
Web Security -Part 1:Cookies Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Web Security – Part 1: Cookies Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Web Applications Big trend:software as a(Web-based)service -Online banking,shopping,government,bill payment,tax prep,customer relationship management,etc. -Cloud computing Applications hosted on Web servers -Written in a mixture of PHP,Java,Perl,Python,C,ASP Security is rarely the main concern -Poorly written scripts with inadequate input validation -Sensitive data stored in world-readable files -Recent push from Visa and Mastercard to improve security of data management(PCI-Payment Card Industry standard) 2
2 Web Applications Big trend: software as a (Web-based) service ─ Online banking, shopping, government, bill payment, tax prep, customer relationship management, etc. ─ Cloud computing Applications hosted on Web servers ─ Written in a mixture of PHP, Java, Perl, Python, C, ASP Security is rarely the main concern ─ Poorly written scripts with inadequate input validation ─ Sensitive data stored in world-readable files ─ Recent push from Visa and Mastercard to improve security of data management (PCI – Payment Card Industry standard)
Typical Web application Design Runs on a Web server or application server Takes input from Web users(via Web server) Interacts with back-end databases and third parties Prepares and outputs results for users(via Web server) Dynamically generated HTML pages 一 Contain content from many different sources,often including regular users -Blogs,social networks,photo-sharing websites... 3
3 Typical Web Application Design Runs on a Web server or application server Takes input from Web users (via Web server) Interacts with back-end databases and third parties Prepares and outputs results for users (via Web server) Dynamically generated HTML pages ─ Contain content from many different sources, often including regular users ─ Blogs, social networks, photo-sharing websites…

Dangerous Websites Recent "Web patrol"study at Microsoft identified 752 unique URLs that could successfully exploit unpatched Windows XP machines -Many are interlinked by redirection and controlled by the same major players "“But I never visit risky websites'” -11 exploit pages are among top 10,000 most visited -Trick:put up a page with popular content,get into search engines,page redirects to the exploit site 4
4 Dangerous Websites Recent “Web patrol” study at Microsoft identified 752 unique URLs that could successfully exploit unpatched Windows XP machines ─ Many are interlinked by redirection and controlled by the same major players “But I never visit risky websites” ─ 11 exploit pages are among top 10,000 most visited ─ Trick: put up a page with popular content, get into search engines, page redirects to the exploit site

HTTP and Cookies HTTP (Hypertext Transfer Protocol)is a stateless request/response protocol -Each request is independent of previous requests Advantage being stateless:servers do not need to retain information about users between requests. HTTP is stateless.Web applications are often stateful. -So the Client has to remember things that the Server needs to know. Cookie is a common way for maintaining states. -A cookie is a piece of information that contains the state(or session ID)of a client.A cookie consists of one or more name-value pairs. Server:uses Set-Cookie parameters to ask client's browser to store a cookie. Client:stores the cookie and sends the unchanged cookie in EVERY request to the same server. 5
5 HTTP and Cookies HTTP (Hypertext Transfer Protocol) is a stateless request/response protocol ─ Each request is independent of previous requests Advantage being stateless: servers do not need to retain information about users between requests. HTTP is stateless. Web applications are often stateful. ─ So the Client has to remember things that the Server needs to know. Cookie is a common way for maintaining states. ─ A cookie is a piece of information that contains the state (or session ID) of a client. A cookie consists of one or more name-value pairs. Server: uses Set-Cookie parameters to ask client’s browser to store a cookie. Client: stores the cookie and sends the unchanged cookie in EVERY request to the same server
