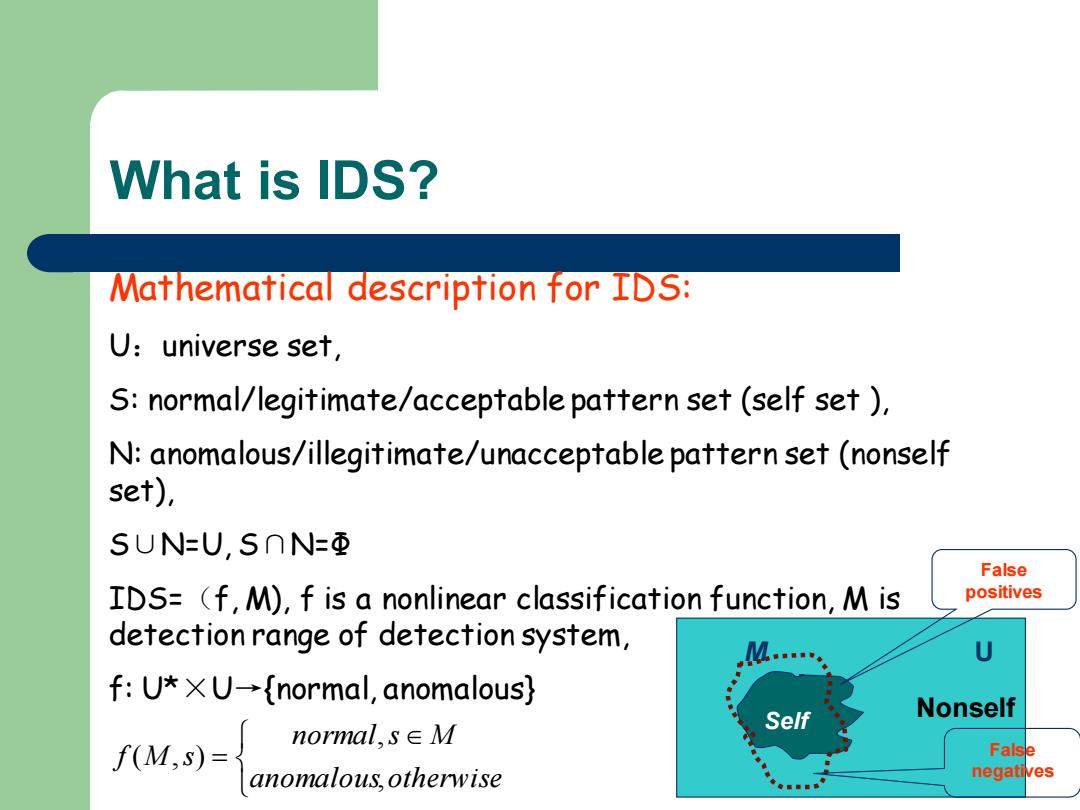
What is IDS? Mathematical description for IDS: U:universe set, S:normal/legitimate/acceptable pattern set (self set ) N:anomalous/illegitimate/unacceptable pattern set(nonself set), SUN=U,S∩N=Φ False IDS=(f,M),f is a nonlinear classification function,M is positives detection range of detection system, U f:U*×U→{normal,anomalous? Nonself normal,S∈M Self f(M,s)= False anomalous,otherwise negatives
What is IDS? Mathematical description for IDS: U:universe set, S: normal/legitimate/acceptable pattern set (self set ), N: anomalous/illegitimate/unacceptable pattern set (nonself set), S∪N=U, S∩N=Ф IDS=(f, M), f is a nonlinear classification function, M is detection range of detection system, f: U*×U→{normal, anomalous} = anomalous otherwise normal s M f M s , , ( , ) Nonself Self False positives False negatives M U
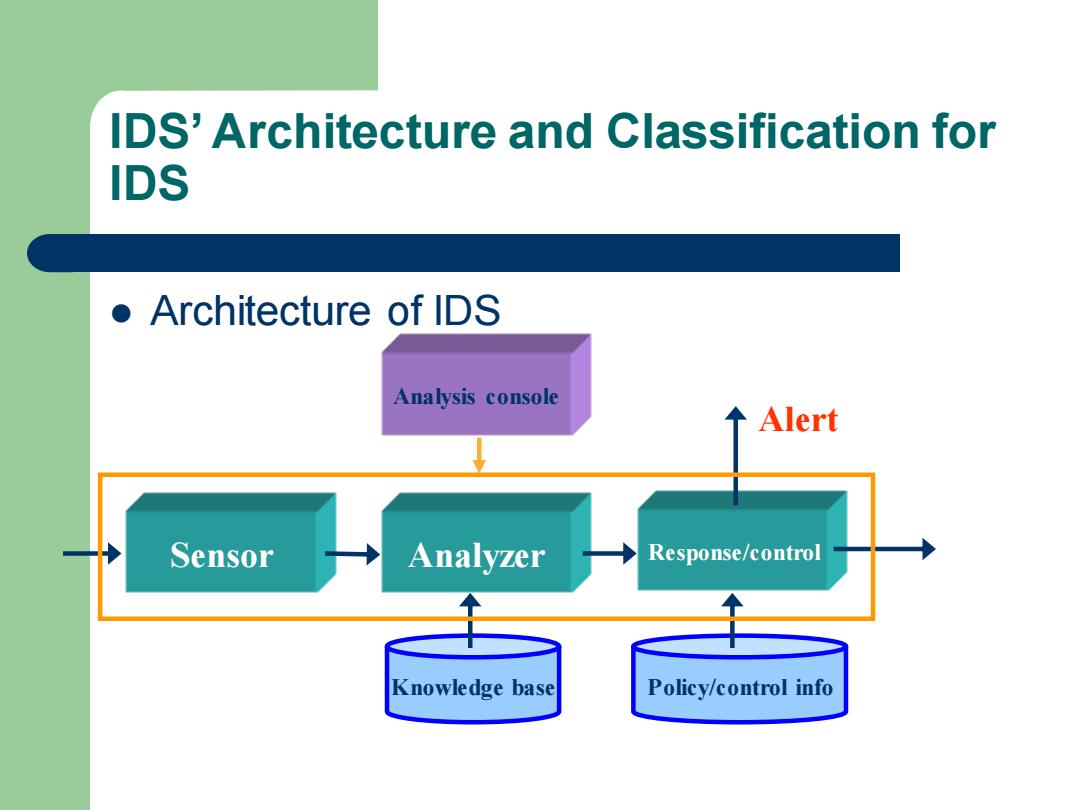
IDS'Architecture and Classification for IDS ●Architecture of IDS Analysis console 个 Alert Sensor Analyzer Response/control Knowledge base Policy/control info
IDS’ Architecture and Classification for IDS ⚫ Architecture of IDS Sensor Analyzer Knowledge base Response/control Policy/control info Alert Analysis console