
On the Safety of loT Device Physical Interaction Control 成员:闫坤、陈晨洋、李秉坤
成员:闫坤、陈晨洋、李秉坤 On the Safety of IoT Device Physical Interaction Control

Outline 1.Research Background >2.System Implementation >3.Experiment and Results >4.Sum and Prospect 1
Outline ➢ 1. Research Background ➢ 2. System Implementation ➢ 3. Experiment and Results ➢ 4. Sum and Prospect 1

Research Background Existing research focuses on solving traditional problems in the Internet of Things environment 1.Device firmware error 2.Communication protocol vulnerability 3.Malware attack 4.System design flaws 2
Research Background Existing research focuses on solving traditional problems in the Internet of Things environment : 1. Device firmware error 2. Communication protocol vulnerability 3. Malware attack 4. System design flaws 2
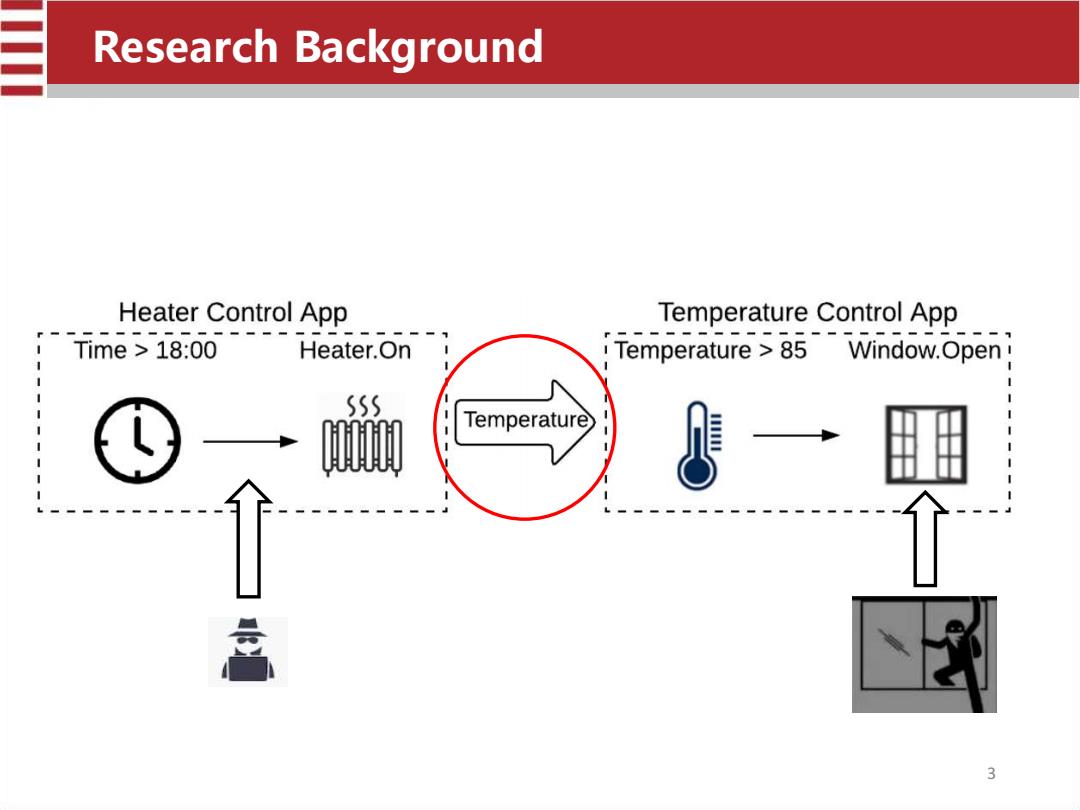
Research Background Heater Control App Temperature Control App Time>18:00 Heater.On Temperature >85 Window.Open 1 555 Temperature 3
Research Background 3

Research Background loTMon:Research loT devices interacting with the surrounding environment through physical channels 1.Discover any possible physical interactions between loT devices 2.Generate all potential interaction chains between applications in the loT environment 3.Assess the security risks of the interaction chain between each discovered application based on physical impact 4
Research Background IoTMon: Research IoT devices interacting with the surrounding environment through physical channels 1. Discover any possible physical interactions between IoT devices 2. Generate all potential interaction chains between applications in the IoT environment 3. Assess the security risks of the interaction chain between each discovered application based on physical impact 4

