
Cryptography and Network Security Fourth Edition Principles and Practices William Stallings
NEXT◆ Cryptography Cryptography and Network Security Principles and Practices,Fourth Edition and Networl Securitv By William Stallings Publisher:Prentice Hall Pub Date:November 16,2005 Print1sBN-10:0-13-187316-4 Print1sBN-13:978-0-13-187316-2 eText ISBN.-10:0-13-187319-9 ·Table of Contents eText1SBN-13:978-0-13-187319-3 ·Index Pages:592 In this age of viruses and hackers,of electronic eavesdropping and electronic fraud,security is paramount. As the disciplines of cryptography and network security have matured,more practical,readily available applications to enforce network security have developed.This text provides a practical survey of both the principles and practice of cryptography and network security.First,the basic issues to be addressed by a network security capability are explored through a tutorial and survey of cryptography and network security technology.Then,the practice of network security is explored via practical applications that have been implemented and are in use today NEXT◆
• Table of Contents • Index Cryptography and Network Security Principles and Practices, Fourth Edition By William Stallings Publisher: Prentice Hall Pub Date: November 16, 2005 Print ISBN-10: 0-13-187316-4 Print ISBN-13: 978-0-13-187316-2 eText ISBN-10: 0-13-187319-9 eText ISBN-13: 978-0-13-187319-3 Pages: 592 In this age of viruses and hackers, of electronic eavesdropping and electronic fraud, security is paramount. As the disciplines of cryptography and network security have matured, more practical, readily available applications to enforce network security have developed. This text provides a practical survey of both the principles and practice of cryptography and network security. First, the basic issues to be addressed by a network security capability are explored through a tutorial and survey of cryptography and network security technology. Then, the practice of network security is explored via practical applications that have been implemented and are in use today

◆PREY NEXT◆ Cryptography and Network Security Principles and Practices,Fourth Edition By William Stallings Publisher:Prentice Hall Pub Date:November 16,2005 Print1SBN-10:0-13-187316-4 Print1SBN-13:978-0-13-187316-2 eText ISBN.-10:0-13-187319-9 ·Table of Contents eText1SBN-13:978-0-13-187319-3 ·Index Pages:592 Copyright Notation Preface Objectives Intended Audience Plan of the Book Internet Services for Instructors and Students Projects for Teaching Cryptography and Network Security What's New in the Fourth Edition Acknowledgments Chapter 0.Reader's Guide Section 0.1.Outline of this Book Section 0.2.Roadmap Section 0.3.Internet and Web Resources Chapter 1.Introduction 122469 Section 1.1.Security Trends Section 1.2.The OSI Security Architecture Section 1.3.Security Attacks Section 1.4.Security Services Section 1.5.Security Mechanisms Section 1.6.A Model for Network Security Section 1.7.Recommended Reading and Web Sites Section 1.8.Key Terms.Review Questions,and Problems Part One:Symmetric Ciphers Chapter 2.Classical Encryption Techniques Section 2.1.Symmetric Cipher Model Section 2.2.Substitution Techniques Section 2.3.Transposition Techniques Section 2.4.Rotor Machines Section 2.5.Steganography 236924503059135624 Section 2.6.Recommended Reading and Web Sites Section 2.7.Key Terms.Review Questions,and Problems Chapter 3.Block Ciphers and the Data Encryption Standard Section 3.1.Block Cipher Principles
