计算机问题求解一论题4-4 密码算法 2017年04月05日
计算机问题求解 – 论题4-4 - 密码算法 2017年04月05日

问题1: Cryptosystem是什么意 思?它要解决的基本问题 是什么?
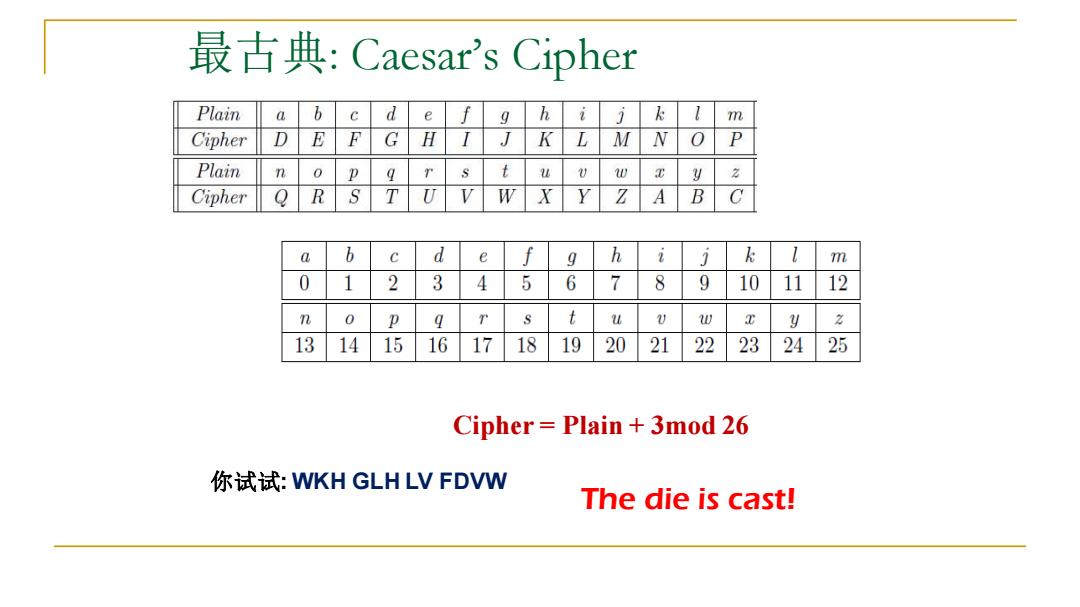
最古典:Caesar's Cipher Plain b c d e h n Cipher D E F G H K L M P Plain n 0 p t U 0 2 Cipher Q R S T U X Z A B C a b d e h i k m 0 1 2 3 4 5 6 7 8 9 10 11 12 n 0 P 9 u U w E y 13 14 15 1617 18 19 20 21 22 23 2425 Cipher Plain +3mod 26 你试试:NKH GLH LV FDVW The die is cast!
最古典: Caesar’s Cipher Cipher = Plain + 3mod 26 你试试: WKH GLH LV FDVW The die is cast!

问题2: 你能不能用数学概念来描述 加密和解密?
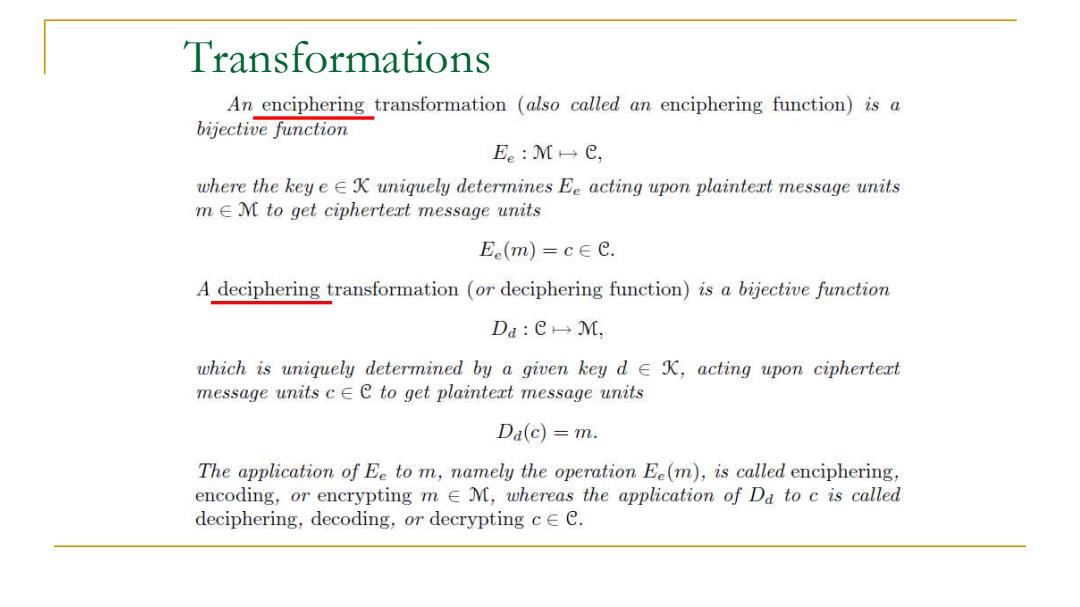
Transformations An enciphering transformation (also called an enciphering function)is a bijective function Ee:M→e, where the key eE K uniquely determines Ee acting upon plaintert message units m E M to get ciphertert message units Ee(m)=c∈C. A deciphering transformation (or deciphering function)is a bijective function Da:CM, which is uniquely determined by a given key d E K,acting upon ciphertert message units c Ee to get plaintert message units Da(c)=m. The application of Ee to m,namely the operation Ee(m),is called enciphering, encoding,or encrypting m EM,whereas the application of Da to c is called deciphering,decoding,or decrypting ceC
Transformations

