
In cryptography,differential privacy aims to provide means to maximize the accuracy of queries from statistical databases while minimizing the chances of identifying its records. ----Source from wikipedia
In cryptography, differential privacy aims to provide means to maximize the accuracy of queries from statistical databases while minimizing the chances of identifying its records. ----Source from wikipedia

Outline 1.Context 2.The Mechanisms of Privacy Preserving 3.Applications under Differential Privacy 4.Our Current Research Works
Outline 1. Context 2. The Mechanisms of Privacy Preserving 3. Applications under Differential Privacy 4. Our Current Research Works
P 1.Context
1.Context
Context The information Technology and applications are developing rapidly in this era. √Mobile Internet √Cloud computing VInternet of Things(or Everything) √Electronic Commerce √Electronic Payment Society Network Service(SNS) Location-Based Service These technologies and applications Produce Big Data
Context The information Technology and applications are developing rapidly in this era. Mobile Internet Cloud computing Internet of Things(or Everything) Electronic Commerce Electronic Payment Society Network Service(SNS) Location-Based Service ………. These technologies and applications Produce Big Data
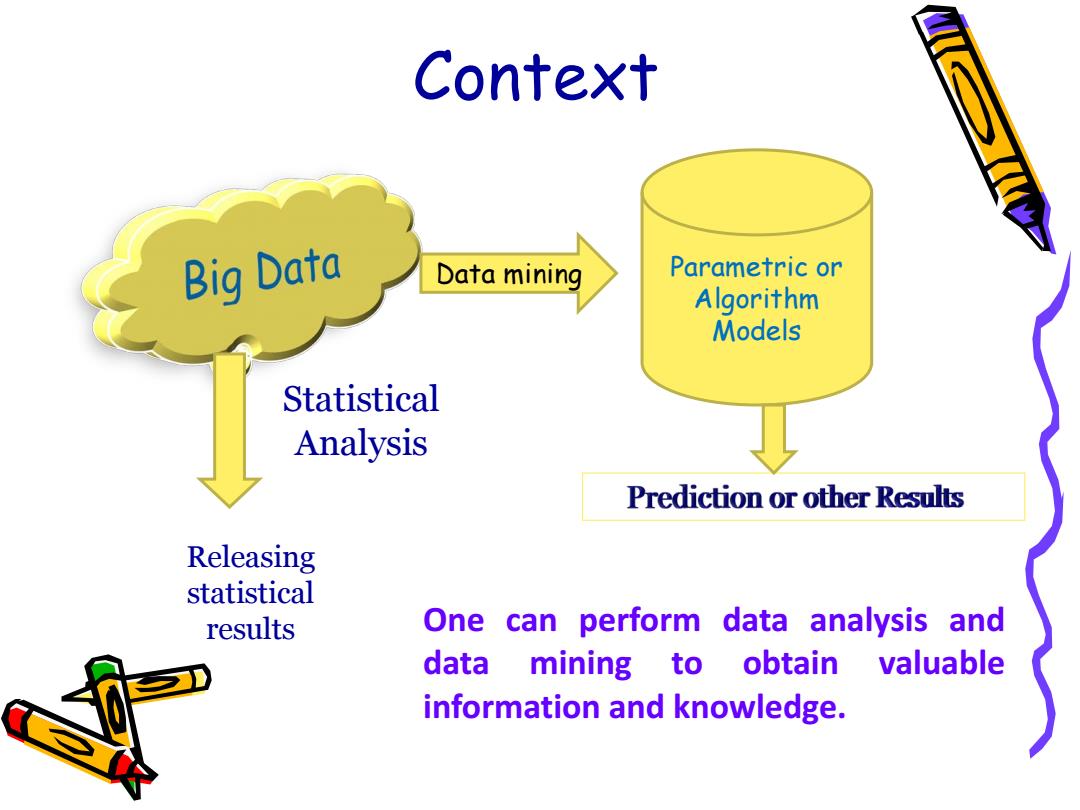
Context Big Data Data mining Parametric or Algorithm Models Statistical Analysis Prediction or other Results Releasing statistical results One can perform data analysis and data mining to obtain valuable information and knowledge
Context Parametric or Algorithm Models Data mining Statistical Analysis Releasing statistical results One can perform data analysis and data mining to obtain valuable information and knowledge

Context However,the disclosure of individual privacy and sensitive information is challenging when performing data release,data analysis or data mining
Context However, the disclosure of individual privacy and sensitive information is challenging when performing data release, data analysis or data mining
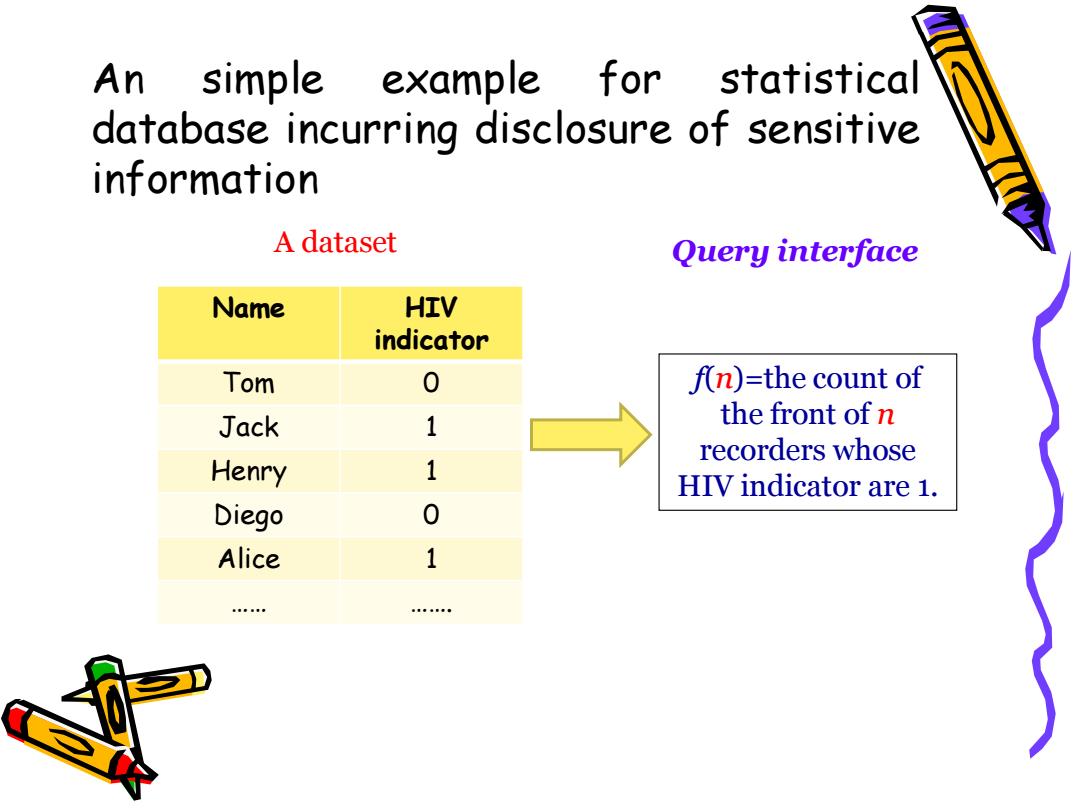
An simple example for statistical database incurring disclosure of sensitive information A dataset Query interface Name HIV indicator Tom f(n)=the count of Jack 1 the front of n recorders whose Henry 1 HIV indicator are 1. Diego Alice 1
Name HIV indicator Tom 0 Jack 1 Henry 1 Diego 0 Alice 1 …… ……. A dataset f(n)=the count of the front of n recorders whose HIV indicator are 1. Query interface An simple example for statistical database incurring disclosure of sensitive information