• Table of Contents • Index Cryptography and Network Security Principles and Practices, Fourth Edition By William Stallings Publisher: Prentice Hall Pub Date: November 16, 2005 Print ISBN-10: 0-13-187316-4 Print ISBN-13: 978-0-13-187316-2 eText ISBN-10: 0-13-187319-9 eText ISBN-13: 978-0-13-187319-3 Pages: 592 Copyright Notation xi Preface xiii Objectives xiii Intended Audience xiii Plan of the Book xiv Internet Services for Instructors and Students xiv Projects for Teaching Cryptography and Network Security xiv What's New in the Fourth Edition xv Acknowledgments xvi Chapter 0. Reader's Guide 1 Section 0.1. Outline of this Book 2 Section 0.2. Roadmap 2 Section 0.3. Internet and Web Resources 4 Chapter 1. Introduction 6 Section 1.1. Security Trends 9 Section 1.2. The OSI Security Architecture 12 Section 1.3. Security Attacks 13 Section 1.4. Security Services 16 Section 1.5. Security Mechanisms 19 Section 1.6. A Model for Network Security 22 Section 1.7. Recommended Reading and Web Sites 24 Section 1.8. Key Terms, Review Questions, and Problems 25 Part One: Symmetric Ciphers 26 Chapter 2. Classical Encryption Techniques 28 Section 2.1. Symmetric Cipher Model 30 Section 2.2. Substitution Techniques 35 Section 2.3. Transposition Techniques 49 Section 2.4. Rotor Machines 51 Section 2.5. Steganography 53 Section 2.6. Recommended Reading and Web Sites 55 Section 2.7. Key Terms, Review Questions, and Problems 56 Chapter 3. Block Ciphers and the Data Encryption Standard 62 Section 3.1. Block Cipher Principles 64

Section 3.2.The Data Encryption Standard Section 3.3.The Strength of Des Section 3.4.Differential and Linear Cryptanalysis Section 3.5.Block Cipher Design Principles Section 3.6.Recommended Reading Section 3.7.Key Terms.Review Questions,and Problems Chapter 4.Finite Fields 22360057 Section 4.1.Groups,Rings.and Fields Section 4.2.Modular Arithmetic 101 Section 4.3.The Euclidean Algorithm 107 Section 4.4.Finite Fields of The Form GF(p 109 Section 4.5.Polynomial Arithmetic Section 4.6.Finite Fields Of the Form GF(2n) Section 4.7.Recommended Reading and Web Sites Section 4.8.Key Terms.Review Questions,and Problems Chapter 5.Advanced Encryption Standard Section 5.1.Evaluation Criteria For AES Section 5.2.The AES Cipher Section 5.3.Recommended Reading and Web Sites Section 5.4.Key Terms.Review Questions,and Problems 1920丝50066场 Appendix 5A Polynomials with Coefficients in GF(28) Appendix 5B Simplified AES Chapter 6.More on Symmetric Ciphers Section 6.1.Multiple Encryption and Triple DES Section 6.2.Block Cipher Modes of Operation Section 6.3.Stream Ciphers and RC4 189 Section 6.4.Recommended Reading and Web Site Section 6.5.Key Terms.Review Questions,and Problems Chapter 7.Confidentiality Using Symmetric Encryption Section 7.1.Placement of Encryption Function Section 7.2.Traffic Confidentiality MM0000 Section 7.3.Key Distribution Section 7.4.Random Number Generation Section 7.5.Recommended Reading and Web Sites Section 7.6.Key Terms.Review Questions,and Problems Part Two:Public-Key Encryption and Hash Functions Chapter 8.Introduction to Number Theory Section 8.1.Prime Numbers Section 8.2.Fermat's