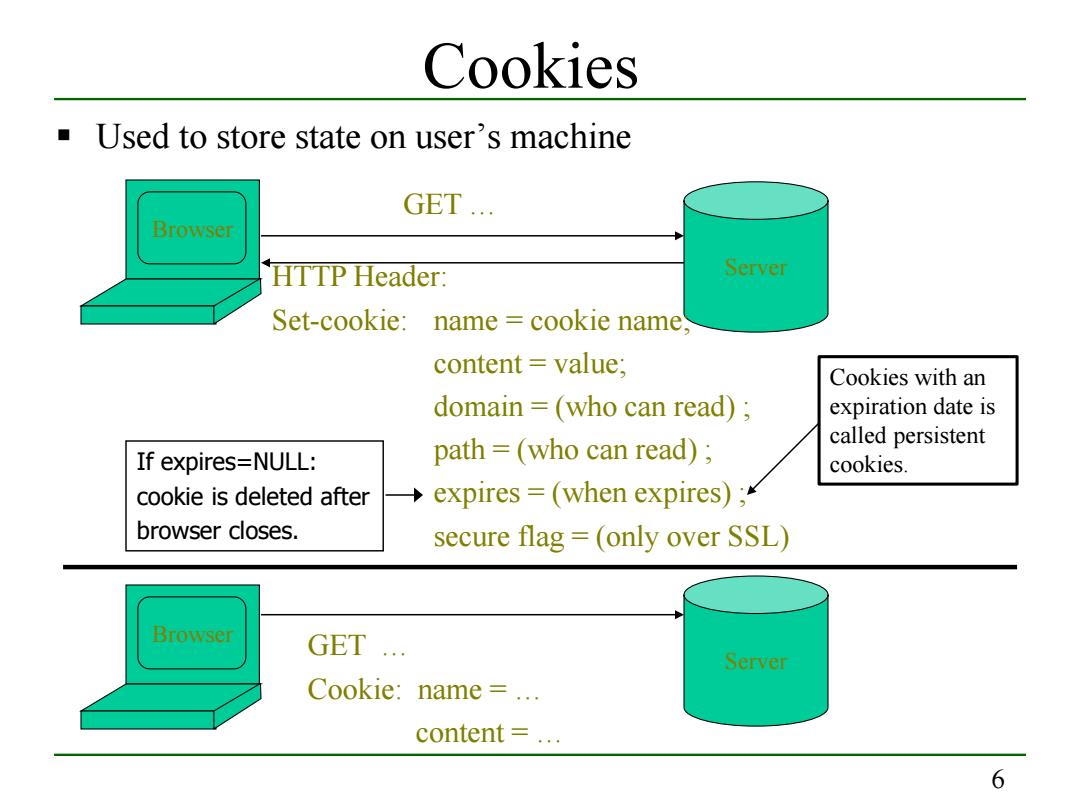
Cookies Used to store state on user's machine GET... Browser HTTP Header: Server Set-cookie: name cookie name, content=value; Cookies with an domain =(who can read); expiration date is called persistent If expires=NULL: path =(who can read); cookies. cookie is deleted after expires =(when expires); browser closes. secure flag=(only over SSL) Browser GET Server Cookie:name =.. content 6
6 Cookies Used to store state on user’s machine Browser Server GET … HTTP Header: Set-cookie: name = cookie name; content = value; domain = (who can read) ; path = (who can read) ; expires = (when expires) ; secure flag = (only over SSL) Browser Server GET … Cookie: name = … content = … If expires=NULL: cookie is deleted after browser closes. Cookies with an expiration date is called persistent cookies
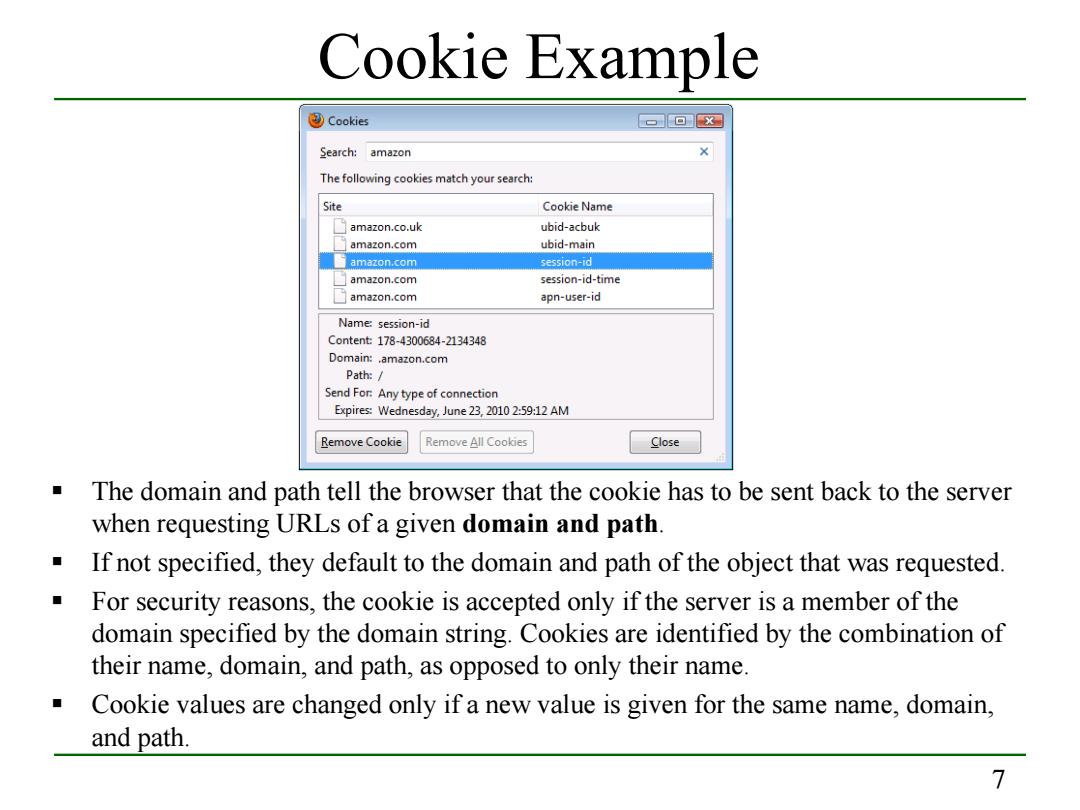
Cookie Example ③Cookies -回x✉ Search:amazon The following cookies match your search: Site Cookie Name amazon.co.uk ubid-acbuk amazon.com ubid-main amazon.com session-id amazon.com session-id-time amazon.com apn-user-id Name:session-id Content:178-4300684-2134348 Domain:.amazon.com Path:/ Send For:Any type of connection Expires:Wednesday,June 23,2010 2:59:12 AM Remove Cookie Remove All Cookies Close The domain and path tell the browser that the cookie has to be sent back to the server when requesting URLs of a given domain and path. If not specified,they default to the domain and path of the object that was requested. For security reasons,the cookie is accepted only if the server is a member of the domain specified by the domain string.Cookies are identified by the combination of their name,domain,and path,as opposed to only their name. Cookie values are changed only if a new value is given for the same name,domain, and path. 7
7 Cookie Example The domain and path tell the browser that the cookie has to be sent back to the server when requesting URLs of a given domain and path. If not specified, they default to the domain and path of the object that was requested. For security reasons, the cookie is accepted only if the server is a member of the domain specified by the domain string. Cookies are identified by the combination of their name, domain, and path, as opposed to only their name. Cookie values are changed only if a new value is given for the same name, domain, and path

Cookie Uses:Session Management Session Management:stores user related data across multiple accesses. Originally,web developers put shopping cart content directly in a cookie. This may make the cookie too big:cookies are intended to be used only for infrequent storage of a small amount of data on the user's machine. Cookie limitations depend on browsers.But the following limits generally apply: -300 cookies total. -20 cookies per server(not per page or site)>So,web developers should try to combine name-value pairs into one cookie. -4K data per cookie(including everything) Nowadays,web developers typically store the shopping cart contents in a database on the server,and stores the unique session ID in the cookie. 8
8 Cookie Uses: Session Management Session Management: stores user related data across multiple accesses. Originally, web developers put shopping cart content directly in a cookie. This may make the cookie too big: cookies are intended to be used only for infrequent storage of a small amount of data on the user’s machine. Cookie limitations depend on browsers. But the following limits generally apply: ─ 300 cookies total. ─ 20 cookies per server (not per page or site) So, web developers should try to combine name-value pairs into one cookie. ─ 4K data per cookie (including everything). Nowadays, web developers typically store the shopping cart contents in a database on the server, and stores the unique session ID in the cookie