System Implementation Application Analysis Interaction Chain Discovery Risk Analysis Mitigation Chains Code Intra-app Intra-app Behavior Modeling Analysis Interactions Clustering Inter-app Applications Interaction Chain Generation Risk Evaluation Physical Physical Description Channel Identification Channels Risk Mitigation
System Implementation 5
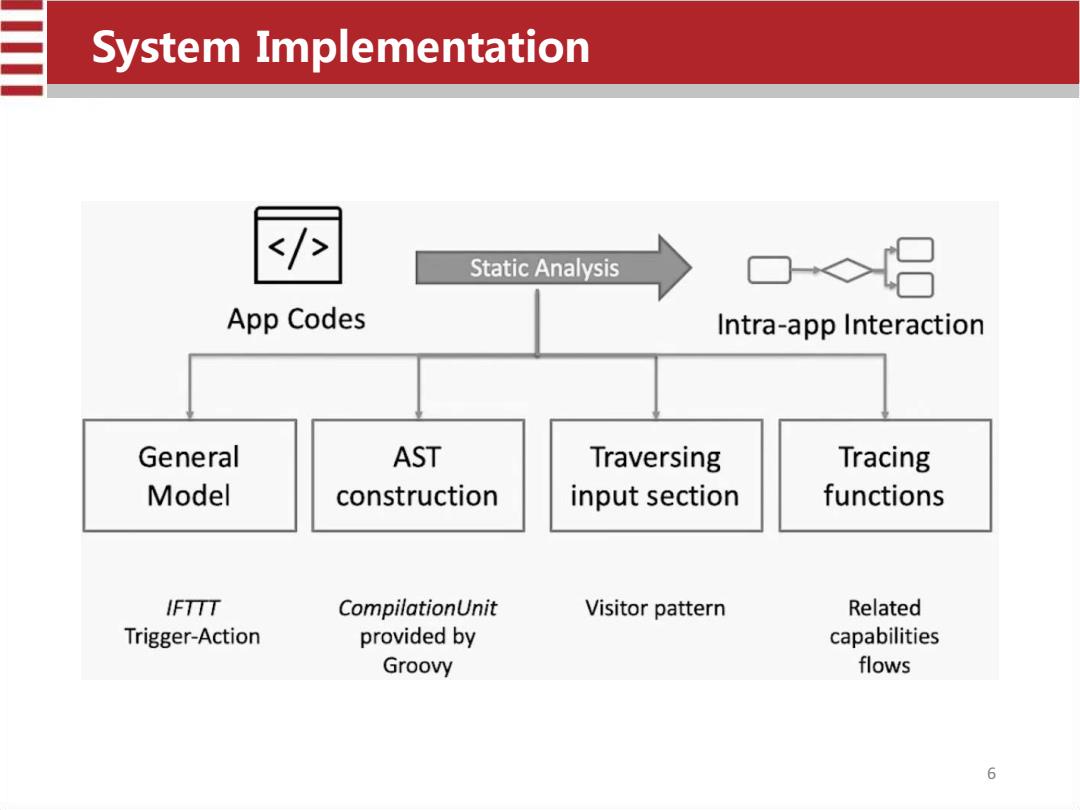
System Implementation Static Analysis 口◇ App Codes Intra-app Interaction General AST Traversing Tracing Model construction input section functions IFTTT CompilationUnit Visitor pattern Related Trigger-Action provided by capabilities Groovy flows 6
System Implementation 6