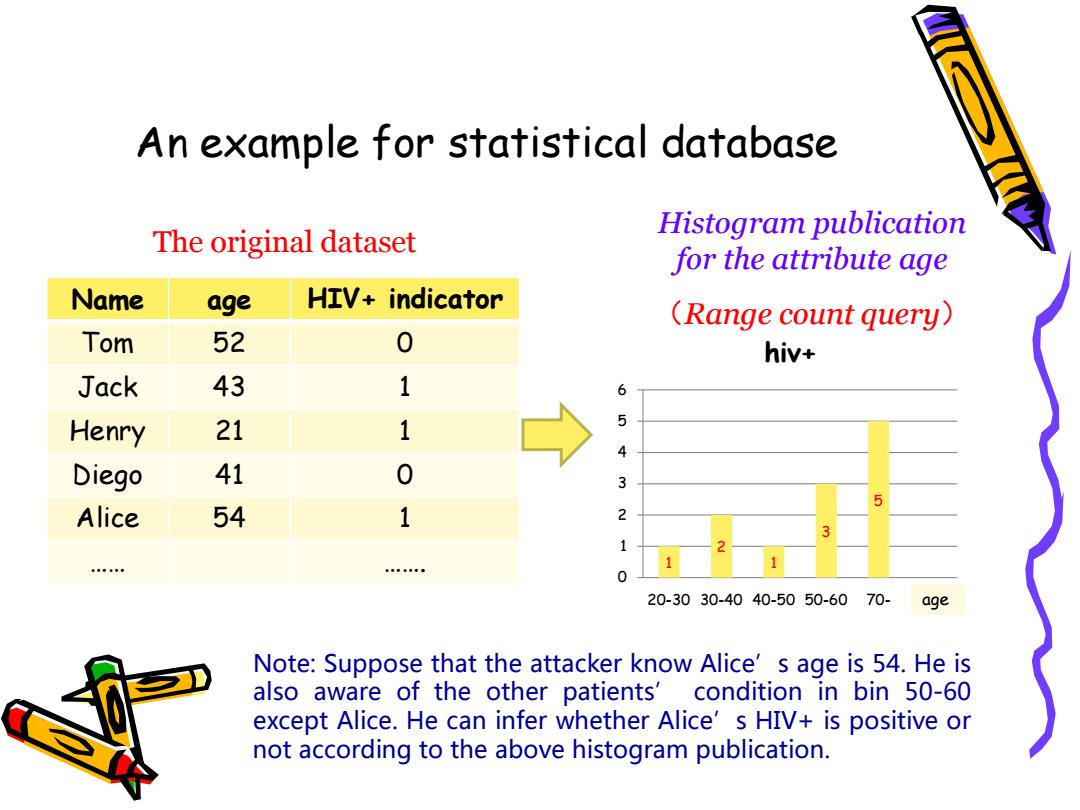
An example for statistical database The original dataset Histogram publication for the attribute age Name age HIV+indicator (Range count query) Tom 52 hiv+ Jack 43 1 6 Henry 21 1 5 Diego 41 3 5 Alice 54 1 2 3 贵第电 20-3030-4040-5050-6070- age Note:Suppose that the attacker know Alice's age is 54.He is also aware of the other patients'condition in bin 50-60 except Alice.He can infer whether Alice's HIV+is positive or not according to the above histogram publication
An example for statistical database Name age HIV+ indicator Tom 52 0 Jack 43 1 Henry 21 1 Diego 41 0 Alice 54 1 …… ……. The original dataset Histogram publication for the attribute age (Range count query) 1 2 1 3 5 0 1 2 3 4 5 6 20-30 30-40 40-50 50-60 70- hiv+ age Note: Suppose that the attacker know Alice’s age is 54. He is also aware of the other patients’ condition in bin 50-60 except Alice. He can infer whether Alice’s HIV+ is positive or not according to the above histogram publication
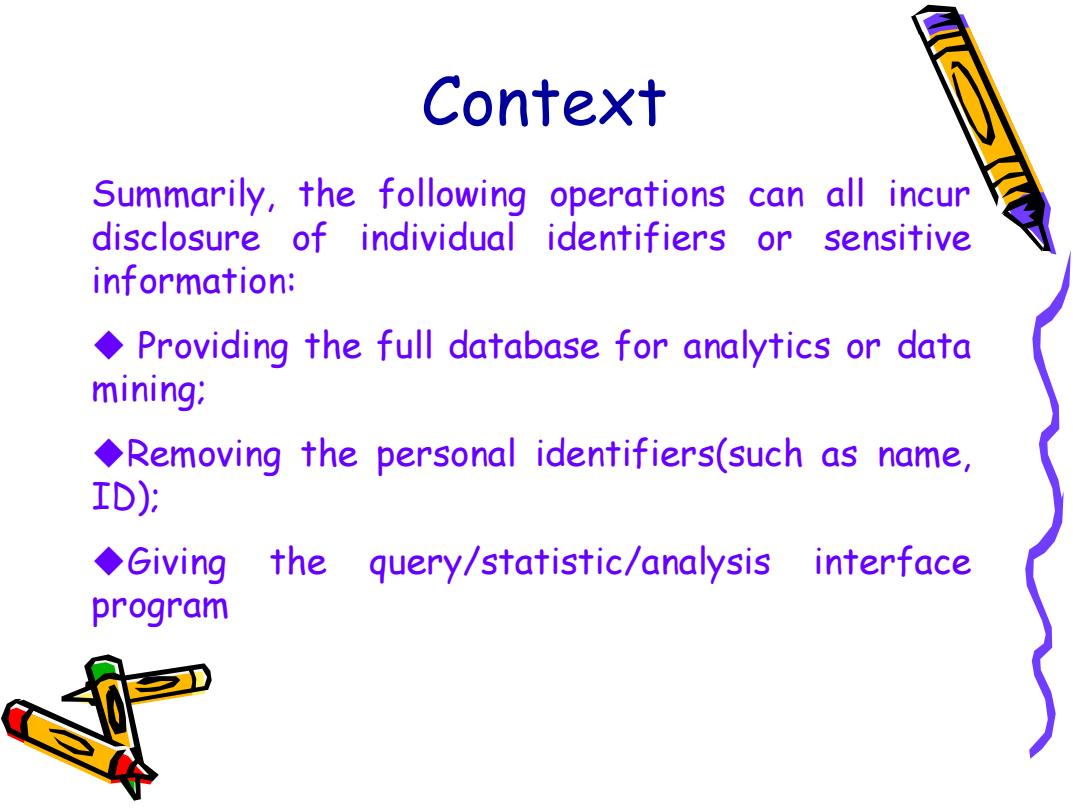
Context Summarily,the following operations s can all incur disclosure of individual identifiers or sensitive information: Providing the full database for analytics or data mining; Removing the personal identifiers(such as name, ID); ◆Giving the query/statistic/analysis interface program
Context Summarily, the following operations can all incur disclosure of individual identifiers or sensitive information: Providing the full database for analytics or data mining; Removing the personal identifiers(such as name, ID); Giving the query/statistic/analysis interface program

Context The events of disclosure of sensitive information: Patient specific data of 135,000 state employees and their families published by the Group insurance Commission (GIC)in Massachusetts; Anonymity Ethnicity Name Visit date Address ZIP Note:Latanya Diagnosis Date Birth Sweeney Broke this registered anonymized data and Procedure date found William Weld, Party the governor of Medication Sex affiliation Massachusetts at that time. Total charge Date last voted Medical Data Voter List
Context The events of disclosure of sensitive information: Patient specific data of 135,000 state employees and their families published by the Group insurance Commission (GIC) in Massachusetts; Note: Latanya Sweeney Broke this anonymized data and found William Weld, the governor of Massachusetts at that time. Anonymity