and Euler's Theorems Section 8.3.Testing for Primality Section 8.4.The Chinese Remainder Theorem Section 8.5.Discrete Logarithms Section 8.6.Recommended Reading and Web Sites 147228408142448459 Section 8.7.Key Terms.Review Questions,and Problems Chapter 9.Public-Key Cryptography and RSA Section 9.1.Principles of Public-Key Cryptosystems Section 9.2.The RSA Algorithm Section 9.3.Recommended Reading and Web Sites 塑 Section 9.4.Key Terms.Review Questions.and Problems 4 Appendix 9A Proof of the RSA Algorithm 285
Section 3.2. The Data Encryption Standard 72 Section 3.3. The Strength of Des 82 Section 3.4. Differential and Linear Cryptanalysis 83 Section 3.5. Block Cipher Design Principles 86 Section 3.6. Recommended Reading 90 Section 3.7. Key Terms, Review Questions, and Problems 90 Chapter 4. Finite Fields 95 Section 4.1. Groups, Rings, and Fields 97 Section 4.2. Modular Arithmetic 101 Section 4.3. The Euclidean Algorithm 107 Section 4.4. Finite Fields of The Form GF(p) 109 Section 4.5. Polynomial Arithmetic 113 Section 4.6. Finite Fields Of the Form GF(2n) 119 Section 4.7. Recommended Reading and Web Sites 129 Section 4.8. Key Terms, Review Questions, and Problems 130 Chapter 5. Advanced Encryption Standard 134 Section 5.1. Evaluation Criteria For AES 135 Section 5.2. The AES Cipher 140 Section 5.3. Recommended Reading and Web Sites 160 Section 5.4. Key Terms, Review Questions, and Problems 161 Appendix 5A Polynomials with Coefficients in GF(28) 163 Appendix 5B Simplified AES 165 Chapter 6. More on Symmetric Ciphers 174 Section 6.1. Multiple Encryption and Triple DES 175 Section 6.2. Block Cipher Modes of Operation 181 Section 6.3. Stream Ciphers and RC4 189 Section 6.4. Recommended Reading and Web Site 194 Section 6.5. Key Terms, Review Questions, and Problems 194 Chapter 7. Confidentiality Using Symmetric Encryption 199 Section 7.1. Placement of Encryption Function 201 Section 7.2. Traffic Confidentiality 209 Section 7.3. Key Distribution 210 Section 7.4. Random Number Generation 218 Section 7.5. Recommended Reading and Web Sites 227 Section 7.6. Key Terms, Review Questions, and Problems 228 Part Two: Public-Key Encryption and Hash Functions 232 Chapter 8. Introduction to Number Theory 234 Section 8.1. Prime Numbers 236 Section 8.2. Fermat's and Euler's Theorems 238 Section 8.3. Testing for Primality 242 Section 8.4. The Chinese Remainder Theorem 245 Section 8.5. Discrete Logarithms 247 Section 8.6. Recommended Reading and Web Sites 253 Section 8.7. Key Terms, Review Questions, and Problems 254 Chapter 9. Public-Key Cryptography and RSA 257 Section 9.1. Principles of Public-Key Cryptosystems 259 Section 9.2. The RSA Algorithm 268 Section 9.3. Recommended Reading and Web Sites 280 Section 9.4. Key Terms, Review Questions, and Problems 281 Appendix 9A Proof of the RSA Algorithm 285