Cookie Uses:Authentication and Personalization Authentication:enable users to log in once but request multiple pages -Allowing users to log in to a website is a frequent use of cookies.Typically the web server will first send a cookie containing a unique session identifier.Users then submit their credentials and the web application authenticates the session and allows the user access to services. Personalization:Cookies may be used to remember the information about the user who has visited a website in order to show relevant content in the future. Many websites use cookies for personalization based on users'preferences.Users select their preferences by entering them in a web form and submitting the form to the server.The server encodes the preferences in a cookie and sends the cookie back to the browser.This way,every time the user accesses a page,the browser sends to the server the cookie where the preferences are stored,and then the server personalizes the page according to the user preferences. For example,the Wikipedia website allows authenticated users to choose the webpage skin they like best;the Google search engine allows users(even non-registered ones)to decide how many search results per page they want to see. 9
9 Cookie Uses: Authentication and Personalization Authentication: enable users to log in once but request multiple pages ─ Allowing users to log in to a website is a frequent use of cookies. Typically the web server will first send a cookie containing a unique session identifier. Users then submit their credentials and the web application authenticates the session and allows the user access to services. Personalization: Cookies may be used to remember the information about the user who has visited a website in order to show relevant content in the future. ─ Many websites use cookies for personalization based on users' preferences. Users select their preferences by entering them in a web form and submitting the form to the server. The server encodes the preferences in a cookie and sends the cookie back to the browser. This way, every time the user accesses a page, the browser sends to the server the cookie where the preferences are stored, and then the server personalizes the page according to the user preferences. ─ For example, the Wikipedia website allows authenticated users to choose the webpage skin they like best; the Google search engine allows users (even non-registered ones) to decide how many search results per page they want to see
Cookie Uses:Tracking within One Site 1.If the user requests a page of the site,but the request contains no cookie,the server presumes that this is the first page visited by the user;the server creates a cookie back to the browser together with the requested page; 2.From this point on,the cookie will be automatically sent by the browser to the server every time a new page from the site is requested;the server sends the page as usual,but also stores the URL of the requested page,the date/time of the request,and the cookie in a log file. 3.By looking at the log file,it is then possible to find out which pages the user has visited and in what sequence.For example,if the log contains some requests done using the cookie id=abc,it can be determined that these requests all come from the same user.The URL and date/time stored with the cookie allows for finding out which pages the user has visited,and at what time 10
10 Cookie Uses: Tracking within One Site 1. If the user requests a page of the site, but the request contains no cookie, the server presumes that this is the first page visited by the user; the server creates a cookie back to the browser together with the requested page; 2. From this point on, the cookie will be automatically sent by the browser to the server every time a new page from the site is requested; the server sends the page as usual, but also stores the URL of the requested page, the date/time of the request, and the cookie in a log file. 3. By looking at the log file, it is then possible to find out which pages the user has visited and in what sequence. For example, if the log contains some requests done using the cookie id=abc, it can be determined that these requests all come from the same user. The URL and date/time stored with the cookie allows for finding out which pages the user has visited, and at what time