System Implementation def presence(evt): if (evt.value ="present"): "Lock it when I leave” if(unlook ="Yes"): def anyLocked lock1.count(it.current ="unlooked")!=Look1.size() if(anyLooked): sendMessage("Doors unlocked at arrivel of Sevt.LinkText") lock1.lock() lock1.unlock(delay:10) switch1.on(delay:1000) Triggers present Actions Locks Switches lock Unlock On 7
System Implementation def presence(evt): if (evt.value == "present"): if(unlook == "Yes"): def anyLocked = lock1.count(it.current == "unlooked") != look1.size() if(anyLooked): sendMessage("Doors unlocked at arrivel of Sevt.linkText") lock1.lock() lock1.unlock(delay:10) switch1.on(delay:1000) “Lock it when I leave” Triggers present Locks Switches lock Unlock On Actions 7
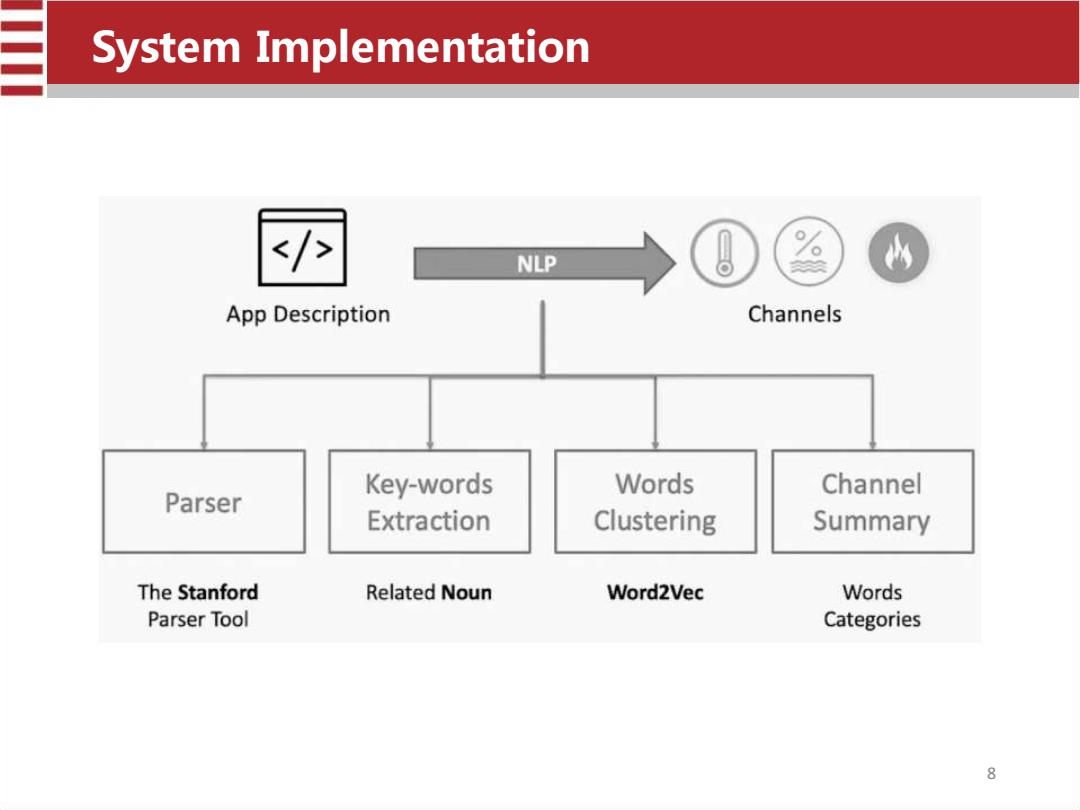
System Implementation 7 NLP App Description Channels Key-words Words Channel Parser Extraction Clustering Summary The Stanford Related Noun Word2Vec Words Parser Tool Categories 8
System Implementation 8
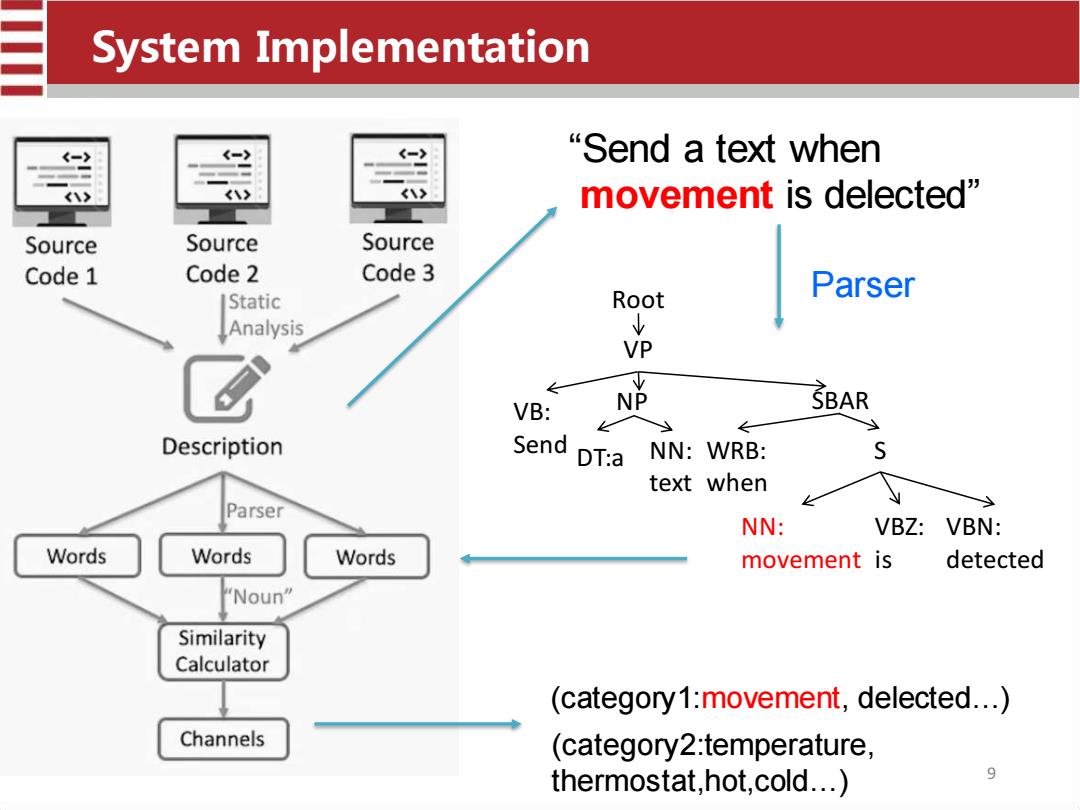
System Implementation “Send a text when movement is delected" Source Source Source Code 1 Code 2 Code 3 Root Parser Static Analysis VP V VB: NP SBAR Description Send DT:a NN:WRB: s text when Parser NN: VBZ:VBN: Words Words Words movement is detected "Noun" Similarity Calculator (category1:movement,delected...) Channels (category2:temperature, thermostat,hot,cold...) 9
“Send a text when movement is delected” NP VP VB: Send Root SBAR DT:a NN: text WRB: when S NN: movement VBZ: is VBN: detected Parser (category1:movement, delected…) (category2:temperature, thermostat,hot,cold…) System Implementation 9