Appendix 9B The Complexity of Algorithms Chapter 10.Key Management;Other Public-Key Cryptosystems Section 10.1.Key Management 塑塑 Section 10.2.Diffie-Hellman Key Exchange 298 Section 10.3.Elliptic Curve Arithmetio Section 10.4.Elliptic Curve Cryptography Section 10.5.Recommended Reading and Web Sites Section 10.6.Key Terms.Review Questions,and Problems 0004 Chapter 11.Message Authentication and Hash Functions Section 11.1.Authentication Requirements Section 11.2.Authentication Functions Section 11.3.Message Authentication Codes Section 11.4.Hash Functions Section 11.5.Security of Hash Functions and Macs Section 11.6.Recommended Reading Section 11.7.Key Terms.Review Questions.and Problems Appendix 11A Mathematical Basis of the Birthday Attack Chapter 12.Hash and MAC Algorithms Section 12.1.Secure Hash Algorithm Section 12.2.Whirlpool Section 12.3.HMAC Section 12.4.CMAC Section 12.5.Recommended Reading and Web Sites Section 12.6.Key Terms,Review Questions,and Problems Chapter 13.Digital Signatures and Authentication Protocols Section 13.1.Digital Signatures Section 13.2.Authentication Protocols Section 13.3.Digital Signature Standard Section 13.4.Recommended Reading and Web Sites Section 13.5.Key Terms.Review Questions,and Problems Part Three:Network Security Applications Chapter 14.Authentication Applications Section 14.1.Kerberos Section 14.2.X.509 Authentication Service Section 14.3.Public-Key Infrastructure Section 14.4.Recommended Reading and Web Sites Section 14.5.Key Terms,Review Questions,and Problems Appendix 14A Kerberos Encryption Techniques Chapter 15.Electronic Mail Security Section 15.1.Pretty Good Privacy Section 15.2.S/MIME Section 15.3.Key Terms,Review Questions,and Problems Appendix 15A Data Compression Using Zip Appendix 15B Radix-64 Conversion Appendix 15C PGP Random Number Generation 14第销销堡 Chapter 16.IP Security Section 16.1.IP Security Overview Section 16.2.IP Security Architecture Section 16.3.Authentication Header 493 Section 16.4.Encapsulating Security Payload 498
Appendix 9B The Complexity of Algorithms 286 Chapter 10. Key Management; Other Public-Key Cryptosystems 289 Section 10.1. Key Management 290 Section 10.2. Diffie-Hellman Key Exchange 298 Section 10.3. Elliptic Curve Arithmetic 301 Section 10.4. Elliptic Curve Cryptography 310 Section 10.5. Recommended Reading and Web Sites 313 Section 10.6. Key Terms, Review Questions, and Problems 314 Chapter 11. Message Authentication and Hash Functions 317 Section 11.1. Authentication Requirements 319 Section 11.2. Authentication Functions 320 Section 11.3. Message Authentication Codes 331 Section 11.4. Hash Functions 334 Section 11.5. Security of Hash Functions and Macs 340 Section 11.6. Recommended Reading 344 Section 11.7. Key Terms, Review Questions, and Problems 344 Appendix 11A Mathematical Basis of the Birthday Attack 346 Chapter 12. Hash and MAC Algorithms 351 Section 12.1. Secure Hash Algorithm 353 Section 12.2. Whirlpool 358 Section 12.3. HMAC 368 Section 12.4. CMAC 372 Section 12.5. Recommended Reading and Web Sites 374 Section 12.6. Key Terms, Review Questions, and Problems 374 Chapter 13. Digital Signatures and Authentication Protocols 377 Section 13.1. Digital Signatures 378 Section 13.2. Authentication Protocols 382 Section 13.3. Digital Signature Standard 390 Section 13.4. Recommended Reading and Web Sites 393 Section 13.5. Key Terms, Review Questions, and Problems 393 Part Three: Network Security Applications 398 Chapter 14. Authentication Applications 400 Section 14.1. Kerberos 401 Section 14.2. X.509 Authentication Service 419 Section 14.3. Public-Key Infrastructure 428 Section 14.4. Recommended Reading and Web Sites 430 Section 14.5. Key Terms, Review Questions, and Problems 431 Appendix 14A Kerberos Encryption Techniques 433 Chapter 15. Electronic Mail Security 436 Section 15.1. Pretty Good Privacy 438 Section 15.2. S/MIME 457 Section 15.3. Key Terms, Review Questions, and Problems 474 Appendix 15A Data Compression Using Zip 475 Appendix 15B Radix-64 Conversion 478 Appendix 15C PGP Random Number Generation 479 Chapter 16. IP Security 483 Section 16.1. IP Security Overview 485 Section 16.2. IP Security Architecture 487 Section 16.3. Authentication Header 493 Section 16.4. Encapsulating Security Payload 498