Cryptosystem A cryptosystem is composed of a set (Ee:eEX} consisting of enciphering transformations and the corresponding set (Ee:eeX)={Da:deX) of deciphering transformations.In other words,for eacheK,there erists a unique dK such that Da=E,so that Da(Ee(m))=m for all mM. The keys (e,d)are called a key pair where possibly e=d.A cryptosystem is also called a cipher
Cryptosystem
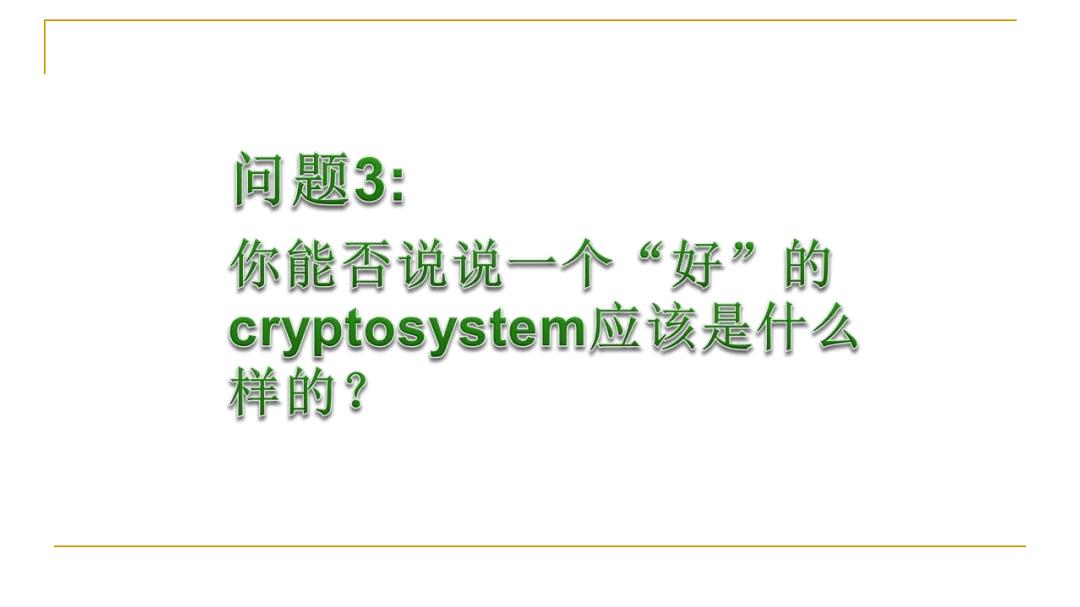
间题3: 你能香说说一个“好”的 cryptosystem应该是什么 样的?

Kerckhoffs'Rules for Field Ciphers 1.The cryptosystem should be practically unbreakable (breakable in theory, perhaps,but not in practice). 2.A compromised cryptosystem should not inconvenience the correspondents. (This is the one from which his principle,displayed on page 96,seems to be derived since it says that the enemy may know the cryptosystem,but one should still be able to send messages since the enemy cannot cryptanalyze with this knowledge and without the key.) 3.The key should be easy to both remember and change at will. 4.Cryptosystems must be amenable to being sent by telegraph. 5.The mechanisms of the cryptosystem must be easily portable and entirely operable by a single entity. 6.The cryptosystem must be easy to use without reference to any manuals or the need for deep mental effort
问题4: 所谓“key”究竟是什么? 问题5: 所谓公开秘钥加密和私有秘 钥加密有什么区别?

古典密码:德国陆军强于恺撒 The German ADFGVX Field Cipher A D G X Plaintext:field cipher A B 3 R D ↓ F E H DF AX FG AV GF FA AX VX FX FG AG G R F L E X D F A X X A G F X F 你试试: X F G V XFVAXAFFGXFFGXFXFXXGDXDAFGVA G F G D A V X X X X A F F
古典密码:德国陆军强于恺撒 Plaintext: field cipher key 你试试: R I F L E D F A X X A G F X F F X F G V G F G D A V X X X X A F F