Section 16.5.Combining Security Associations 503 Section 16.6.Key Management Section 16.7.Recommended Reading and Web Site Section 16.8.Key Terms,Review Questions,and Problems 51亚 Appendix 16A Internetworking and Internet Protocols 8 Chapter 17.Web Security 52 Section 17.1.Web Security Considerations Section 17.2.Secure Socket Layer and Transport Layer Security Section 17.3.Secure Electronic Transaction 549 Section 17.4.Recommended Reading and Web Sites 560 Section 17.5.Key Terms,Review Questions,and Problems Part Four:System Security Chapter 18.Intruders Section 18.1.Intruders Section 18.2.Intrusion Detection Section 18.3.Password Management Section 18.4.Recommended Reading and Web Sites Section 18.5.Key Terms.Review Questions,and Problems Appendix 18A The Base-Rate Fallacy Chapter 19.Malicious Software Section 19.1.Viruses and Related Threats Section 19.2.Virus Countermeasures 第10 Section 19.3.Distributed Denial of Service Attacks Section 19.4.Recommended Reading and Web Sites Section 19.5.Key Terms,Review Questions,and Problems 102 Chapter 20.Firewalls Section 20.1.Firewall Design Principles Section 20.2.Trusted Systems Section 20.3.Common Criteria for Information Technology Security Evaluation Section 20.4.Recommended Reading and Web Sites Section 20.5.Key Terms.Review Questions.and Problems Appendix A.Standards and Standards-Setting Organizations Section A.1.The Importance of Standards Section A.2.Internet Standards and the Internet Society Section A.3.National Institute of Standards and Technology Appendix B.Projects for Teaching Cryptography and Network Security Section B.1.Research Projects 54 Section B.2.Programming Projects 6 Section B.3.Laboratory Exercises Section B.4.Writing Assignments Section B.5.Reading/Report Assignments Glossary 657 References 663 Abbreviations 663 Inside Front Cover InsideFrontCover Inside Back Cover InsideBackCover Index ◆PREY NEXT◆
Section 16.5. Combining Security Associations 503 Section 16.6. Key Management 506 Section 16.7. Recommended Reading and Web Site 516 Section 16.8. Key Terms, Review Questions, and Problems 517 Appendix 16A Internetworking and Internet Protocols 518 Chapter 17. Web Security 527 Section 17.1. Web Security Considerations 528 Section 17.2. Secure Socket Layer and Transport Layer Security 531 Section 17.3. Secure Electronic Transaction 549 Section 17.4. Recommended Reading and Web Sites 560 Section 17.5. Key Terms, Review Questions, and Problems 561 Part Four: System Security 563 Chapter 18. Intruders 565 Section 18.1. Intruders 567 Section 18.2. Intrusion Detection 570 Section 18.3. Password Management 582 Section 18.4. Recommended Reading and Web Sites 591 Section 18.5. Key Terms, Review Questions, and Problems 592 Appendix 18A The Base-Rate Fallacy 594 Chapter 19. Malicious Software 598 Section 19.1. Viruses and Related Threats 599 Section 19.2. Virus Countermeasures 610 Section 19.3. Distributed Denial of Service Attacks 614 Section 19.4. Recommended Reading and Web Sites 619 Section 19.5. Key Terms, Review Questions, and Problems 620 Chapter 20. Firewalls 621 Section 20.1. Firewall Design Principles 622 Section 20.2. Trusted Systems 634 Section 20.3. Common Criteria for Information Technology Security Evaluation 640 Section 20.4. Recommended Reading and Web Sites 644 Section 20.5. Key Terms, Review Questions, and Problems 645 Appendix A. Standards and Standards-Setting Organizations 647 Section A.1. The Importance of Standards 648 Section A.2. Internet Standards and the Internet Society 649 Section A.3. National Institute of Standards and Technology 652 Appendix B. Projects for Teaching Cryptography and Network Security 653 Section B.1. Research Projects 654 Section B.2. Programming Projects 655 Section B.3. Laboratory Exercises 655 Section B.4. Writing Assignments 655 Section B.5. Reading/Report Assignments 656 Glossary 657 References 663 Abbreviations 663 Inside Front Cover InsideFrontCover Inside Back Cover InsideBackCover Index
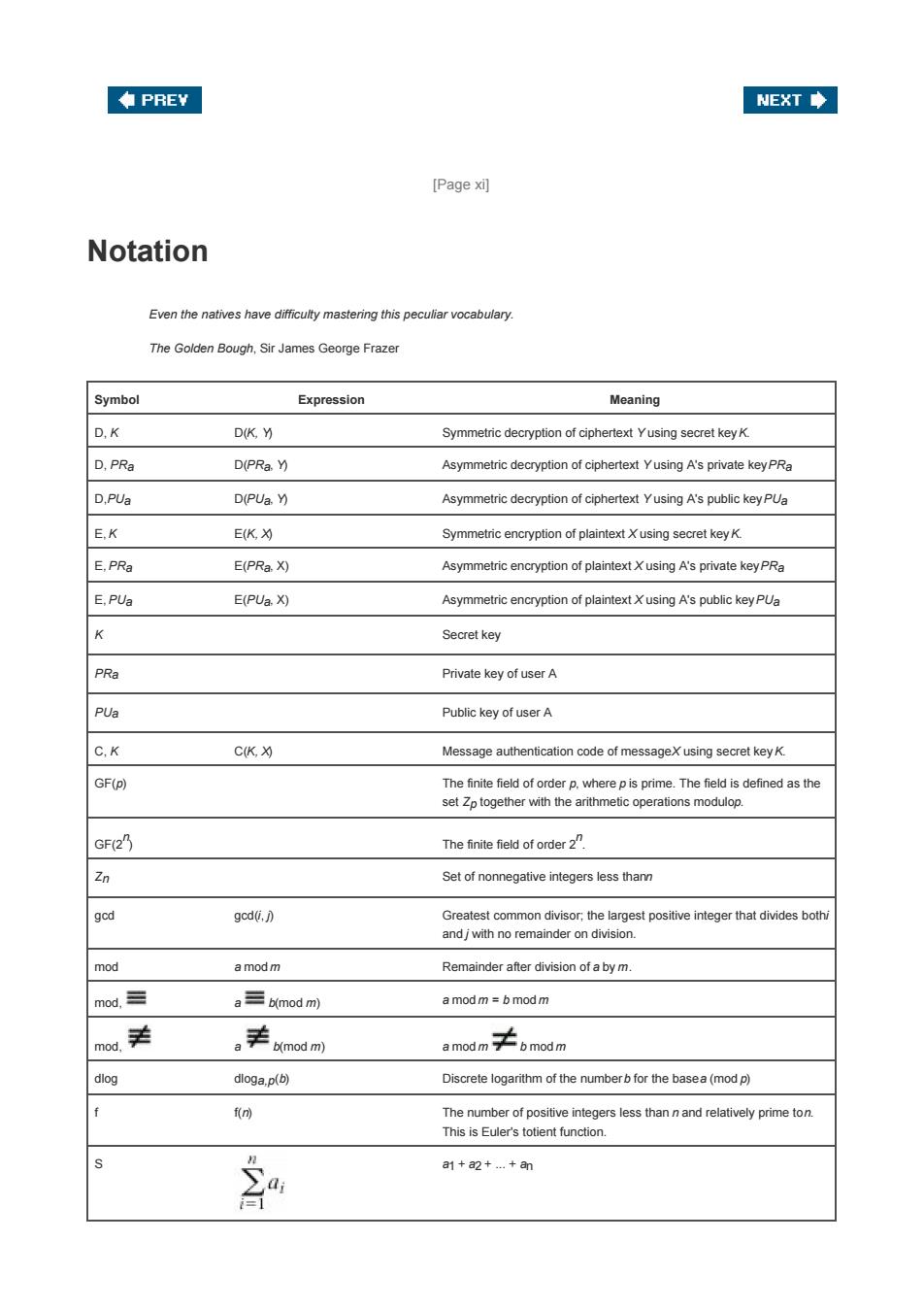
◆PREY NEXT◆ [Page x刈 Notation Even the natives have difficulty mastering this peculiar vocabulary. The Golden Bough,Sir James George Frazer Symbol Expression Meaning D,K D(K,Y) Symmetric decryption of ciphertext Yusing secret key K. D,PRa D(PRa.Y) Asymmetric decryption of ciphertext Yusing A's private key PRa D,PUa D(PUa.Y) Asymmetric decryption of ciphertext Yusing A's public key PUa E,K E(K,9 Symmetric encryption of plaintext X using secret key K. E.PRa E(PRa.X) Asymmetric encryption of plaintext X using A's private key PRa E,PUa E(PUa.X) Asymmetric encryption of plaintext X using A's public key PUa K Secret key PRa Private key of user A PUa Public key of user A C.K C(K,X) Message authentication code of messageX using secret key K. GF(p) The finite field of order p.where p is prime.The field is defined as the set Zp together with the arithmetic operations modulop. GF(2 The finite field of order2 Zn Set of nonnegative integers less thann gcd gcd〔,) Greatest common divisor;the largest positive integer that divides bothi and jwith no remainder on division. mod amodm Remainder after division of a by m. mod,≡ a三b(mod m) a mod m b mod m mog美 ,丰kmo8m a mod m≠6mdnm dlog dloga.p(b) Discrete logarithm of the numberb for the basea(mod p) f f The number of positive integers less than n and relatively prime ton. This is Euler's totient function. 和 a1+a2+.+an
[Page xi] Notation Even the natives have difficulty mastering this peculiar vocabulary. The Golden Bough, Sir James George Frazer Symbol Expression Meaning D, K D(K, Y) Symmetric decryption of ciphertext Y using secret key K. D, PRa D(PRa, Y) Asymmetric decryption of ciphertext Y using A's private key PRa D,PUa D(PUa, Y) Asymmetric decryption of ciphertext Y using A's public key PUa E, K E(K, X) Symmetric encryption of plaintext X using secret key K. E, PRa E(PRa, X) Asymmetric encryption of plaintext X using A's private key PRa E, PUa E(PUa, X) Asymmetric encryption of plaintext X using A's public key PUa K Secret key PRa Private key of user A PUa Public key of user A C, K C(K, X) Message authentication code of message X using secret key K. GF(p) The finite field of order p, where p is prime. The field is defined as the set Zp together with the arithmetic operations modulo p. GF(2 n ) The finite field of order 2 n . Zn Set of nonnegative integers less than n gcd gcd(i, j) Greatest common divisor; the largest positive integer that divides both i and j with no remainder on division. mod a mod m Remainder after division of a by m. mod, a b(mod m) a mod m = b mod m mod, a b(mod m) a mod m b mod m dlog dloga,p(b) Discrete logarithm of the number b for the base a (mod p) f f(n) The number of positive integers less than n and relatively prime to n. This is Euler's totient function. S a1 + a2 + ... + an

Symbol Expression Meaning Π a1 x a2x ..x an a =1 v i divides j,which means that there is no remainder wheny is divided byi 间 Absolute value of a X x concatenated with y 之 ≈, x is approximately equal toy ⊕ ⊕, Exclusive-OR of x and y for single-bit variables;Bitwise exclusive-OR of x and y for multiple-bit variables J L The largest integer less than or equal tox xEs The elementx is contained in the set S. ←→ A←→(a1,a2,…a The integer A corresponds to the sequence of integers e1,a2....,ak) 中PREY NEXT◆
Symbol Expression Meaning a1 x a2 x ... x an | i|j i divides j, which means that there is no remainder when j is divided by i |,| |a| Absolute value of a || x||y x concatenated with y x y x is approximately equal to y x y Exclusive-OR of x and y for single-bit variables; Bitwise exclusive-OR of x and y for multiple-bit variables , x The largest integer less than or equal to x x S The element x is contained in the set S. A (a1,a2, ...,ak) The integer A corresponds to the sequence of integers (a1,a2, ...,ak)
◆PREY NEXT◆ [Page xii] Preface "The tie,if I might suggest it.sir,a shade more tightly knotted.One aims at the perfect butterfly effect.If you will permit me" "What does it matter,Jeeves,at a time like this?Do you realize that Mr.Little's domestic happiness is hanging in the scale?" "There is no time.sir,at which ties do not matter." Very Good,Jeeves!P.G.Wodehouse In this age of universal electronic connectivity.of viruses and hackers,of electronic eavesdropping and electronic fraud,there is indeed no time at which security does not matter.Two trends have come together to make the topic of this book of vital interest.First,the explosive growth in computer systems and their interconnections via networks has increased the dependence of both organizations and individuals on the information stored and communicated using these systems.This,in turn,has led to a heightened awareness of the need to protect data and resources from disclosure,to guarantee the authenticity of data and messages,and to protect systems from network-based attacks.Second,the disciplines of cryptography and network security have matured,leading to the development of practical,readily available applications to enforce network security. ◆PREY NEXT◆
[Page xiii] Preface "The tie, if I might suggest it, sir, a shade more tightly knotted. One aims at the perfect butterfly effect. If you will permit me" "What does it matter, Jeeves, at a time like this? Do you realize that Mr. Little's domestic happiness is hanging in the scale?" "There is no time, sir, at which ties do not matter." Very Good, Jeeves! P. G. Wodehouse In this age of universal electronic connectivity, of viruses and hackers, of electronic eavesdropping and electronic fraud, there is indeed no time at which security does not matter. Two trends have come together to make the topic of this book of vital interest. First, the explosive growth in computer systems and their interconnections via networks has increased the dependence of both organizations and individuals on the information stored and communicated using these systems. This, in turn, has led to a heightened awareness of the need to protect data and resources from disclosure, to guarantee the authenticity of data and messages, and to protect systems from network-based attacks. Second, the disciplines of cryptography and network security have matured, leading to the development of practical, readily available applications to enforce network security

◆PREY NEXT◆ [Page xii(continued)] Objectives It is the purpose of this book to provide a practical survey of both the principles and practice of cryptography and network security.In the first two parts of the book,the basic issues to be addressed by a network security capability are explored by providing a tutorial and survey of cryptography and network security technology.The latter part of the book deals with the practice of network security:practical applications that have been implemented and are in use to provide network security. The subject,and therefore this book,draws on a variety of disciplines.In particular,it is impossible to appreciate the significance of some of the techniques discussed in this book without a basic understanding of number theory and some results from probability theory. Nevertheless,an attempt has been made to make the book self-contained.The book presents not only the basic mathematical results that are needed but provides the reader with an intuitive understanding of those results.Such background material is introduced as needed.This approach helps to motivate the material that is introduced,and the author considers this preferable to simply presenting all of the mathematical material in a lump at the beginning of the book. ◆ ◆PREY NEXT◆
[Page xiii (continued)] Objectives It is the purpose of this book to provide a practical survey of both the principles and practice of cryptography and network security. In the first two parts of the book, the basic issues to be addressed by a network security capability are explored by providing a tutorial and survey of cryptography and network security technology. The latter part of the book deals with the practice of network security: practical applications that have been implemented and are in use to provide network security. The subject, and therefore this book, draws on a variety of disciplines. In particular, it is impossible to appreciate the significance of some of the techniques discussed in this book without a basic understanding of number theory and some results from probability theory. Nevertheless, an attempt has been made to make the book self-contained. The book presents not only the basic mathematical results that are needed but provides the reader with an intuitive understanding of those results. Such background material is introduced as needed. This approach helps to motivate the material that is introduced, and the author considers this preferable to simply presenting all of the mathematical material in a lump at the beginning of the book